Cybersecurity is important. It’s a hard truth we all must accept. Cyber threats are constantly evolving, targeting individuals, businesses, and governments. As much as I hate to say it, protecting sensitive information and maintaining secure systems is crucial.
The National Institute of Standards and Technology (NIST) framework manages and reduces cybersecurity risks by providing structured guidelines.
Let’s deep dive into VM lifecycle NIST framework and implement them with a vulnerability management tool , shall we?
Introduction to NIST
Founded in 1901, the National Institute of Standards and Technology (NIST) is a federal agency within the U.S. Department of Commerce. NIST’s mission is to promote innovation and industrial competitiveness by advancing measurement science, standards, and technology. Over the years, NIST has played a key role in various scientific and technological advancements, including cybersecurity.
The Vulnerability Management Lifecycle NIST
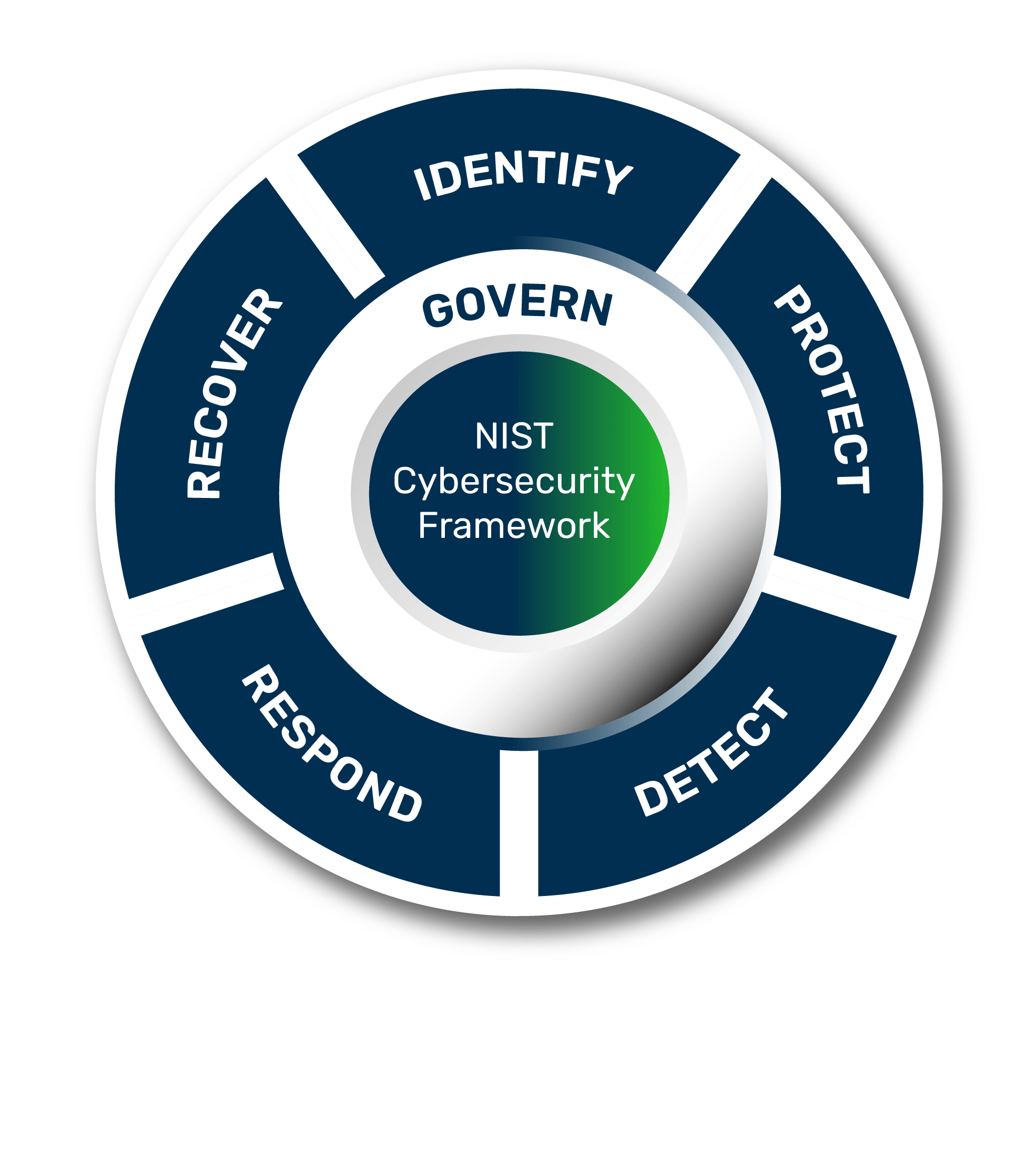
The NIST Cybersecurity Framework outlines five core functions to manage cybersecurity risks: Identify, Protect, Detect, Respond, and Recover. These functions form the foundation of the vulnerability management lifecycle.
