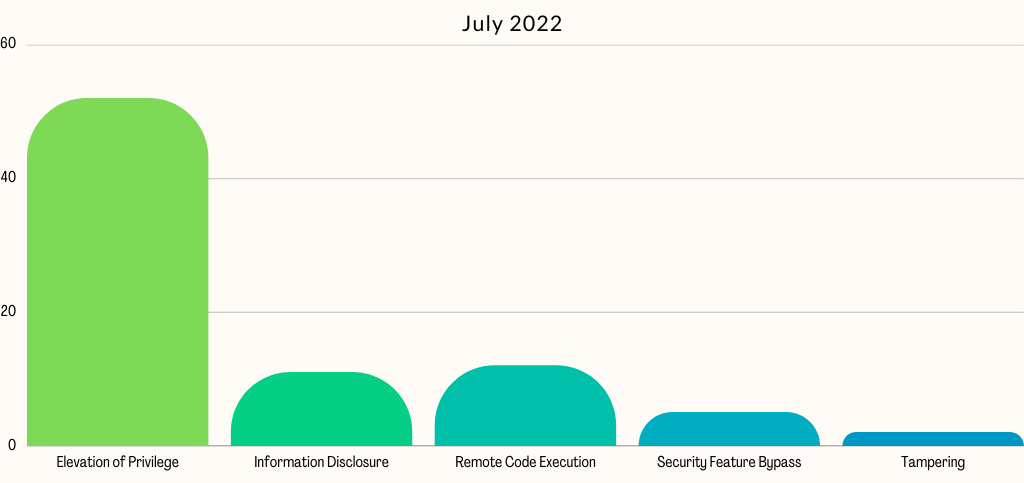
Microsoft fixes 84 vulnerabilities, including four critical, one zero-day, and 79 others as important in its July 2022 Patch Tuesday update. All four critical vulnerabilities are of remote code execution, and there are about 12. The rest include elevation of privileges (zero-day flaw), Information Disclosure, Denial of Service, and Security Feature Bypass. These vulnerabilities can be prevented by using a vulnerability management software. The vulnerabilities distribution graph is provided below for better reference.
The fixed zero-day flaw is an elevation of privileges found in CSRSS (Client Server Runtime Subsystem). Microsoft stated that the vulnerability is not publicly disclosed but is known to be actively exploited. Other products fixed in this PT include RDP client for Windows, Windows BitLocker, Windows kernel, Windows IIS, Windows NFS, Microsoft Office, Skype for Business, etc. Deploying these important patches can be simplified with the help of a good patch management software.
Zero-day Vulnerabilities
CVE-2022-22047 – Windows CSRSS (Client Server Runtime Subsystem) Elevation of Privilege Vulnerability. An attacker can gain SYSTEM privileges by successfully exploiting this vulnerability. Microsoft has not been informed on where or how widely it is being exploited.
Critical Vulnerabilities
In its July 2022 Patch Tuesday update, Microsoft fixed these critical vulnerabilties.
CVE-2022-22039 – Windows Network File System Remote Code Execution Vulnerability. An attacker can exploit this vulnerability over the network by making an unauthenticated, specially crafted call to a Network File System (NFS) service, which can result in Remote Code Execution (RCE). Microsoft said, “Successful exploitation of this vulnerability requires an attacker to win a race condition.”
CVE-2022-22038 – Remote Procedure Call Runtime Remote Code Execution Vulnerability. An attacker must invest time in repeated exploitation attempts by sending constant or intermittent data. A successful attack will allow remote users to execute commands remotely.
CVE-2022-22029 – Windows Network File System Remote Code Execution Vulnerability. Like the above vulnerability, an attacker must make multiple attempts with a specially crafted request to a Network File System (NFS) service to trigger a Remote Code Execution (RCE).
CVE-2022-30221 – Windows Graphics Component Remote Code Execution Vulnerability. An attacker must persuade a targeted user to connect to a malicious RDP server. Upon connecting, the malicious server could execute code on the victim’s system in the context of the targeted user.
