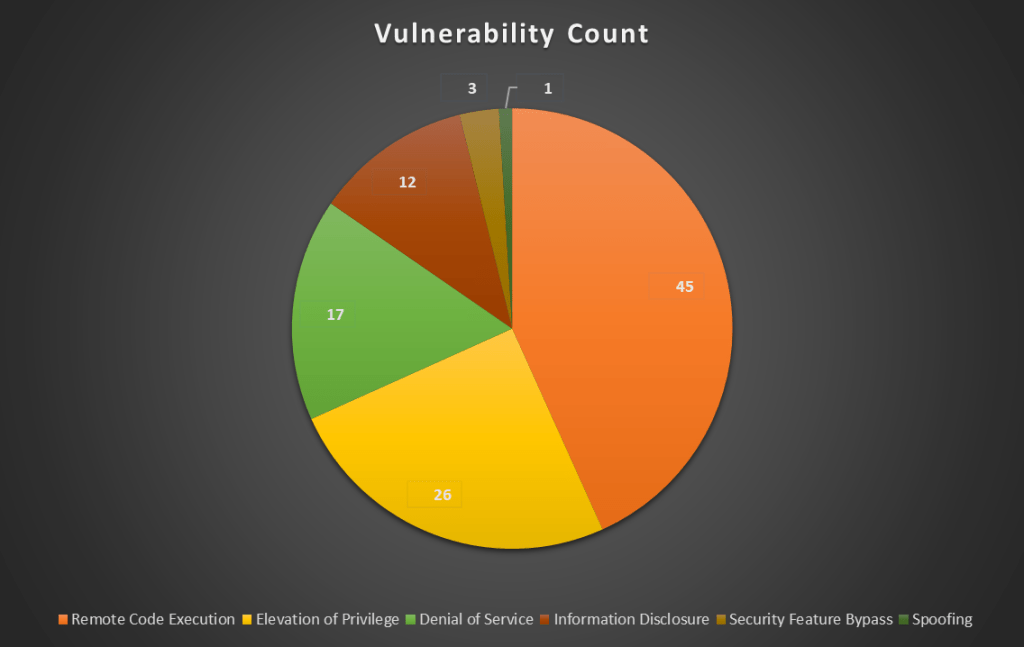
This Patch Tuesday, Microsoft fixed 104 vulnerabilities, with 13 rated as critical and 91 rated as important. Remote code execution is the most common category, with 12 of the 13 critical vulnerabilities being RCE flaws. In fact, 45 out of the 104 are RCE – that’s almost half!
Here’s a pie chart that illustrates the number of vulnerabilities in each category.
Zero Day Vulnerabilities
Microsoft categorizes a vulnerability as a zero-day when it is publicly disclosed or actively exploited, and no official fix or patch is currently available. October’s Zero Days have all been actively exploited, and two have been publicly disclosed.
CVE-2023-41763 – Skype for Business, Elevation of Privilege Vulnerability (publicly disclosed): An attacker can send a crafted network call to the target server. Successful HTTP request parsing can grant the attacker access to internal networks and confidential information.
CVE-2023-44487 – HTTP/2, Rapid Reset Attack: This DDoS technique exploits a vulnerability in HTTP/2’s stream cancellation feature, allowing an attacker to send and cancel requests repeatedly. Unfortunately, there is no fix for this yet, but it can be mitigated by rate limiting or blocking the protocol.
Microsoft has provided steps to disable HTTP/2 in its advisory for this vulnerability.
CVE-2023-36563 – Microsoft WordPad, Information Disclosure Vulnerability (publicly disclosed): An attacker can either log onto the system and run a specially crafted application or persuade the victim to open a malicious file to exploit this vulnerability. The attacker can then steal NLTM hashes, which can be cracked to access the victim’s account.
Microsoft has announced that WordPad will not be updated further and will be removed from later versions of Windows. They recommend switching to Word as an alternative.
Critical Vulnerabilities
CVE-2023-35349 – Windows Message Queuing, Remote Code Execution Vulnerability: As of the release date of this blog, there is no further information regarding this vulnerability.
CVE-2023-36697 – Windows Message Queuing, Remote Code Execution Vulnerability: An attacker can exploit this vulnerability by persuading a user on the target machine to connect to a malicious server or compromise a legitimate server host and run it as a malicious server.
CVE-2023-36566 – Microsoft Common Data Model SDK, Denial of Service Vulnerability: As of the release date of this blog, there is no further information regarding this vulnerability other than the requirement of low-level authentication to exploit it.
CVE-2023-36718: Microsoft Virtual Trusted Platform Module, Remote Code Execution Vulnerability: An attacker can exploit this vulnerability while authenticated as a guest mode user. This could lead to a contained execution environment escape.
