How many vulnerabilities do you have in your IT infrastructure right now? The odds are that the number could be thousands or even 10s of thousands and always rising too! And with software vendors releasing updates to their software almost daily, there’s always a constant chance for potential risk in the update that could lead to a cyberattack. With uncountable vulnerabilities being discovered every day, how do you effectively manage the ever-expanding attack surface? How to prioritize risk?
Risk Prioritization strategies paired with a attack surface management tools are the only way forward to effectively and efficiently manage and rapidly reduce the attack surface.
The Age-old Dilemma: How to Prioritize Risk?
A modern IT network, if scanned, will most likely have a significant amount of security risks. And that begs the question, which risk should you remediate first?
With different criticalities, different levels of exploitability, availability of exploit kits, and other factors influencing the potential dangers of security risk, Security teams are left at sea with risk remediation and attack surface reduction.
Adding to the dilemma is the obvious lack of manpower and resources to handle the detected security risks. With most security teams equipped with manual detection and remediation tools, the task of remediating risks and reducing the attack surface becomes very difficult.
So, which strategy would work best for IT security teams to prioritize risks and rapidly reduce the attack surface?
Prioritizing Risks: The Best Risk Prioritization Strategies for 2024
Risk Prioritization strategies can break or make your organization’s IT security. Here are the best strategies to implement for your organization, regardless of size, structure, or space.
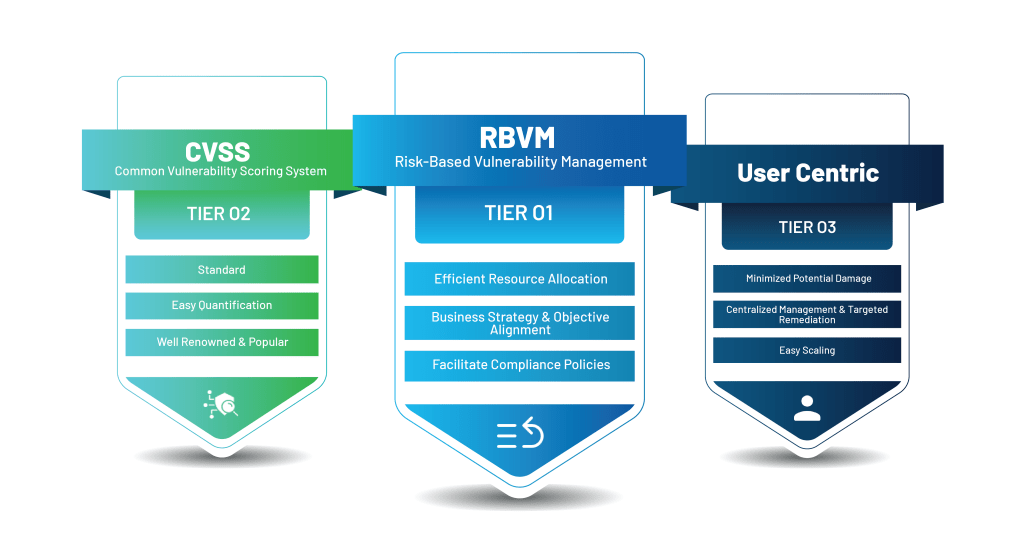
Risk-based Vulnerability Prioritization
Risk-based Vulnerability Prioritization is probably the most effective way of combating modern risks. By combing through your organization’s IT infrastructure and actively looking for weaknesses, understanding the potential risk each of them can have on your organization, and quickly remediating them, risk-based vulnerability management stands shoulders above other risk remediation strategies. It involves understanding which security risk can have the most impact on your organization and working in a top-down approach to mitigate the security risks.
Advantages:
- Allows you to allocate your resources and manpower efficiently.
- Helps align business strategies and objectives with your security efforts.
- Helps you meet compliance requirements.
- Significantly improves overall cyber resilience.
Disadvantages:
- Complex to implement when compared to other methods.
- Doesn’t have a proper standard or guideline to follow.
CVSS-based Vulnerability Prioritization
The most popular way of prioritizing security risks is CVSS-based vulnerability prioritization. Security risks in the wild, mainly software vulnerabilities, are assigned a score based on their criticality or how dangerous they can be. This Cumulative Vulnerability Scoring System can provide a baseline for IT and Security teams to sort the detected vulnerabilities in their network quickly and get on with the task of patching them.
Advantages:
- Provides a standardized way of prioritizing risks.
- Easy to measure results due to easy quantification of the potential risks.
- Well-renowned and popular method.
Disadvantages:
- CVSS is not dynamic, so if a security risk suddenly becomes critical, it might not be reflected in the score.
- A risk can have a different impact on different environments, and the CVSS score doesn’t incorporate the business context.
User/Device Centric Vulnerability Prioritization
Another popular way of prioritizing security risks in your organization is user/device-centric prioritization. In any organization, some devices are more important than others. It might hold sensitive data or company secrets or might be used by a critical member of the team, making it very important to protect them.
So, by prioritizing these devices over individual security risks, this method of risk prioritization helps protect the most important assets of the organization and minimize the impact of a successful cyberattack.
Advantages:
- Minimizes the potential damage a cyberattack can cause to an organization.
- Helps target remediation with clear-cut aim and centralizes management.
- Easily scales up with your infrastructure.
Disadvantages:
- Obvious security gap in less critical infrastructure, which can lead to potential cyberattacks.
- Resource and manpower intensive due to the continuous focus needed in protecting critical assets.
Conclusions
Every organization has different priorities and goals, so it is critical to choose the right strategy based on your organization’s structure and what matters the most to you and your organization.
While there’s a multitude of risk prioritization strategies that can have varying effects on your organization’s security posture, there is no one-size-fits-all. But risk-based vulnerability prioritization is as close as it can get to an ideal risk prioritization strategy that can significantly improve your organization’s security posture and prevent cyberattacks.


