Has your organization’s vulnerability assessment framework proven effective against the present cyber-attacks?
A majority of the organization’s existing vulnerability assessment framework does not detect vulnerabilities beyond CVEs, lacks visibility and accuracy, and does not instantly remediate vulnerabilities. Therefore, a good
vulnerability management tool can help to combat these vulnerabilities.
While setting up an effective vulnerability assessment framework, it should achieve complete visibility, continuous monitoring, automatically assess vulnerabilities beyond CVEs, and get comprehensive reports.?
But let’s first understand why detecting and assessing vulnerabilities beyond CVEs with a vulnerability management software is essential.
Why Assessing Vulnerabilities Beyond CVEs Important?
Besides vulnerabilities with CVEs, there are many other vulnerabilities to watch out for, such as system misconfiguration, unknown assets, and system anomalies.
Many security/IT teams might still believe managing vulnerabilities with CVEs is sufficient. But attackers are finding every possible sophisticated way to invade exploits in organizations.
According to stats, more than 6,000 vulnerabilities do not have CVE assigned. Some of them have led to critical cyber-attacks like the Marriot attack, which was caused due to misconfiguration.
So, to ensure your organization is safe from any kind of cyberattacks, it is vital to detect vulnerabilities without CVEs too.
Advanced Vulnerability Assessment Through SecPod’s AVM Framework
Generally, traditional vulnerability assessment ends without instantly remediating vulnerabilities. But what’s the point of detecting vulnerabilities if we are not going to remediate them?
With SecPod’s advanced vulnerability assessment framework, IT teams finally manage vulnerabilities more effectively.
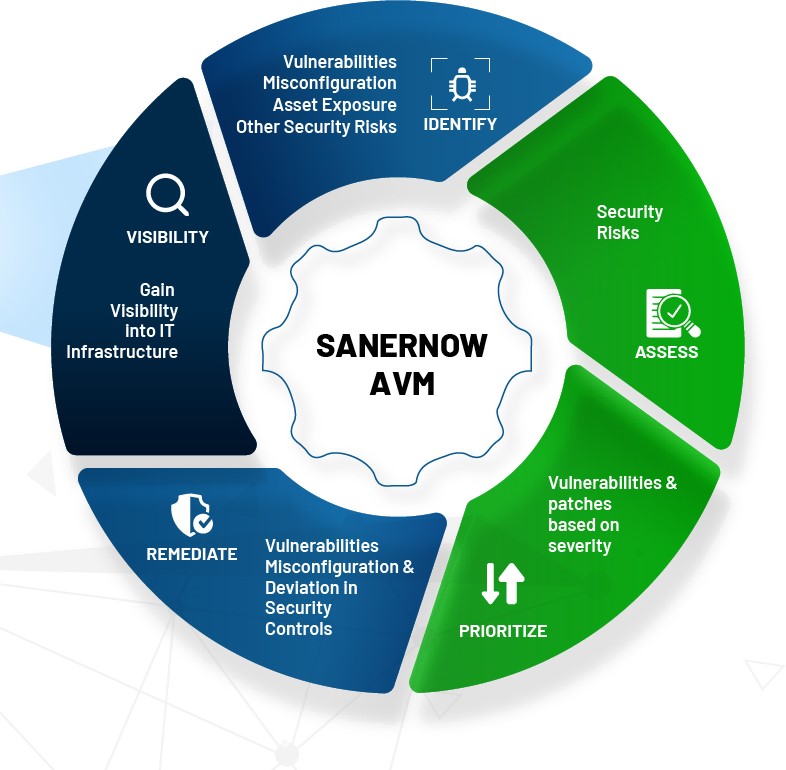
1: Gain visibility into IT infrastructure
- Ensure that you have a comprehensive overview of all the assets present in your organization.
- You can detect vulnerabilities more precisely and improve performance by having complete visibility.
2:?Identify software vulnerabilities and beyond
- The next step, after identifying assets, is to scan and detect vulnerabilities and other security risks.?
- The other security risks include misconfiguration, posture anomalies, missing configuration, deviation in security controls, IT asset exposure, and security posture anomalies.
3:?Assess security risks
- Assess the detected vulnerabilities and assign appropriate severity levels.
- IT teams can plan and prioritize vulnerabilities for instant remediation by adding a severity level.
4:?Prioritize vulnerabilities
- Prioritize vulnerabilities and other security risks based on their severity level as critical, high, medium, and low.
- With prioritization, you can address critical vulnerabilities first, followed by the rest.
5: Remediate vulnerabilities
- Completely remediating vulnerabilities and other security risks detected in your organization while adhering to compliance and regulatory policies.
Why should you follow this Advanced Vulnerability Assessment Framework?
- It is a continuous and repeatable process
- Attain a broader approach to looking at vulnerabilities
- Mitigate vulnerabilities instantly with integrated remediation
- Improve the speed of reducing the vulnerabilities
- Obtain accurate and precise scan results
SanerNow Advanced Vulnerability Management
SecPod’s SanerNow is an Advanced Vulnerability Management platform where you can gain complete visibility into your organization’s assets, detect vulnerabilities, misconfigurations, and other security risks, and apply patches and necessary security controls to remediate vulnerabilities instantly.
?With SanerNow AVM:
- Get a comprehensive view of your organization’s network
- Blazing-fast vulnerability scans
- End-to-end automation
- Integrated patch management
- Manage vulnerabilities and other security risks through a single console
- Leverage hundreds of security remediation controls
- Get auto-generated customizable insightful reports.
To learn more about SanerNow Advanced Vulnerability Management, check out the technical brief.?
Since cyberattacks are increasing, and also hackers are finding more sophisticated ways to find loopholes in your organization’s security posture. It’s finally time to adopt an advanced vulnerability assessment framework to keep your organization ahead of cyberattacks and, more precisely, manage vulnerabilities and other security risks.