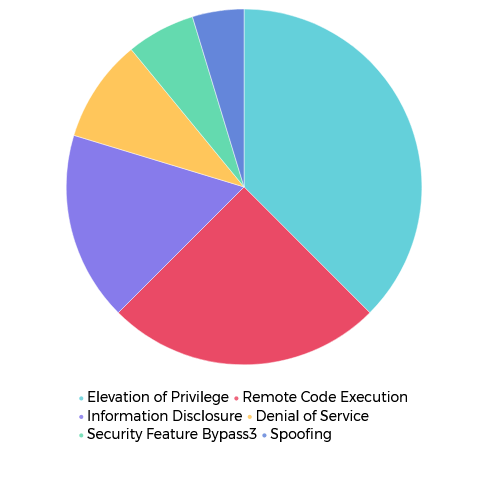
Microsoft has released patches for 65 vulnerabilities in its Microsoft November Patch Tuesday of which 6 are actively exploited Zero-Day. Among the 6 Zero-day, CVE-2022-41091 vulnerability is publicly disclosed. Eleven of the 65 vulnerabilities fixed in this security update are classified as ‘Critical’ as they allow privilege elevation, spoofing, or remote code execution, and the rest as ‘Important’. Moreover, with the correct patch management tool, you can easily detect and remediate this instantly.
In Microsoft November Patch Tuesday the 6 Zero-Day vulnerabilities include Microsoft Exchange Server (CVE-2022-41082, CVE-2022-41040), Windows CNG Key Isolation Service (CVE-2022-41125), Windows Print Spooler (CVE-2022-41073), Windows Scripting Languages (CVE-2022-41128), Windows Mark of the Web Security (CVE-2022-41091).

Zero-day Vulnerabilities
Microsoft November Patch Tuesday 2022 fixed zero-day vulnerabilities like:
CVE-2022-41082, CVE-2022-41040 – Microsoft Exchange Server Remote Code Execution and Elevation of Privilege Vulnerability. An authenticated attacker could attempt to trigger malicious code in the context of the server’s account through a network call. These vulnerabilities were disclosed in late September by Vietnamese cybersecurity firm GTSC, who first spotted the flaws used in attacks. Thus, successfully exploiting the vulnerability could allow authenticated attackers to perform remote code execution with elevated privileges.
CVE-2022-41125 – Windows CNG Key Isolation Service Elevation of Privilege Vulnerability. Successful exploitation of this vulnerability could allow the attacker to gain SYSTEM privileges.
Furthermore Microsoft November Patch Tuesday 2022 also covered:
CVE-2022-41073 – Windows Print Spooler Elevation of Privilege Vulnerability. Successful exploitation of this vulnerability could allow the attacker to gain SYSTEM privileges.
CVE-2022-41128 – Windows Scripting Languages Remote Code Execution Vulnerability. The JScript9 scripting language, a component of the Scripting Language, is vulnerable to this flaw. The victim must interact with the attacker for it to succeed. Successful exploitation of the vulnerability could allow attackers to perform remote code execution.
CVE-2022-41091 – Windows Mark of the Web Security Feature Bypass Vulnerability. The vulnerability is being exploited in the wild and exploitation of the vulnerability is publicly available. A malicious actor could craft a file that could bypass MoTW “resulting in a limited loss of integrity and availability of security features such as Protected View.”
Therefore Microsoft November Patch Tuesday addressed the above vulnerabilities. Patch Management Software can prove to be of great use to prevent these attacks from occurring.