Identify
In the “Identity” phase, organizations develop an understanding of their cybersecurity risks by identifying critical assets, vulnerabilities, and potential threats. However, it involves conducting risk assessments, asset inventories, and vulnerability scans. Also, understanding their risk landscape lets companies prioritize efforts and allocate resources effectively.
Protect
The “Protect” function focuses on implementing safeguards to secure critical assets and data. It includes deploying security controls such as firewalls, encryption, access controls, and regular patch management. Protecting against vulnerabilities involves continuously monitoring systems for potential weaknesses and promptly applying security updates.
Detect
In the “Detect” phase, organizations establish capabilities to identify cybersecurity events in a timely manner. It involves implementing intrusion detection systems, security information and event management (SIEM) solutions, and continuous monitoring tools. Detecting vulnerabilities early allows organizations to respond swiftly and minimize potential damage.
Respond
The “Respond” function involves developing and implementing response plans to address detected cybersecurity incidents. Also, it includes defining roles and responsibilities, establishing communication protocols, and conducting regular incident response drills. Moreover, effective response plans enable organizations to contain and mitigate the impact of vulnerabilities and breaches.
Recover
The “Recover” phase focuses on restoring normal operations and minimizing the impact of cybersecurity incidents. However, this involves developing recovery plans, conducting post-incident reviews, and implementing improvements based on lessons learned. A robust recovery process ensures that organizations can quickly bounce back from incidents and enhance their resilience.
Why use the NIST Cybersecurity Framework?
Common Cybersecurity Issues:
- Concern about hidden risks and unknown
- Lack of an accurate inventory of assets that need protection
- Challenges in determining which vulnerabilities to remediate first
- Need to understand how to address risk items with current tools and available solutions in the marketplace.
- Difficulty in ensuring that colleagues outside the cybersecurity team understand cyber risks
- Increasing pressure from the board to ensure compliance with NIST standards
Best Practices to Implement NIST Cybersecurity Framework
Implementing the NIST Cybersecurity Framework effectively requires following best practices:
- Conduct Regular Assessments: Regularly check your company’s cybersecurity through vulnerability scans, penetration testing, and then risk assessments.
- Prioritize Vulnerabilities: Focus on fixing the vulnerabilities that pose the greatest threat first.
- Automate: Use automation tools to streamline processes like scanning, patching, and reporting.
- Continuous Monitoring: Implement continuous monitoring tools to detect and respond to vulnerabilities in real-time.
- Develop Incident Response Plans: Establish and regularly update plans to ensure a coordinated and effective response to cybersecurity incidents.
Conclusion
A place where cyber threats are constantly changing, vulnerability management is crucial for a company’s cybersecurity strategy. The NIST Cybersecurity Framework provides a comprehensive approach to managing vulnerabilities and enhancing overall security. By following best practices and using the framework’s guidelines, companies will effectively identify, protect, detect, respond to, and recover from cybersecurity incidents. Embracing the NIST framework not only strengthens defenses but also promotes a proactive cybersecurity culture, ensuring a resilient and secure digital environment.