The news of numerous exploits on Citrix ADC(formerly NetScaler ADC) has been hitting the headlines lately. A total of 550,000 compromise attempts recorded as per latest available statistics. Thousands of systems were sitting ducks while Citrix delayed the final release of necessary updates for the vulnerable devices. This is done using a vulnerability management tool.
Citrix ADC is an application delivery and load balancing solution that accelerates application performance, enhances application availability, secures mission-critical apps from attacks and lowers server expenses by offloading computationally intensive tasks. The vulnerability that affects Citrix ADC can be remediated using a patch management solution.
CVE-2019-19781 is a flaw in Citrix ADC and Citrix Gateway that allows an attacker to execute arbitrary code via directory traversal. This flaw discovered by Mikhail Klyuchnikov of Positive Technologies who explains that in a real world scenario, attackers can obtain direct access to a company’s local network from the Internet. An attacker would not require access to any accounts to launch the attack.
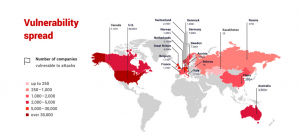 credits: Positive Technologies
credits: Positive Technologies
According to the report published by Positive Technologies in late December 2019, atleast 80,000 organizations spread across 158 countries known to be at risk. The United States, the UK, Germany, the Netherlands, and Australia are the top 5 countries with maximum vulnerable devices.
Attack Chronology of CVE-2019-19781
Early on this month, researchers observed reconnaissance attempts for Citrix ADC and Citrix Gateway servers vulnerable to CVE-2019-19781, but there were no instances of active exploitation. Two days after which, numerous working exploits for CVE-2019-19781 were made public by security researchers. These exploits could be used to create reverse shells back to the attackers machines and execute commands on the vulnerable devices. A deep analysis of the vulnerability and the exploit details published by MDsec is available here.
Soon after, a threat actor conquered the vulnerable Citrix Servers to deliver a payload named NOTROBIN by FireEye researchers. The threat actors gained access to a vulnerable Citrix server. Removed the existing malware processes on the device and then deployed NOTROBIN. Which kept subsequent exploitation attempts on the device at bay. That’s not all, NOTROBIN was also designed to maintain backdoor access on the infected device with a secret passcode. Researchers predicted that the motivation behind threat actors. Collecting data from vulnerable NetScaler devices could be to launch a widespread campaign.
Chronology
Analysis of most exploitation attempts revealed that these attacks deployed coinminers or the NOTROBIN payload. But recently, security experts have also found ransomware being delivered after infection. FireEye identified this ransomware as Ragnorak. The threat actor uses multiple exploits to abuse vulnerable internal systems and also move laterally inside the organization.
The ransomware known to exclude Russian and Chinese countries from encryption. Interestingly, Ragnorak tries to disable the Windows Defender by adding Windows group policies which disable protection features on Windows. Additionally, Ragnorak also attempts to delete Shadow Volume Copies, turn off Windows Firewall and disable Windows automatic startup repair.
Some files used by Ragnorak reveal that the ransomware is under active development to include payloads for infection of Unix systems too and thereby shape the malware to be capable of cross platform infection. Other features of Ragnorak are:
- Uses AES encryption and encrypts the generated key with a bundled RSA encryption key.
- Appends the extension “.ragnorak” to encrypted files.
- Avoids encryption of files with “.exe”, “.dll”, “.sys”, and “.ragnarok” extensions.
Under the Breach researchers have attributed attacks on vulnerable Citrix systems in an automation company to the Sodinokibi ransomware. The attackers have threatened the victims to publish the data in case the ransom demands are not met.
Affected Products
- Citrix ADC and Citrix Gateway version 13.0 all supported builds before 13.0.47.24
- NetScaler ADC and NetScaler Gateway version 12.1 all supported builds before 12.1.55.18
- NetScaler ADC and NetScaler Gateway version 12.0 all supported builds before 12.0.63.13
- NetScaler ADC and NetScaler Gateway version 11.1 all supported builds before 11.1.63.15
- NetScaler ADC and NetScaler Gateway version 10.5 all supported builds before 10.5.70.12
- Citrix SD-WAN WANOP appliance models 4000-WO, 4100-WO, 5000-WO, and 5100-WO all supported software release builds before 10.2.6b and 11.0.3b
Impact
This vulnerability allows any unauthorized attacker to access published applications and attack other resources of a company’s internal network using Citrix server as the initial infection point. An unauthorized attacker can execute arbitrary code via directory traversal to deliver ransomware, coinminers, etc.
Solution
Citrix has released updates for all supported versions of Citrix ADC, Citrix Gateway, and applicable appliance models of Citrix SD-WAN WANOP. Must apply these updates without any further delay.
Researchers have indicated that patching of systems with the latest available updates would not be sufficient to ensure safety and security of the devices. Systems which affected before installation of the updates could have a backdoor left behind, which abused to launch further attacks anytime.
Citrix working with FireEye Mandiant has released a scanner which looks for infection on a device using known indicators of compromise. Advise for all organizations to use this tool to get an awareness of potential compromise related to the aforementioned vulnerability on their systems.

