A critical and wormable 17 years-old vulnerability (CVE-2020-1350) has been discovered in Microsoft Windows DNS Servers which can allow an attacker to run arbitrary code on the vulnerable system. The vulnerability is identified as CVE-2020-1350 and resides in the way how DNS Server parses incoming query or a response for a forwarded request. This vulnerability has been named ‘SIGRed‘ and has received the highest severity score of 10.0. It affects all Windows Servers ranging from version 2003 to 2019. A vulnerability management tool helps detect these kinds of vulnerabilities.
Vulnerability (CVE-2020-1350) Details:
Domain Name System (DNS) Servers are one of the core components of the internet, which plays a significant role in domain-name-to-IP address mapping. Microsoft Windows DNS Server is the Microsoft implementation of the DNS server and is present in all Microsoft Windows Server platforms. The Domain Name System (DNS) is a hierarchical and decentralized model. Worldwide, at the top of the hierarchy, there are 13 root DNS servers that have all the information. When a DNS server doesn’t know the answer to a query it receives, the query is forwarded to a DNS server above it in the hierarchy. CVE-2020-1350 vulnerability exists in the way the DNS server parses this response (answer) for a forwarded query. However utilizing a patch management software is critical here.
The executable responsible for answering DNS queries on Microsoft Windows Server is “dns.exe“. This executable includes various parsing functions for various supported DNS record types. One of these record types is the signature record type, referred to as SIG. The dns.exe function expects a SIG record of size, not more than 64KB. A SIG response of size greater than 64KB leads to integer overflow resulting in a heap-based buffer overflow. Although a single DNS message is limited to 512 bytes or 4,096 bytes if the server supports EDNS0 (Extension Mechanisms for DNS 0). CVE-2020-1350 hurdle can overcome by using compression for DNS names and squeeze as much information as possible. Once a DNS Server receives a malicious SIG response, it leads to buffer overflow allowing users to execute arbitrary code on the affected system.
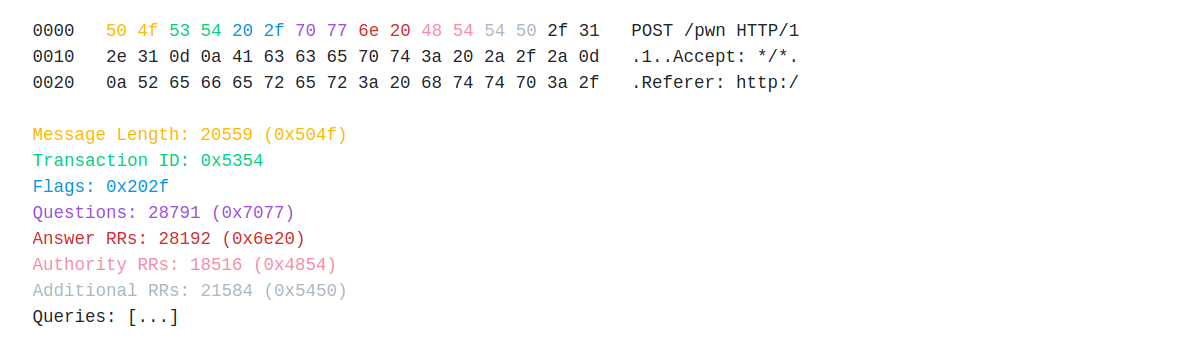
DNS can transport over TCP and Windows DNS Server supports this. An HTTP request sent to DNS Server on port 53 causes the Windows DNS Server to interpret this payload as if it was a DNS query. Here is an example.
More details on CVE-2020-1350:
This bug can trigger remotely too. Microsoft Windows DNS Servers support for both ‘Connection Reuse’ and ‘Pipelining’, which allows sending multiple queries over a single TCP session without waiting for replies. These features when combined allow sending HTTP POST requests with binary data, with another DNS query in the POST data to process separately. This is possible even in browsers, such as Internet Explorer and Microsoft Edge that allow requests to port 53 used by the DNS. Google Chrome and Mozilla Firefox do not allow HTTP requests to this port.
As per researchers to have the target Windows DNS Server parse responses from malicious DNS Nameserver, then follow this:
- Configure used domains (e.g deadexample.go) NS Records to point at malicious DNS Server.
- Query the victim Windows DNS Server for NS Records of deadexample.go
- The victim DNS, not yet knowing the answer for this query, forwards the query to the DNS server above it.
- The authoritative server knows the answer, and then responds with the Nameserver of deadexample.go
- The victim Windows DNS Server processes and caches this response.
- The next time there is a query for a subdomain of deadexample.go, the target Windows DNS Server will also query Nameserver (received earlier from authoritative) for its response.
Impact
An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the Local System Account.
Affected Products by CVE-2020-1350
Affects all Microsoft Windows Servers with DNS Server implementation.
- Windows Server 2019
- Windows Server 2019 (Server Core installation)
- Windows Server, version 1909 (Server Core installation)
- Windows Server, version 1903 (Server Core installation)
- Windows Server, version 2004 (Server Core installation)
- Windows Server 2016
- Windows Server 2016 (Server Core installation)
- Windows Server 2008 Service Pack 2 32-bit/64-bit Systems
- Windows Server 2008 Service Pack 2 (Server Core installation) 32-bit/64-bit Systems
- Windows Server 2008 R2 Service Pack 1 x64-based Systems
- Windows Server 2008 R2 Service Pack 1 (Server Core installation) x64-based Systems
- Windows Server 2012
- Windows Server 2012 (Server Core installation)
- Windows Server 2012 R2
- Windows Server 2012 R2 (Server Core installation)
Workaround
NOTE: This is a temporary workaround and you apply patches at the earliest.
Moreover, the maximum length of a DNS message (over TCP) set to ‘0xFF00’ to eliminate the chances of a buffer overflow. The registry modification for the workaround as shown below.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters
DWORD = TcpReceivePacketSize
Value = 0xFF00
Note: A restart of the DNS Service is to take effect.
Solution to CVE-2020-1350
Microsoft has released a security fix in its monthly Patch Tuesday updates for July 2020.
However, SanerNow security content has published to detect and mitigate these vulnerabilities. We strongly recommend applying the security updates as soon as possible following the instructions published in our article, which is now replaced by support article .

Nice blog author. Thank you. Keep it up.