List of Critical Vulnerabilities in Microsoft November Patch Tuesday 2022
| Tag | CVE ID | CVE Title | Severity |
|---|---|---|---|
| Windows Point-to-Point Tunneling Protocol | CVE-2022-41039 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability | Critical |
| Windows Point-to-Point Tunneling Protocol | CVE-2022-41088 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability | Critical |
| Windows Kerberos RC4-HMAC | CVE-2022-37966 | Windows Kerberos RC4-HMAC Elevation of Privilege Vulnerability | Critical |
| Windows Hyper-V | CVE-2022-38015 | Windows Hyper-V Denial of Service Vulnerability | Critical |
| Windows Kerberos | CVE-2022-37967 | Windows Kerberos Elevation of Privilege Vulnerability | Critical |
| Windows Scripting Languages | CVE-2022-41128 | Windows Scripting Languages Remote Code Execution Vulnerability | Critical |
| Microsoft Exchange Server | CVE-2022-41080 | Microsoft Exchange Server Elevation of Privilege Vulnerability | Critical |
| Windows Scripting Languages | CVE-2022-41118 | Windows Scripting Languages Remote Code Execution Vulnerability | Critical |
| Azure CLI | CVE-2022-39327 | GitHub Improper Control of Generation of Code (‘Code Injection’) in Azure CLI | Critical |
| Windows Point-to-Point Tunneling Protocol | CVE-2022-41044 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability | Critical |
Microsoft November Patch Tuesday 2022 security bulletin summary
- NET Framework
- AMD CPU Branch
- Azure
- Azure Real Time Operating System
- Linux Kernel
- Microsoft Dynamics
- Microsoft Exchange Server
- Microsoft Graphics Component
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office SharePoint
- Microsoft Office Word
- Network Policy Server (NPS)
- Open Source Software
- Role: Windows Hyper-V
- SysInternals
- Visual Studio
- Windows Advanced Local Procedure Call
- Windows ALPC
- Windows Bind Filter Driver
- Windows BitLocker
- Windows CNG Key Isolation Service
- Windows Devices Human Interface
- Windows Digital Media
- Windows DWM Core Library
- Windows Extensible File Allocation
- Windows Group Policy Preference Client
- Windows HTTP.sys
- Windows Kerberos
- Windows Mark of the Web (MOTW)
- Windows Netlogon
- Windows Network Address Translation (NAT)
- Windows ODBC Driver
- Windows Overlay Filter
- Windows Point-to-Point Tunneling Protocol
- Windows Print Spooler Components
- Windows Resilient File System (ReFS)
- Windows Scripting
- Windows Win32K
Product: Microsoft Windows.
CVEs/Advisory: CVE-2022-23824, CVE-2022-37966, CVE-2022-37967, CVE-2022-37992, CVE-2022-38014, CVE-2022-38015, CVE-2022-38023, CVE-2022-41039, CVE-2022-41044, CVE-2022-41045, CVE-2022-41047, CVE-2022-41048, CVE-2022-41049, CVE-2022-41050, CVE-2022-41052, CVE-2022-41053, CVE-2022-41054, CVE-2022-41055, CVE-2022-41056, CVE-2022-41057, CVE-2022-41058, CVE-2022-41060, CVE-2022-41061, CVE-2022-41073, CVE-2022-41086, CVE-2022-41088, CVE-2022-41090, CVE-2022-41091, CVE-2022-41092, CVE-2022-41093, CVE-2022-41095, CVE-2022-41096, CVE-2022-41097, CVE-2022-41098, CVE-2022-41099, CVE-2022-41100, CVE-2022-41101, CVE-2022-41102, CVE-2022-41103, CVE-2022-41109, CVE-2022-41113, CVE-2022-41114, CVE-2022-41116, CVE-2022-41118, CVE-2022-41120, CVE-2022-41125, CVE-2022-41128.
Impact: Denial of Service, Elevation of Privilege, Information Disclosure, Remote Code Execution, Security Feature Bypass.
KB’s: 5002291, 5019080, 5019081, 5019958, 5019959, 5019961, 5019964, 5019966, 5019970, 5019980, 5020000, 5020003, 5020005, 5020009, 5020010, 5020013, 5020019, 5020023.
Product: Microsoft Azure.
CVE/Advisory: CVE-2022-30175, CVE-2022-38014, CVE-2022-39327, CVE-2022-41051, CVE-2022-41085.
Impact: Remote Code Execution, Elevation of Privilege.
Product: Microsoft Office.
CVE/Advisory: CVE-2022-41060, CVE-2022-41061, CVE-2022-41063, CVE-2022-41066, CVE-2022-41103, CVE-2022-41104, CVE-2022-41105, CVE-2022-41106, CVE-2022-41107.
Impact: Information Disclosure, Remote Code Execution, Security Feature Bypass, Defense in Depth.
KB’s: 3191869, 3191875, 5002217, 5002223, 5002253, 5002261, 5002275, 5002276, 5021002.
These are the critical CVEs covered in Microsoft November Patch Tuesday 2022. Try out SanerNow VM and SanerNow PM to detect and automatically fix these vulnerabilities by applying security updates. Therefore Use SanerNow and keep your systems updated and secure.