The first and foremost step of implementing security measures in an organization is getting visibility into their IT infrastructure. However, IT security teams today have visibility only to their hardware and software assets with limited actionable insights.
Just having a high-level visibility will only act as a loophole for hackers to invade your network. Continuous posture anomaly management will give you real visibility to your IT by assessing hundreds of device parameters and artifacts.
Before we dive in into what all continuous posture anomaly can provide, let’s understand what real/naked visibility is.
What is Real/Naked Visibility?
| Superficial visibility | Real Visibility |
| Having information about the software and hardware assets, their asset license, operating system, manufacturer. | Real visibility will include all the information of assets, and additionally gives you a deeper visibility and discovers the aberrations, deviations and outliers present in IT infrastructure |
| Information provided by superficial visibility is often less accurate | Having 360-degree visibility acts as a advantage and provides you with accurate data |
| Without complete information it is difficult to make informed decision | It helps you to make informed decisions |
How does Continuous Posture Anomaly Management help in achieving the Naked Visibility?
1. Discover the most obvious attack vectors:
Continuous Posture Anomaly Management analyzes your IT network and identifies the outliers or aberrations present in your IT infrastructure.
Few examples of these outliers or aberrations are unfamiliar or unique applications, unusual services or processes, irregular IP mappings, multiple login attempts, vulnerable processes and more.
2. Declutter your IT network:
Continuous Posture Anomaly management can help you with decluttering by eliminating the unwanted applications, multiple VPN tools, apps from unknown publishers and more. This would allow only essential applications running your network and can also reduce the software bill of material (SBOM).
3. Attain Binocular View of your organization:
Have visibility like you have never had before, track the changes of your IP and MAC addresses, also know if there is any deviation in the configuration of firewall of any particular system, detect unwanted applications and unique services running in your devices and many such hidden risks and protect your networks from cyberattacks.
4. Eliminate the hidden risks:
Continuous posture anomaly management can not only detect the obvious attack surfaces but also provides the necessary remediation controls that allow you to eliminate them.
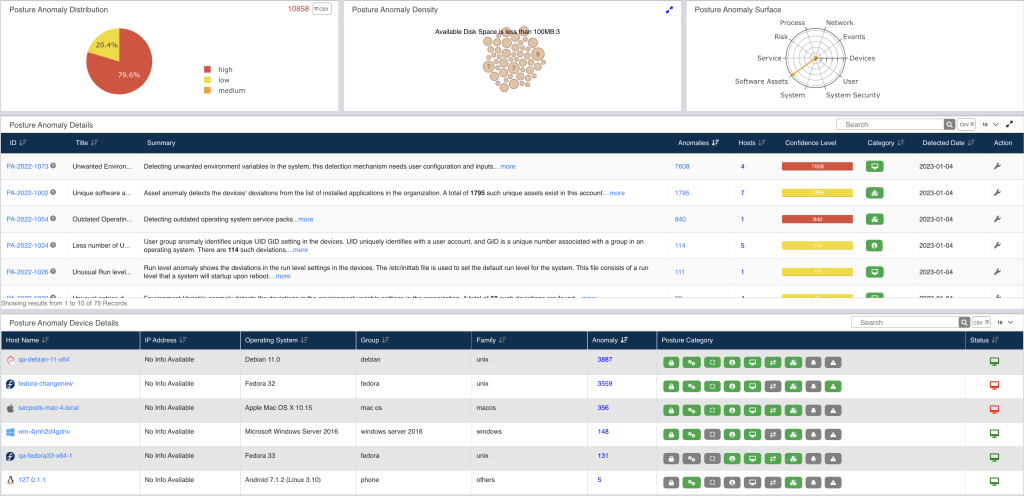
Why Continuous Posture Anomaly Management?
a. To improve security:
Holistically having visibility to your IT infrastructure can increase organization security and can help you identify deviations or aberrations if any and keep you ahead of potential cyber-attacks.
b. To improve operational efficiency:
Most of the cyberattacks these days are due to unnoticed risks, and once your organization is hit by the cyber-attack, productivity decreases. To avoid these circumstances, Continuous posture anomaly management can detect hidden risks and will in turn reduce downtime.
c. Eliminate and achieve perfect security posture:
There’s no use of just detecting hidden risks if you cannot eliminate them. Eliminate the detected hidden risks and achieve all cyber-hygiene measures.
As the saying goes “There is more than what meets the eyes”, superficial visibility is never enough for effective vulnerability mitigation. Therefore, have a naked visibility and comprehensively know your IT assets and stay ahead of attacks.
To know more, Visit: https://www.secpod.com/visibility-control/