Microsoft released its May edition of Patch Tuesday, in which 61 vulnerabilities and three actively exploited zero days were addressed. Of the 61 vulnerabilities, 59 fall under the Important severity, while one each in the Moderate and Critical severity.
Microsoft has patched the below-mentioned three zero-day vulnerabilities. You can find the details for each of these zero-day vulnerabilities below.
CVE-2024-30040 (CVSS score: 8.8) – Windows MSHTML Platform Security Feature Bypass Vulnerability.
This vulnerability bypasses OLE mitigations in Microsoft 365 and Microsoft Office, which protects users from vulnerable COM /OLE controls.
An attacker would have to convince the user to load a malicious file onto a vulnerable system, typically through an enticement in an Email or Instant Messenger message, and then convince the user to manipulate the specially crafted file but not necessarily click or open the malicious file.
An unauthenticated attacker who successfully exploited this vulnerability could gain code execution by convincing a user to open a malicious document, at which point the attacker could execute arbitrary code in the user’s context.
CVE-2024-30051 (CVSS score: 7.8) – Windows DWM Core Library Elevation of Privilege Vulnerability.
An attacker exploiting this vulnerability could execute arbitrary code with elevated privileges, enabling them to install programs, view/change/delete data, or create new accounts with full user rights on the compromised system.
This vulnerability is actively exploited by Qakbot malware and other threat actors to compromise Windows systems.
CVE-2024-30044 (CVSS score: 8.8) – Windows Sharepoint Server Remote Code Execution Vulnerability.
An authenticated attacker with Site Powner permission can exploit the vulnerability to inject arbitrary code and execute it in the context of Sharepoint Server.
An authenticated attacker with Site Owner permissions or higher could upload a specially crafted file to the targeted SharePoint Server and craft specialized API requests to trigger the deserialization of the file’s parameters. This would enable the attacker to perform remote code execution in the context of the SharePoint Server.
We recommend that you patch these vulnerabilities using SanerNow as soon as possible to secure your devices and prevent attacks on your organization.
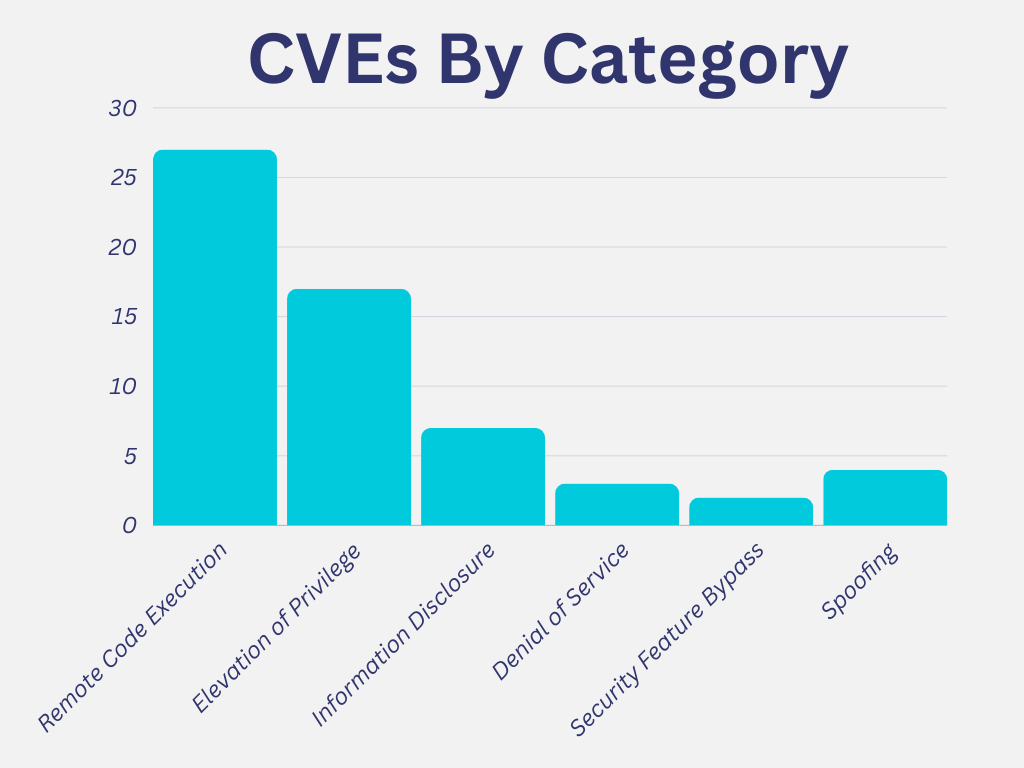
In May, Patch Tuesday saw the highest number of vulnerabilities belonging to the Remote Code Execution category, followed by the Elevation of Privilege category and the Information Disclosure category.

Microsoft Security Bulletin Summary for May 2024
Microsoft released security updates for the following products in the May patch tuesday release.
- Azure Migrate
- Windows Mobile Broadband
- Windows Common Log File System Driver
- Windows DWM Core Library
- Windows Routing and Remote Access Service (RRAS)
- Windows Hyper-V
- Windows Cryptographic Services
- Windows Kernel
- Windows DHCP Server
- Windows Mark of the Web (MOTW)
- Windows Task Scheduler
- Windows Win32K – ICOMP
- Windows Win 32K – GRFX
- Windows CNG Key Isolation Service
- Windows Cloud Files Mini Filter Driver
- Windows Deployment Services
- Windows Remote Access Connection Manager
- Windows MSHTML Platform
- Microsoft Intune
- Microsoft Windows Search Component
- Microsoft Edge (Chromium-based)
- Microsoft Windows SCSI Class System File
- Microsoft Dynamics 365 Customer Insights
- Microsoft Bing
- Microsoft Office Excel
- Visual Studio
- Microsoft WDAC OLE DB provider for SQL
- Microsoft Brokering File System
- Microsoft Office SharePoint
- .NET and Visual Studio
SanerNow vulnerability management and SanerNow patch management detects and automatically fixes these vulnerabilities mentioned above by applying security updates. Use SanerNow to keep your systems updated and secure.


