The shared responsibility model is fundamental to cloud security, defining how security obligations are divided between cloud service providers and their customers. As organizations increasingly adopt cloud services to drive innovation and efficiency, understanding these responsibilities is essential.
Through systematic implementation of the shared responsibility model and deployment of multi layered security controls, organizations can advance their cloud initiatives with greater assurance. Strong security protocols implemented across applications, databases, and network infrastructure enable teams to strengthen their security posture while staying ahead of new threats.
What is the Shared Responsibility Model?
The Shared Responsibility Model (SRM) is a security framework that defines how cloud service providers and customers divide security responsibilities in cloud environments. This model ensures that both parties understand their roles in maintaining security and compliance across cloud and virtual infrastructure. While providers maintain responsibility for securing the cloud infrastructure, customers must protect their data and applications within the cloud.
According to Gartner’s market analysis, by 2025, approximately 50% of enterprise spending on critical IT segments, including application and infrastructure software, business process services, and system infrastructure will transition to cloud- based solutions. This significant shift indicates that organizations are rapidly moving away from traditional on premises deployments in favor of cloud technologies.
How Does it Work?
The shared responsibility model operates on a clear division of security duties. Cloud providers handle the security of the cloud including physical infrastructure, network controls, and host operating systems. Customers manage security in the cloud, covering their data, access management, and application-level controls. For example, in a responsibly managed cloud environment:
- Cloud providers maintain physical security of data centres, including biometric access controls, surveillance systems, and environmental safeguards. They also handle hardware maintenance, firmware updates, and network infrastructure security.
- Customers take charge of securing their deployed applications through regular security patches, vulnerability scanning, and code security reviews. They configure security settings for cloud services, implement access controls, and manage user authentication, including password policies and multifactor authentication requirements.
- The intersection of these responsibilities creates a unified security framework. For example, while providers secure the underlying database infrastructure, customers must implement proper data encryption and access policies.
Why is it Important?
The shared responsibility model stands as a cornerstone of effective cloud security governance, serving multiple functions. Beyond simply defining security boundaries, this model provides organizations with a clear roadmap for risk management, enabling them to identify potential security gaps and address them proactively. It acts as a vital framework for compliance adherence, helping businesses understand exactly which security controls they must implement to meet regulatory requirements, while clarifying which aspects are handled by their cloud provider.
Without this model, organizations would struggle with overlapping security efforts in some areas while leaving dangerous gaps in others, making it an indispensable tool for maintaining a security posture in the cloud.
1. Risk Management: With clearly defined boundaries, organizations can systematically identify vulnerabilities and implement targeted controls. This clarity helps security teams assess risks at each layer of their cloud infrastructure, from network security to application controls.
2. Compliance: Knowledge of shared responsibility helps meet regulatory requirements and industry standards. It also enables organizations to map regulatory requirements directly to responsible parties, ensuring nothing falls through the cracks during compliance assessments.
3. Resource Optimization: Clear responsibility boundaries help organizations allocate security budgets and staff more effectively. Teams can focus investments on controls they must manage rather than duplicating provider-managed security measures. This understanding helps prioritize security spending, staff training, and tool selection based on actual needs rather than perceived gaps.
4. Incident Response: Clear responsibility delineation enables faster and more effective incident response. Teams can quickly determine whether an incident involves provider-managed or customer managed components, streamlining investigation and remediation efforts
