Cybersecurity is essential to every enterprise as there is no sign of dipping of security threats. An increase in cybercrimes has led enterprises to implement various methods to prevent them. Even after such implementations, some security threats go undiscovered for months. While IT teams ask themselves what they should do, vulnerability assessment vs penetration testing is a question that would chart the journey the whole team takes. Vulnerability Management Software is a one stop solution for all these problems.
Many security teams choose efficient tools to gain visibility into their risks, whereas winning teams look for tools not just to get visibility but also to remediate those risks instantly. Hence, you have to be careful in assessing your systems for vulnerabilities by choosing efficient security tools like vulnerability management tool.
Besides, vulnerability assessment and penetration testing are used interchangeably because of a lack of knowledge or market hype. But both are different in terms of their objectives. Let us know more about them one by one.
Vulnerability Assessment
Vulnerability Assessment is a comprehensive method for detecting, classifying, and prioritizing vulnerabilities. It will make your process of vulnerability management more efficient. Hence, it is essential to analyze them before fixing them. Vulnerability assessment becomes more critical when the vulnerabilities are complex. Therefore, checking security loopholes will close the pathway for attackers.
The vulnerability assessment is a one-time process. It also helps to identify threats and risks at the earliest. To add to this, it even enables remediation to close the security gap in IT infrastructure.
Vulnerability assessment aims to keep security risks under control. It helps detect and mitigate harmful vulnerabilities, prioritizes vulnerabilities, and remediates them on time.
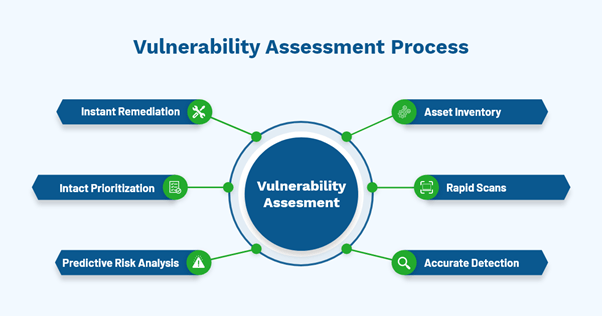
Check out the following diagram that summarizes the vulnerability assessment process.
Vulnerability Assessment Process
-
Asset inventory
Asset inventory is the foundation of complete IT security. Without clear visibility over IT assets, it won’t be easy to protect them. Understanding the environment and its assets will aid in better security vulnerability assessment.
-
Rapid scans
Scanning is the primary process of identifying vulnerabilities. Most organizations rely on periodic scanning, which takes place once or twice a month. Periodic scanning makes the organization more vulnerable to security risks. Hence, scanning should be a daily ongoing process to manage vulnerabilities. The vulnerability scanner must scan within minutes. Fast scanners help quick remediation after detection.
-
Accurate detection
Vulnerability detection marks the foundation for assessing vulnerabilities. If this detection is not accurate, the assessment data will not be precise. For precise detection, there is a need for an effective vulnerability scanner. It should detect vulnerabilities without producing false positives. An inefficient vulnerability scanner drains the security team’s energy in assessing false positives.
-
Predictive risk analysis
Predicting vulnerability exploits before they show up is one way to manage vulnerabilities. You can improve security posture by predicting the probability of new exploits. You can analyze the recorded occurrence and probability of recurrence. Thus, it can estimate the nature of emerging vulnerabilities.
-
Intact prioritization
After detecting the vulnerabilities, we need to rank them based on severity levels. CVSS and risk-based assessment will help in precise prioritization. Prioritization aid in remediating the high critical risks first. The combination of CVSS and risk-based vulnerability management is even more effective.
-
Instant remediation
Detecting the vulnerabilities is on one side, and remediating is on the other. After detection of vulnerabilities, remediation of vulnerabilities will reduce potential attacks. Most organizations lag in remediating vulnerabilities on time and going for an integrated vulnerability and patch management solution with help here.
Penetration Testing
Penetration testing involves finding out vulnerabilities in a particular network. It is essential to validate an enterprise system, networks and applications. Furthermore, it helps to find security loopholes before cybercriminals do. It also determines if the vulnerability is genuine or not. When a penetration tester exploits a threat, it is considered genuine.
Suppose they are unable to exploit, it is regarded as a theoretical vulnerability. A major key point to note is, exploiting theoretical vulnerabilities will lead to Dos. Dos refers to Denial of Service where many packets are loaded onto the server, making the application unavailable for legitimate users.
The pen testing process includes five stages.
Penetration Testing Process
-
Planning and gathering open-source intelligence
In this step, you have to define the scope of the test and plan upon which system must be addressed with testing methods. Gathering open-source intelligence includes domain names, servers and networks to get better insights about the target and the vulnerabilities that can exploit them.
-
Scanning application’s code
This step includes understanding the response of the target application after intruding with applicable codes. Such tools can scan the entire code at a single pass or piece by piece of the code is analyzed in its running state.
-
Gaining access to privileges
After intruding application codes, the tester uses web application attacks called SQL injection, cross-site scripting etc. These techniques will uncover the target’s vulnerabilities so that tester can exploit them. Most importantly, testers try to escalate privileges, steal data, dump a large number of packets etc., to understand the damage they can cause to target.
-
Maintaining access
This stage aims to maintain access in the target to imitate persistence presence. Tester maintains access to find out vulnerabilities in the system. Further, persistent attacks are used by testers for a long time to steal your confidential information.
-
Analysis through reports
The penetration test report consists of specific vulnerabilities exploited, confidential data accessed, and the time taken by the tester to remain in the system undetected.
Vulnerability Assessment vs Penetration Testing
-
Breadth vs depth
Vulnerability assessment covers many vulnerabilities and uses a breadth over depth approach. It is employed regularly to ensure network security. In addition to this, it helps enterprises know all possible security weaknesses to prioritize them and mitigate them.
Penetration testing uses a depth-oriented approach to check if the network security is strong enough to prevent vulnerabilities and ensure that they are hack-proof.
-
The degree of automation
Another difference is that vulnerability assessments can be automated where IT admins schedule them daily. It will help in wider coverage of vulnerabilities. On the other hand, penetration testing combines automation and manual techniques that digs deeper into the loopholes.
-
High-level of expertise
Vulnerability assessments do not require many skills and also it is an automated process. So, IT admins alone can find vulnerabilities and patch accordingly. On the other hand, penetration testing needs a higher level of expertise to carry out manual processes. Also, it should always be outsourced to a penetration testing services provider.
Which Method is Ideal for Implementing?
Both vulnerability assessment and penetration testing have advantages of their own. They use different approaches and functionalities to deal with vulnerabilities. However, vulnerability assessment is more beneficial than penetration testing.
Vulnerability Assessment v/s Penetration Testing:
Vulnerability assessment discovers vulnerabilities and provides a solution to fix them. Whereas penetration testing provides if hackers can penetrate system security and any hacker can penetrate through, what harm will they inflict to the systems?
In addition to this, vulnerability assessment is integrated security program that improves the security posture. In contrast, penetration testing gives you an idea of how effective your security program is. Hence, vulnerability assessment offers good results than penetration testing.
SanerNow Vulnerability Assessment Program
SecPod SanerNow provides continuous vulnerability assessment that aids in improved security posture. It includes every step of assessment from identification to remediation of vulnerabilities. Therefore, it can be the best fit to assess your systems and network vulnerabilities.
Schedule a demo if you have not seen SanerNow in action!