Scale. One word we can use to define the cybersecurity world over the past few decades. Networks and devices in them have scaled up and so have the number of security risks in them. As a result, the number of cyberattacks has scaled up, too! With this gigantic increase, traditional vulnerability management methods often fall short. Is automating vulnerability management the only way forward in mitigating the rising number of cyberattacks? Yes.
So, let’s dig deeper into the art of automating vulnerability management.
What is Automated Vulnerability Management?
As the name suggests, automated vulnerability management involves leveraging advanced tools to automate the different steps of the vulnerability management process.
You typically do it to eliminate the manual efforts and speed up the process.
Further, automating the process gives you other benefits too. You get real-time insights into risks, and you can also automate the remediation response as well. However, the biggest advantage is that automation makes your vulnerability management proactive and reduces the potential chances of cyberattacks.
How Automated Vulnerability Management Transforms Your Security
Automating vulnerability management boosts your security and provides you with significant benefits. Let’s dig deeper into some important ones:
- Accurate picture of the attack surface at all times:
Periodic scans do not give a close-to-accurate picture of the security posture at all times. By the time you perform the next scan after 2-3 weeks, numerous risks would’ve surfaced in the form of critical software vulnerabilities, rogue processes, misconfigured firewalls, and much more. Automated scans let you keep track of vulnerabilities almost at all times without you spending time babysitting the scans. - Faster detection and mitigation cycles:
The first step to faster mitigation cycles is to detect the vulnerability as soon as possible. Nowadays, a critical vulnerability is disclosed in a commonly used software tool at least once a week. Typically, a programmed scan takes anywhere between 1 and 5 hours based on the number of devices and other factors. When such a scan is performed only once a week or month, the speed of detection reduces considerably, slowing down your mitigation cycles. With automated scans, you can start the vulnerability management program and roll out the mitigation steps almost immediately after you discover the flaws. - Lowered time and resources for configuring detection and remediation:
Vulnerability scans are usually configured to run periodically. They typically require trained personnel to dedicate a few hours for every scanning cycle to set up the target devices, check the types of configurations, and check many other parameters for the scan. By automating vulnerability management, you only need to set up the scan once. The scanner returns the results automatically without you prompting the scanning tool. Based on your needs, you can even set up separate scans for different devices under different conditions and times. - Continuous compliance with security standards:
Detecting and mitigating vulnerabilities is a compliance mandate for security standards such as ISO, HIPAA, PCI, etc. Some standards require organizations to run weekly or bi-weekly vulnerability scans for all their assets. Automated scans and remediation save time and effort by implementing continuous compliance, where the assets are under continuous monitoring. You can immediately detect risks that point out a non-compliant environment.
- Reduced team fatigue and improved productivity:
In an enterprise security team, vulnerability and compliance teams occupy an important spot in the whole IT strategy. The teams can spend their time analyzing how processes can be improved instead of grunting over manual work while setting up scans each time. Smaller and mid-size organizations can tackle bigger compliance and vulnerability management challenges easily with timely help from smart tools like automated vulnerability scans and assessments. - Eliminate Human Error and Improve Accuracy: A sad thing about modern security processes is that vulnerability management processes are still performed manually. This is typically error-prone and difficult to perform regularly. Another advantage automation brings to the table is that it reduces the risk of human error. Further, you can customize automated tools based on your needs to detect vulnerabilities accurately and minimize false positives as well.
- Achieve and Implement Easy Scalability: Your enterprise is bound to grow and the consequence is that your IT environments will grow and become more complex along with it. Automating vulnerability management is the only way you can easily scale and accommodate this growth. Further, it’ll also ensure that all assets are consistently monitored and protected without the need for additional manual resources.
What are the Best Practices for Automating Your Vulnerability Management?
Automating vulnerability management can be daunting. But here are the best practices you can follow to make the process easier, more effective, and more impactful.
- Comprehensive Visualization of IT Infrastructure:
You can’t protect what you can’t see is a mantra that not only helps you automate but also improves overall security as well. So, completely visualizing your IT environment is vital. Also, by maintaining an up-to-date view of your network, you can ensure that all assets in your network are secure and that your automated systems are effectively securing your IT.
- Integrating Vulnerability Assessment and Remediation:
Automation works best if your vulnerability management is a single cyclic process. So, by integrating vulnerability assessment with remediation, you actually speed up the overall process, too. Further, integration allows you to quickly and automatically address issues without having to switch between different tools or platforms.
- Prioritize Vulnerabilities AND Devices:
Not all vulnerabilities are important, and not all devices are critical. So, another best practice is to automate your systems to prioritize vulnerabilities based on factors such as severity, exploitability, and potential impact. Further, you must also prioritize the devices in your network to ensure your automation efforts are giving you maximum results. By focusing on the most critical vulnerabilities and devices first, you can automate scanning and remediation and fix what matters.
- Automate Patch Management:
What is remediation without patching? Patch management is arguably the most critical component of vulnerability remediation. So, automating the patching process will have the most impact on your security. Automation ensures that patches are applied right on time and consistently across all endpoints in your network. The key advantage is that the time mean time to remediate a security risk (MTRR) is reduced, which in turn minimizes the window of opportunity for attackers.
Conclusion
Automating vulnerability management is a necessity in the modern cybersecurity landscape. It is the single most powerful tool you must leverage to combat and handle the rising number of risks and cyberattacks.
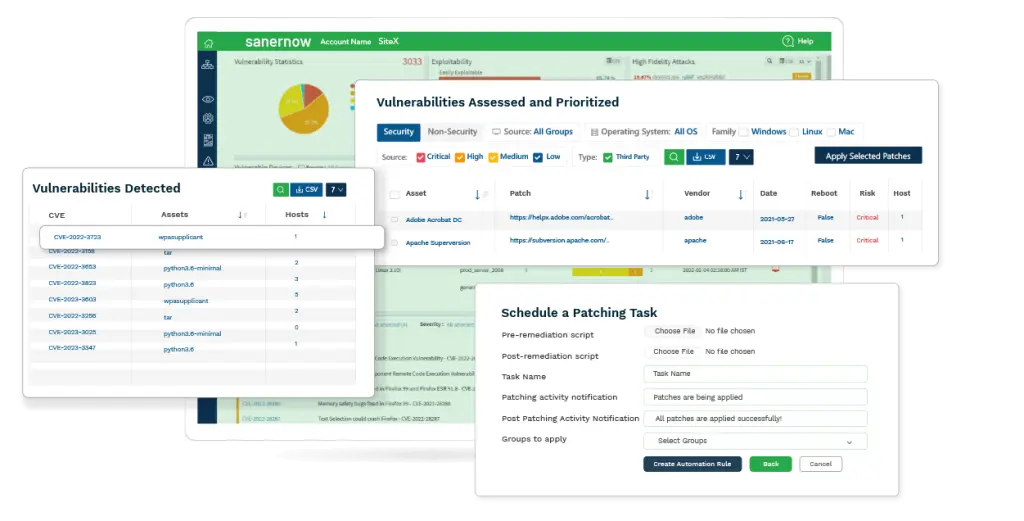
Leverage SanerNow’s advanced automation capabilities paired with its integrated risk detection and remediation to reduce your attack surface and prevent cyberattacks.
Schedule a Demo and see it in action!