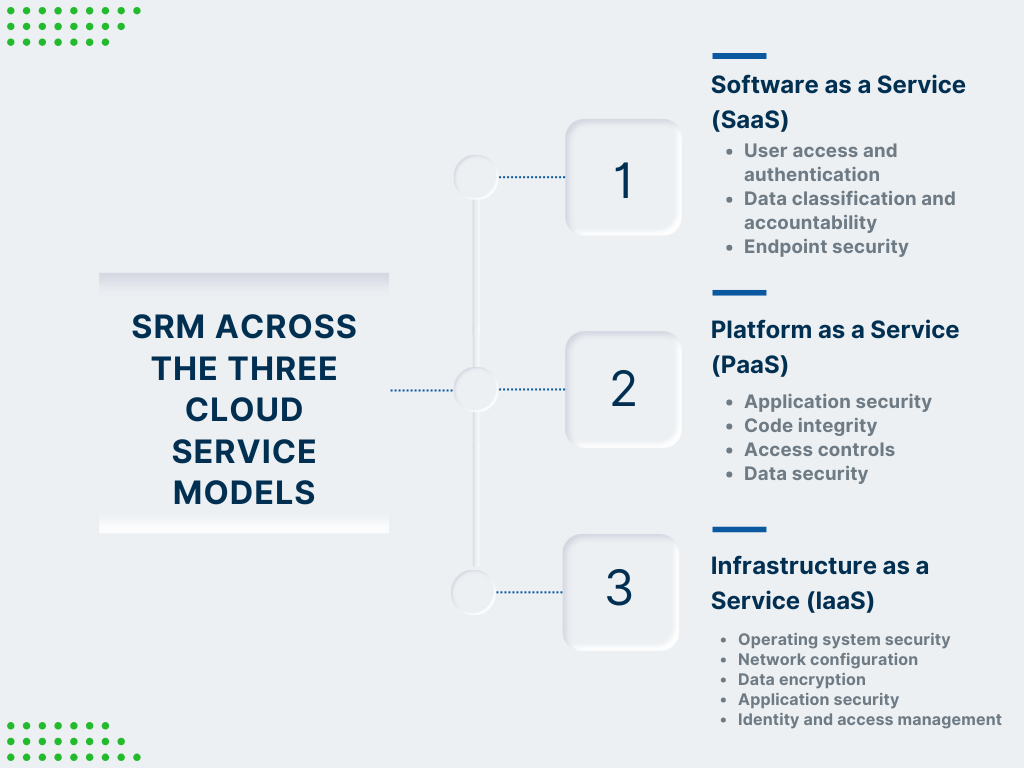
SRM Across the Three Cloud Service Models
The shared responsibility model varies significantly across different cloud service models, including Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS). Each service model represents a different level of control and responsibility division between the cloud provider and the customer.
As you move from SaaS to PaaS to IaaS, customers assume more security responsibilities progressively, while providers handle fewer aspects of the security stack. Let’s look into them:
Challenges in Implementing SRM
While the shared responsibility model provides a clear framework for security governance in the cloud, implementing it effectively remains a significant challenge for many organizations. The complexity of modern cloud environments, combined with evolving security threats and regulatory requirements, creates numerous obstacles that security teams must navigate. Organizations face several hurdles when implementing the shared responsibility model such as:
Lack of Understanding: Businesses often struggle to grasp the exact boundaries of their security responsibilities, leading to potential vulnerabilities. This stems from unclear documentation, changing service features, and differing models across providers. Technical teams may focus too heavily on infrastructure while overlooking application security, or vice versa.
- Multi
- Identity and Access Management: Managing access controls in cloud services requires advanced identity management tools. Security teams need to set proper user permissions, limit access rights, and align authentication rules between cloud platforms and internal networks. These challenges multiply when working with multiple cloud providers and connecting different systems.
- Regulatory Alignment: Meeting compliance requirements while operating within the shared responsibility framework presents unique challenges. Organizations must demonstrate compliance across infrastructure they don’t fully control, implement appropriate controls within their responsibility domain, and maintain clear audit trails across cloud boundaries. This becomes particularly challenging when regulations evolve or when operating across multiple jurisdictions.
Strategic Measures:
Effective implementation of the shared responsibility model requires a comprehensive yet streamlined approach to security management. Organizations must start by thoroughly understanding and documenting their security obligations, creating clear responsibility matrices that define security boundaries between cloud providers and internal teams. This foundation of understanding should be regularly updated and communicated across the organization to ensure alignment. Security implementation in the shared responsibility model revolves around three core principles, as shown below:
Proactive Risk Management:
- Regular risk assessments across cloud deployments
- Comprehensive evaluation of both provider and customer-managed components
- Continuous monitoring and vulnerability detection
Security Controls and Compliance:
- Implementation of identity and access management
- Data encryption and secure configuration practices
- Regular compliance audits and documentation
- Clear incident response procedures
Continuous Improvement:
- Regular training and awareness programs
- Ongoing security validation and testing
- Strong vendor management practices
- Update security measures based on emerging threats
The success of these practices depends heavily on maintaining strong communication channels with cloud providers and ensuring that all team members understand their specific security responsibilities. Regular validation through testing and audits helps organizations identify and address potential security gaps before they can be exploited.
Key Takeaways:
Effective cloud security is not about shifting responsibility but orchestrating a collaborative defense strategy. This model transcends basic security delegation, functioning as a strategic approach to risk management and compliance in cloud environments.
Remember, security in the cloud is a partnership between providers and customers. Success depends on both parties fulfilling their obligations under the Azure shared responsibility model and maintaining open communication about security concerns and requirements. As cloud architectures evolve and threats become more sophisticated, the shared responsibility model will continue to be the cornerstone of cloud security governance, guiding organizations through the complexities of securing their digital assets.

