The Threat Intelligence team of Wordfence discovered two security vulnerabilities in the Orbit Fox WordPress plugin on November 19, 2020. This plugin was developed by ThemeIsle to extend the theme functionalities with various modules like Social Media Share Buttons & Icons, Uptime Monitoring, Google Analytics, custom menu-icons, one-click import page templates, free stock featured images, and page builder addons. The flaws in this particular plugin i.e, privilege-escalation, and a stored XSS vulnerability are said to have impacted over 400,000 sites.
Vulnerability Details
Out of the two vulnerabilities exposed, the Authenticated Privilege Escalation is rated as critical with a CVSS score of 9.9 whereas the Authenticated Stored XSS is rated as medium with a CVSS score of 6.4.
Authenticated Privilege Escalation
Orbit Fox plugin facilitates various functionalities where the registration widget is one of them. This particular widget helps to create a registration form with customizable fields when using the Elementor and Beaver Builder page builder plugins. The plugin allows selecting the default role whenever a user tries to register using the form while creating the registration form. This was developed with the intention that lower-level users like contributors, authors, and editors were not shown the option to set the default user role from the editor, but using the flaw existing in the plugin it is possible to modify the default user role by crafting a request with the appropriate parameter.
Client-side protection was enabled in the plugin to prevent the role selector from being shown to lower-level users while creating a registration form. Unfortunately, the server-side protections or validation was not done to verify that an authorized user can actually set the default user role in a request. Due to this lack of server-side validation, any lower-level user with access to the page/post editor could create a registration form and set the user role to that of an administrator upon successful registration. Once the registration form was created, the user will gain all the administrator privileges like creating a new user and other desired actions.
{"save_builder":{"action":"save_builder","data":{"status":"publish","elements":[{"id":"be9a476","elType":"section","isInner":false,"settings":{},"elements":[{"id":"7ea305d","elType":"column","isInner":false,"settings":{"_column_size":100,"_inline_size":null},"elements":[{"id":"6edacb5","elType":"widget","isInner":false,"settings":{"form_fields[...],"submit_label":"Register","user_role":"administrator"},"elements":[],"widgetType":"content_form_registration"}]}]}],"settings":{"post_title":"BadPost","post_status":"pending"}}}}',
The above-seen request is one such example, where the user_role parameter can be used by any such lower-level user to escalate their privileges to that of an administrator as server-side validation is not taken care of.
Authenticated Stored Cross-Site Scripting
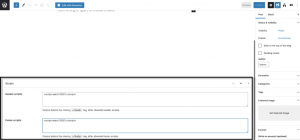
Researchers also found this flaw in the header and footer script feature of the Orbit Fox plugin which allowed any lower-level users to add scripts like malicious JavaScript to posts that would execute in the browser whenever a user visited that page. As we all know, this would later lead to the common impacts of XSS like creating any new administrative user, injecting malicious script, or alter site content through such malicious Java scripts.
Again as a result of lack of server-side validation the issue takes place which leads to undesirable actions by the attackers.
Orbit Fox header and footer script area.
Image credits: Wordfence
Impact
An authenticated lower-level users who successfully exploited these vulnerabilities can take over the site control and perform the following actions:
- Escalate their privileges to those of an administrator and take over a WordPress site.
- Inject potentially malicious JavaScript into posts and redirect users to malicious sites or create new administrative users.
Affected Versions
The vulnerability affects Orbit Fox WordPress plugin versions 2.10.2 and prior.
Note: A site with user registration disabled or Elementor and Beaver Builder page builder plugins not installed would not be affected by this vulnerability.
Solution
A fix for this vulnerability has been released in 2.10.3. Update Orbit Fox WordPress plugin to this fixed version or later.