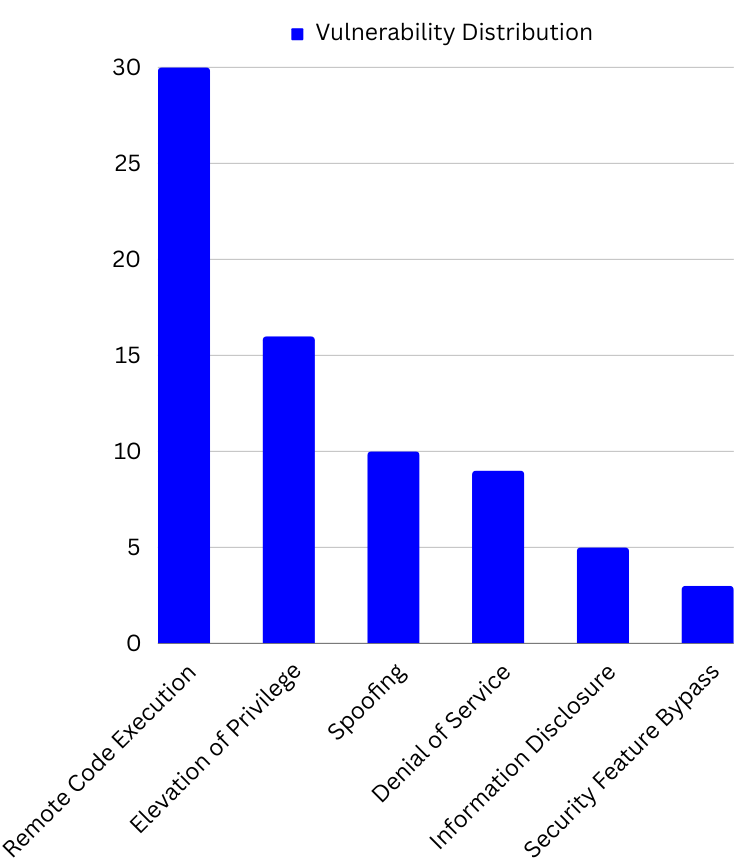
Microsoft’s latest security updates for Patch Tuesday in February 2024 address a total of 73 vulnerabilities. Among these, five are classified as critical, including two zero-day vulnerabilities (CVE-2024-21351 and CVE-2024-21412), with thirty vulnerabilities linked to remote code execution. The utilization of vulnerability management tools is vital for identifying critical vulnerabilities and effectively addressing them.
The security update for February covers Microsoft Windows, Exchange Server, Microsoft Dynamics, Office, .NET, Microsoft WDAC OLE DB provider for SQL, Azure, Microsoft Edge (Chromium-based), Windows Kernel, and more
Zero Day Vulnerabilities
CVE-2024-21351 – Windows SmartScreen Security Feature Bypass Vulnerability. This vulnerability was actively exploited, enabling attackers to bypass SmartScreen security checks. To exploit this vulnerability, an unauthorized attacker would need to send the user a malicious file and persuade them to open it. Successful exploitation of this vulnerability could allow the attacker to circumvent the SmartScreen user experience.
CVE-2024-21412 – Internet Shortcut Files Security Feature Bypass Vulnerability. This vulnerability could bypass Mark of the Web (MoTW) warnings in Windows. Mark of the Web (MOTW) is a security feature by Microsoft aimed at preventing the download or opening of malicious files and attachments. An unauthorized attacker could send a targeted user a specially crafted file intended to bypass displayed security checks. However, the attacker lacks the ability to compel a user to view the attacker-controlled content directly. Instead, they would need to convince the user to take action by clicking on the file link.
Critical Vulnerabilities
| Tag | CVE Number | CVE Title | Max Severity |
| Windows Hyper-V | CVE-2024-20684 | Windows Hyper-V Denial of Service Vulnerability | Critical |
| Windows (PGM) | CVE-2024-21357 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability | Critical |
| Microsoft Dynamics Business Central/NAV | CVE-2024-21380 | Microsoft Dynamics Business Central/NAV Information Disclosure Vulnerability | Critical |
| Microsoft Exchange Server | CVE-2024-21410 | Microsoft Exchange Server Elevation of Privilege Vulnerability | Critical |
| Microsoft Outlook | CVE-2024-21413 | Microsoft Outlook Remote Code Execution Vulnerability | Critical |
Microsoft security bulletin summary for February 2024
In addition, this release includes security updates for the following products, features, and roles.
- .NET
- Azure Active Directory
- Azure Connected Machine Agent
- Azure DevOps
- Azure File Sync
- Azure Site Recovery
- Azure Stack
- Internet Shortcut Files
- Microsoft ActiveX
- Microsoft Azure Kubernetes Service
- Microsoft Defender for Endpoint
- Microsoft Dynamics
- Microsoft Edge (Chromium-based)
- Microsoft Exchange Server
- Microsoft Office
- Microsoft Office OneNote
- Microsoft Office Outlook
- Microsoft Office Word
- Microsoft Teams for Android
- Microsoft WDAC ODBC Driver
- Microsoft WDAC OLE DB provider for SQL
- Microsoft Windows
- Microsoft Windows DNS
- Role: DNS Server
- SQL Server
- Skype for Business
- Trusted Compute Base
- Windows Hyper-V
- Windows Internet Connection Sharing (ICS)
- Windows Kernel
- Windows LDAP – Lightweight Directory Access Protocol
- Windows Message Queuing
- Windows OLE
- Windows SmartScreen
- Windows USB Serial Driver
- Windows Win32K – ICOMP
Product: Microsoft Dynamics
CVEs/Advisory: CVE-2024-21327, CVE-2024-21328, CVE-2024-21380, CVE-2024-21389, CVE-2024-21393, CVE-2024-21394, CVE-2024-21395, CVE-2024-21396
Impact: Cross-Site Scripting, Spoofing , Information Disclosure
Product: Microsoft WDAC OLE DB provider for SQL
CVEs/Advisory: CVE-2024-21350, CVE-2024-21352, CVE-2024-21358, CVE-2024-21359, CVE-2024-21360, CVE-2024-21361, CVE-2024-21365, CVE-2024-21366, CVE-2024-21367, CVE-2024-21368, CVE-2024-21369, CVE-2024-21370, CVE-2024-21375, CVE-2024-21391, CVE-2024-21420
Impact: Remote Code Execution
Product: Windows Internet Connection Sharing (ICS)
CVEs/Advisory: CVE-2024-21343, CVE-2024-21344, CVE-2024-21348, CVE-2024-21357
Impact: Remote Code Execution, Denial of Service
However, SanerNow Vulnerability Management and SanerNow Patch Management detect and automatically fix these vulnerabilities by applying security updates. Finally, use SanerNow and keep your systems updated and secure.