You might have a concrete vulnerability management plan and robust security practices, but sometimes, the most obvious outliers and attack vectors get missed, leading to a dangerous attacker entering your network. A Vulnerability Management Software can prevent these attacks.
So, is your IT security strong enough? Or is it missing something?
A gap exists, a missing piece that cohesively allows all other steps to perform better and improve IT security. Real visibility and intelligent awareness of IT infrastructure is the missing piece that answers these questions. A good Vulnerability management tool can solve these issues.
What is Posture Anomaly, and what is Continuous Posture Anomaly Management?
A posture anomaly is an outlier against the known good in your IT network when the network is evaluated collectively. Here, evaluating your network ‘collectively’ is key to discovering posture anomalies. For example, open ports in a system that shouldn’t have been open are an anomaly.
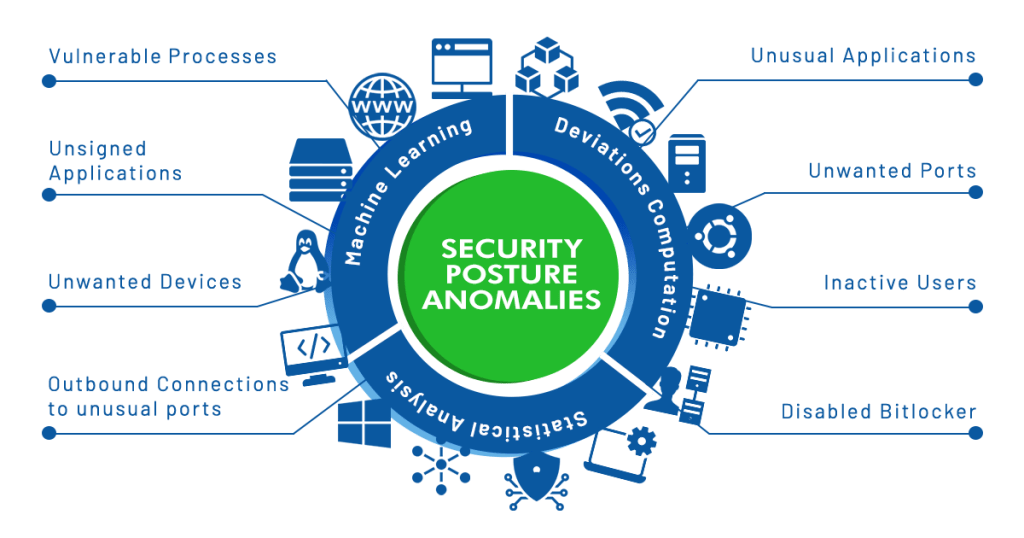
Continuous Posture Anomaly Management (CPAM) is the detection and remediation of these anomalies in your IT environment to improve your overall IT security posture.
Why is Continuous Posture Anomaly Management the Missing Piece?
You might continuously perform vulnerability management and weed out all the vulnerabilities, but your IT infrastructure will still be at risk without fixing posture anomalies. Because the most obvious issues are the easiest to exploit, and they are often missed. Further, if your IT assets are not working as they are supposed to, your IT environment is abnormal and filled with posture anomalies. So, normalizing your environment by detecting and fixing those abnormalities is critical before a cyberattack hits.
Take a vulnerability scanner, for example. It looks for vulnerabilities in a particular device alone, but a posture anomaly scanner looks at the bigger picture and collectively analyses your IT network to detect posture anomalies. A vulnerability scanner will not detect the open port since it is not a vulnerability but a security risk nonetheless. Nothing wrong with an open port until it is suddenly exploiting with an unknown application!
So, without real visibility and intelligent awareness about the posture anomalies in your environment, whatever you do will not be effective enough.
So, How is Continuous Posture Anomaly Management Beneficial?
· Intelligent visibility for better IT security
Superficial visibility over your IT assets isn’t enough. In your IT network with 100s and 1000s of devices, only knowing the basic information like device type, software assets installed, etc., doesn’t provide an entire picture of the actual risk your IT assets are in.
Continuous Posture Anomaly Management provides holistic visibility into your IT network and becomes an intelligent addon to improve IT security. With machine learning and statistical analysis, CPAM identifies dangerous anomalies that a vulnerability scanner can’t and provides real visibility into your infrastructure.
Improves your overall cyberattack prevention plan
· Pre-Cleanup for Improved operational efficiency
If your IT network consists of unnecessary assets like unused software, it can lead to untold potential risks, so why keep it? Further, while you perform vulnerability management, you must scan for vulnerabilities in these unnecessary assets too. This leads to even lengthier scans and tests and preventable wastage of resources and time. Unnecessary assets can lead to preventable attacks.
So CPAM pre-cleans and declutters your IT environment from unused software, ports, services, and more and improves the effectiveness of other IT security processes like vulnerability management, etc.
Conclusion
Your IT security stack might consist of efficient vulnerability management or quick detection and response. But to prevent cyberattacks, minimizing your infrastructure’s attack surfaces is what matters.
Continuous Posture Anomaly Management is the new weapon in your IT arsenal. A silver bullet that not only reduces the attack surface by detecting and remediating posture anomalies. But also improves every other IT security process, making it an indispensable part of every IT admin’s security arsenal.