Microsoft security bulletin summary for March 2022
- Azure Site Recovery
- Azure Storage Library
- Microsoft Defender for Endpoint
- Microsoft Edge (Chromium-based)
- Microsoft Graphics Component
- Microsoft Office
- Open Source Software
- Windows Active Directory
- Windows Advanced Local Procedure Call
- Windows BitLocker
- Windows Boot Manager
- Windows Client/Server Runtime Subsystem
- Windows Connected Devices Platform Service
- Windows Credential Guard
- Windows Fast FAT Driver
- Windows Fax and Scan Service
- Windows Group Policy
- Windows IIS
- Windows Kernel
- Windows Media
- Windows Network File System
- Windows Performance Counters
- Windows Point-to-Point Tunneling Protocol
- Windows Portable Device Enumerator Service
- Windows Print Spooler Components
- Windows Remote Procedure Call Runtime
- Windows Security Account Manager
- Windows Server Service
- Windows Shell
- Windows Storage
- Xbox
Product: Microsoft Windows.
CVEs/Advisory: CVE-2022-22043, CVE-2022-22040, CVE-2022-22025, CVE-2022-30225, CVE-2022-30208, CVE-2022-22047, CVE-2022-22050, CVE-2022-22049, CVE-2022-22045, CVE-2022-22041, CVE-2022-22037, CVE-2022-22036, CVE-2022-22034, CVE-2022-22031, CVE-2022-22026, CVE-2022-22022, CVE-2022-30226, CVE-2022-30224, CVE-2022-30220, CVE-2022-30215, CVE-2022-30209, CVE-2022-30206, CVE-2022-30205, CVE-2022-30202, CVE-2022-33644, CVE-2022-23825, CVE-2022-23816, CVE-2022-27776, CVE-2022-22042, CVE-2022-22028, CVE-2022-30223, CVE-2022-30213, CVE-2022-30212, CVE-2022-22711, CVE-2022-21845, CVE-2022-22039, CVE-2022-22038, CVE-2022-22029, CVE-2022-22027, CVE-2022-22024, CVE-2022-30222, CVE-2022-30214, CVE-2022-30211, CVE-2022-30221, CVE-2022-22048, CVE-2022-22023, CVE-2022-30203, CVE-2022-30216
Impact: Denial of Service, Elevation of Privilege, Information Disclosure, Remote Code Execution, Security Feature Bypass, Tampering
KB’s: 5015874, 5015877, 5015863, 5015875, 5015808, 5015832, 5015807, 5015814, 5015827, 5015811, 5015861, 5015862, 5015866, 5015870
Product: Microsoft Azure
CVE/Advisory: CVE-2022-33672, CVE-2022-33671, CVE-2022-33669, CVE-2022-33668, CVE-2022-33667, CVE-2022-33666, CVE-2022-33665, CVE-2022-33664, CVE-2022-33663, CVE-2022-33662, CVE-2022-33661, CVE-2022-33660, CVE-2022-33659, CVE-2022-33658, CVE-2022-33657, CVE-2022-33656, CVE-2022-33655, CVE-2022-33654, CVE-2022-33653, CVE-2022-33652, CVE-2022-33651, CVE-2022-33650, CVE-2022-33643, CVE-2022-33642, CVE-2022-33677, CVE-2022-33675, CVE-2022-33674, CVE-2022-33673, CVE-2022-33641, CVE-2022-30181, CVE-2022-30187, CVE-2022-33678, CVE-2022-33676
Impact: Elevation of Privilege, Information Disclosure, Remote Code Execution
Product: Microsoft Office
CVE/Advisory: CVE-2022-33632
Impact: Security Feature Bypass
KB: 5002112
SanerNow VM and SanerNow PM detect and automatically fix these vulnerabilities by applying security updates. Use SanerNow and keep your systems updated and secure.

