In today’s digital world, cyberattacks are becoming more frequent and sophisticated. Attackers are constantly refining their methods, and no organization—large or small—is completely immune to their reach. Many businesses struggle to protect their IT environments effectively, leading to breaches, financial losses, and damaged reputations. To stay ahead, organizations need to rethink their cybersecurity strategies and adopt key foundational principles that can significantly improve their defenses.
There is considerable emphasis on threat detection, incident response, recovery, and resilience, often based on the assumption that “attacks are inevitable.” While being prepared for such scenarios is essential, it should not come at the expense of not prioritizing prevention. Strengthening defenses, improving cyber hygiene, and minimizing the attack surface are critical steps in making cyberattack prevention a reality.
Here, we explore seven essential principles to help prevent cyberattacks and strengthen your IT security posture.
Seven Key Principles
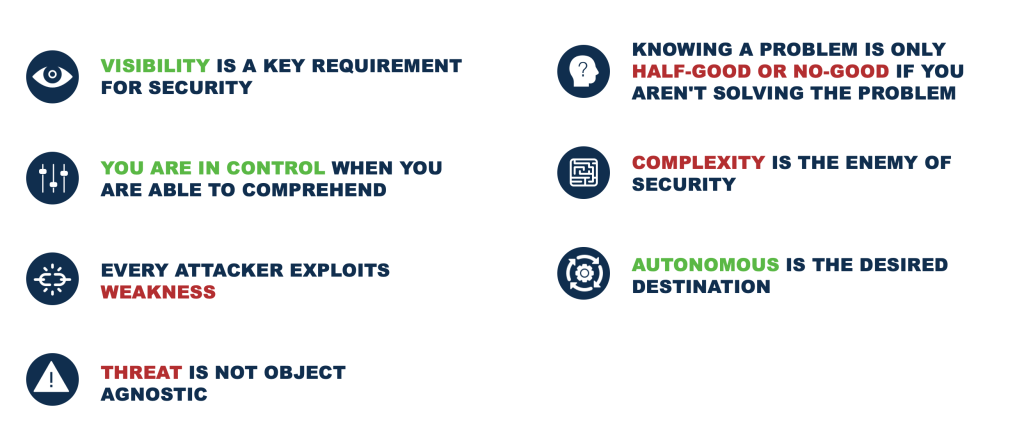
1. Visibility is a Key Requirement for Security
You cannot protect what you cannot see. Continuous visibility is a fundamental requirement for ensuring a secure IT environment. Organizations must have a clear and uninterrupted view of their networks, devices, applications, and data at all times. Since IT environments are constantly evolving, it’s critical to have real-time monitoring that highlights changes and potential vulnerabilities. Blind spots in your IT infrastructure make it easy for attackers to exploit weaknesses, so maintaining visibility is paramount.
Implement tools and processes that ensure continuous visibility across your IT infrastructure.

2. You are in Control When You are Able to Comprehend
Effective security comes from understanding your IT environment. Standardizing your IT infrastructure allows you to establish what is “known-good,” making it easier to detect anomalies and vulnerabilities. When you have a comprehensive understanding of your system, it becomes simpler to maintain control and address potential risks before they evolve into threats.
Standardize and familiarize yourself with every aspect of your IT infrastructure to maintain control.

3. Every Attacker Exploits Weaknesses
Every cyberattack exploits weaknesses within an IT environment, whether they come in the form of vulnerabilities, exposures, or configuration flaws. A vulnerability is a specific flaw that can be exploited, while exposure refers to the availability of that flaw for exploitation. To reduce the risk of attacks, organizations must continually assess their systems for these weaknesses and address them swiftly.
Implement continuous vulnerability assessments and vulnerability remediation program to close security gaps.
4. Threat is not Object Agnostic
Not all threats or assets in your IT environment are created equal. Mission-critical applications, data, and infrastructure should be prioritized when assessing potential risks. Identifying the most crucial elements of your IT environment ensures that you’re focusing your security efforts where they matter most, protecting assets that could cause the most damage if compromised.
Classify and prioritize assets based on their importance to business continuity and security.

5. Knowing a Problem is Only Half-Good or No-Good if you aren’t Solving the Problem
Simply being aware of vulnerabilities and issues within your IT environment isn’t sufficient; decisive action is necessary to mitigate these risks. Attackers can exploit these weaknesses faster than you can respond. Allowing vulnerabilities to linger for months or constantly trying to clear a backlog puts you in a reactive mode, playing catch-up instead of staying ahead of potential threats.
Move beyond awareness and take swift, decisive action to eliminate security risks.
6. Complexity is the Enemy of Security
Complexity is often the enemy of security. Overly complex processes, hierarchies, or workflows can slow down decision-making and increase the chance of human error. Simplifying your IT environment and security response procedures enables faster response times and reduces potential vulnerabilities.
Streamline processes and minimize unnecessary complexity to improve your security posture.

7. Autonomous is the Desired Destination
Cybersecurity threats evolve rapidly, and organizations often struggle with limited resources, skill-gap, a growing backlog of vulnerabilities, and constant changes in their IT environments. Automation is the key to keeping up with these challenges.
Leverage automated solutions to maintain continuous cybersecurity posture.

A New Dimension in Cybersecurity: CVEM
These seven principles form the foundation of a modern cybersecurity strategy known as CVEM (Continuous Vulnerability and Exposure Management). CVEM emphasizes the continuous monitoring of devices, applications, data, infrastructure, and users, enabling organizations to detect and respond to vulnerability.
Conclusion
The battle against cyberattacks requires a proactive, comprehensive approach. By adhering to these seven principles—maintaining visibility, standardizing IT environments, identifying and fixing weaknesses, prioritizing assets, taking action, simplifying processes, and embracing automation—organizations can vastly improve their ability to prevent attacks.
Cybersecurity is an ongoing journey, and implementing these foundational elements will ensure you are prepared for whatever challenges come next.

