Organizations worldwide are investing heavily in cybersecurity tools to defend against increasing threats. But here’s the irony, the more tools they use, the more vulnerable they often become.
A recent study by Ponemon Institute found that enterprises deploy an average of 45 different security tools. Yet, 53% of security professionals believe their organization is still not effective at reducing risk. The very tools meant to safeguard them are, in many cases, creating complexity, confusion, and security gaps. So, is your cybersecurity stack protecting you or working against you? Let’s explore how cybersecurity overload can be a bigger risk than a solution.
The Growing Complexity of Security Stacks
Cybersecurity budgets are increasing each year, with Gartner predicting global security spending to reach $215 billion by 2025. Organizations are purchasing tools for:
- Endpoint security
- Network monitoring
- Identity and access management
- Threat intelligence
- SIEM (Security Information and Event Management)
- Vulnerability management
- Patch management
- Cloud security
While this sounds like a comprehensive defense, reality is far messier. Security teams are juggling multiple dashboards, alerts, and configurations. More tools mean more complexity, which means more room for errors.
Stat Check: The Problem with Too Many Tools
- 76% of security teams say they are overwhelmed by alerts from multiple tools (Cisco 2023 Security Outcomes Report).
- 79% of organizations use more than 10 security tools, leading to integration challenges (IBM Security Report).
- 67% of enterprises admit to having overlapping security tools with redundant capabilities (Forrester Research).
Why More Security Tools Create More Risk
1. Alert Fatigue: Too Many Alarms, Too Little Action
Security teams deal with an overwhelming number of alerts daily. A typical SOC (Security Operations Center) receives over 10,000 alerts per day. When analysts are bombarded with constant notifications, critical threats get buried in the noise.
Example: In 2021, a major financial institution suffered a data breach despite having over 50 security tools. The breach occurred because the security team ignored an alert, one of thousands received that day.
2. Lack of Integration: Siloed Security Tools Create Blind Spots
Each cybersecurity tool has its own dashboard, log format, and response mechanism. If they don’t communicate effectively, security teams must manually piece together insights, increasing response time.
Stat: 42% of security breaches occur due to lack of integration between security tools (Cybersecurity Insiders Report).
3. Skill Gap: More Tools, More Training, More Complexity
Organizations struggle to hire cybersecurity professionals, with an estimated 3.5 million unfilled security jobs worldwide (Cybersecurity Ventures). Every new tool requires specialized knowledge, training, and maintenance—which most companies don’t have the resources for.
Example: A healthcare provider installed a new SIEM system but failed to configure it properly due to a lack of expertise. As a result, a ransomware attack went undetected for weeks.
4. Increased Attack Surface: More Tools, More Vulnerabilities
Every security tool requires updates, patches, and monitoring. If one of these tools has a vulnerability, it can be exploited.
Stat: 25% of security breaches in the last three years were caused by vulnerabilities in security tools themselves (Gartner Research).
The Cost of Cybersecurity Overload
Security tools are expensive, yet they often fail to deliver value when mismanaged. Let’s break down the hidden costs:
- Financial Cost
- Large enterprises spend an average of $18 million per year on cybersecurity tools (Accenture Report).
- 50% of CISOs say they don’t use half of their security tools effectively (Ponemon Institute).
- Productivity Cost
- Security analysts spend 40% of their time managing tools instead of investigating threats (Forrester Research).
- 60% of security teams say tool complexity slows down response times (Cybersecurity Insiders).
- Risk Cost
- More tools mean more misconfigurations, and misconfigurations are responsible for 80% of breaches (IBM Data Breach Report).
How to Simplify Cybersecurity Without Compromising Security
1. Consolidate Your Security Stack
Instead of using 10 different tools for different security functions, look for platforms that combine multiple capabilities (e.g., unified vulnerability and patch management).
Example: Companies using a single integrated security platform reduced breach risk by 40% (IBM Security Report).
2. Prioritize Interoperability
Before purchasing a new tool, ensure it integrates well with existing systems. Look for solutions with API support and automation capabilities.
3. Focus on Risk-Based Vulnerability Management
Instead of chasing every vulnerability, prioritize those actively being exploited or impacting critical assets.
Example: Risk-based patching reduced breach likelihood by 76% compared to traditional CVSS-based patching (Cybersecurity Ventures).
4. Automate Where Possible
Use automation for patch management, threat detection, and remediation to reduce manual workloads and speed up response times.
Example: Companies using automated patching reduced remediation times from 45 days to just 5 days (Forrester Research).
5. Reduce Alert Fatigue with AI-Driven Security Tools
AI-driven threat detection filters out false positives, reducing the noise security teams deal with daily.
Stat: AI-powered cybersecurity reduced alert overload by 72% in organizations that implemented it (McKinsey Report).
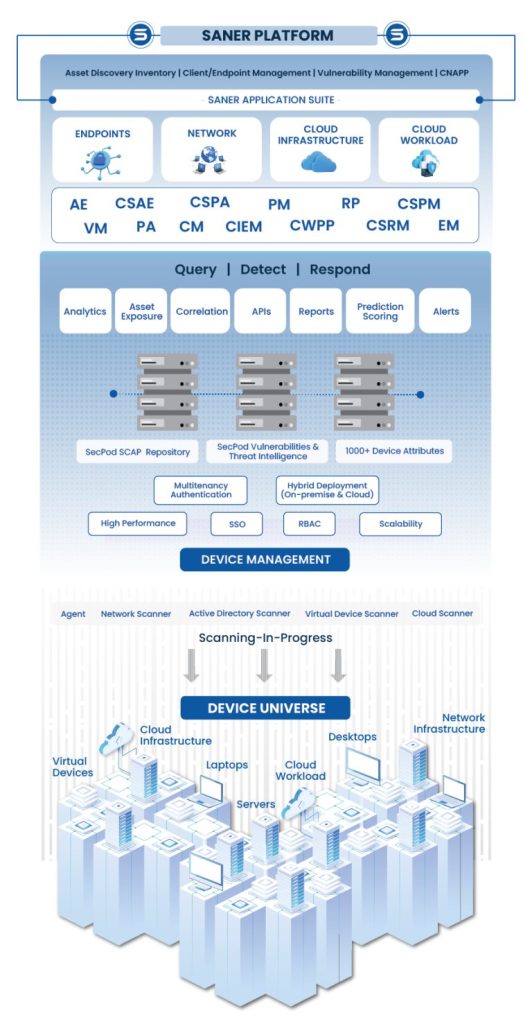
Saner Platform
SecPod’s Saner Platform provides continuous AI-driven protection across endpoints, server, network infrastructure, cloud infrastructure, cloud workload, and distributed IT infrastructure eliminating security gaps before attackers can exploit them.
The Saner Platform is the industry’s first truly unified cyber hygiene solution, combining Saner CVEM & Saner Cloud. Backed by innovation and deep intelligence from SecPod Research Labs, the Saner Platform delivers continuous security, automated remediation, and policy-driven compliance, all from a single integrated console.
Conclusion
Less is More in Cybersecurity. Security leaders must shift their mindset from “more tools = better security” to “simpler security = stronger security.” The goal is to create a cohesive, well-integrated security strategy rather than a fragmented collection of tools. Too many tools increase complexity, reduce efficiency, and create security gaps. Integrated, automated, and risk-based tools like Saner lead to better protection. A leaner security stack = fewer alerts, faster responses, and lower costs. The best cybersecurity strategy isn’t about how many tools you have. It’s about how well you use them.