CVE-2023-41765, CVE-2023-41767, CVE-2023-41768, CVE-2023-41769, CVE-2023-41770, CVE-2023-41771, CVE-2023-41773, CVE-2023-41774, CVE-2023-38166 – Windows Layer 2 Tunneling Protocol, Remote Code Execution Vulnerability: An attacker can exploit these vulnerabilities by winning a race condition.
Products Affected
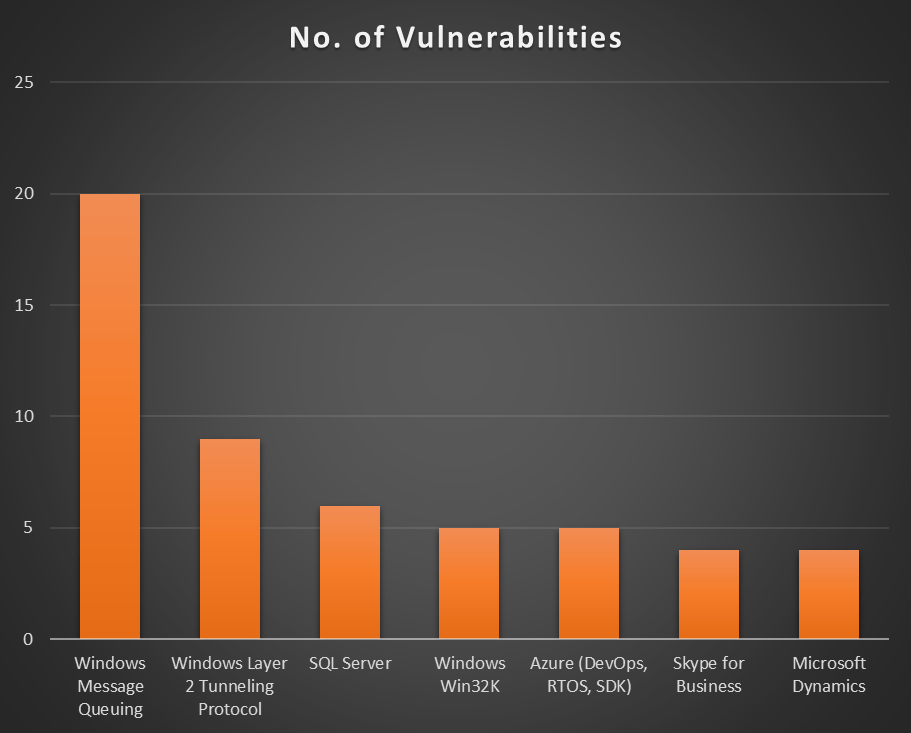
Here is a graph showing the products affected by the most vulnerabilities this October. Note that this graph does not include products affected by fewer than four vulnerabilities.
Other products affected include:
-
- Active Directory Domain Services
- Azure
- Azure DevOps
- Azure Real-Time Operating System
- Azure SDK
- Client Server Run-time Subsystem (CSRSS)
- Microsoft Common Data Model SDK
- Microsoft Dynamics
- Microsoft Exchange Server
- Microsoft Graphics Component
- Microsoft Office
- Microsoft QUIC
- Microsoft WDAC OLE DB provider for SQL
- Microsoft Windows Media Foundation
- Microsoft Windows Search Component
- Microsoft WordPad
- SQL Server
- Skype for Business
- Windows Active Template Library
- Windows AllJoyn API
- Windows Client/Server Runtime Subsystem
- Windows Common Log File System Driver
- Windows Container Manager Service
- Windows DHCP Server
- Windows Deployment Services
- Windows Error Reporting
- Windows HTML Platform
- Windows IIS
- Windows IKE Extension
- Windows Kernel
- Windows Layer 2 Tunneling Protocol
- Windows Mark of the Web (MOTW)
- Windows Message Queuing
- Windows Microsoft DirectMusic
- Windows Mixed Reality Developer Tools
- Windows NT OS Kernel
- Windows Named Pipe File System
- Windows Power Management Service
- Windows RDP
- Windows Remote Procedure Call
- Windows Resilient File System (ReFS)
- Windows Runtime C++ Template Library
- Windows Setup Files Cleanup
- Windows TCP/IP
- Windows TPM
- Windows Virtual Trusted Platform Module
- Windows Win32K
This month’s Patch Tuesday brings us a long list of vulnerabilities, and securing your systems is more important than ever! For vulnerabilities without patches, such as CVE-2023-44487, refer to Microsoft’s security guide and follow the steps provided to stay safe.
SanerNow Vulnerability Management and SanerNow Patch Management detect and automatically fix these vulnerabilities by applying security updates. Use SanerNow and keep your devices updated and secure.

