The CVE-2021-21972 remote code execution vulnerability was reported by Mikhail Klyuchnikov from Positive Technologies. A vulnerability management tool discovered this. The organization also published a detailed write-up for this vulnerability to share the impact of the flaw.
VMware vCenter and vSphere allow the centralized management of virtual corporate infrastructure. Virtualization used to create and manage multiple VMs (Virtual Machines). Due to the vast popularity of VMware, widely used, and therefore thousands of vulnerable targets easily found.
CVE-2021-21972 Details
The remote code execution flaw exists in the vropspluginui plugin. This plugin improperly configured to allow any (unauthorized) user to access any URL it handled. A patch management tool can patch this vulnerability.
The function uploadOvaFile,responsible for the URI /ui/vropspluginui/rest/services/uploadova which can be used to upload tar files. The code that processes the tar files is not filtering the names of the tar files properly. Instead, simply concatenated with the string “/tmp/unicorn_ova_dir” which results in the creation of a file to the specified location.
With the above understanding, an attacker could create an archive entry containing the string “../”, which would allow uploading an arbitrary file to an arbitrary directory on the server. For illustration, a demo file “a.tar” archive containing a file with the name “..\..\testFolder\testUpload.txt“ is uploaded to the URL “/ui/vropspluginui/rest/services/uploadova“. Thereafter, uploading, checking server’s file system for the presence of testFolder and its nested file in the C:\ root directory.
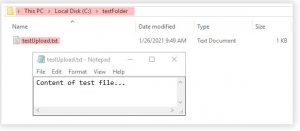
Credits: Positive Technologies
Now, to get the RCE(remote code execution) on Windows. The attacker would need to upload a malicious .jsp file to a location that is writable/accessible in the web-root directory and not requiring authorization. The directory “C:\ProgramData\VMware\vCenterServer\data\perfcharts\tc-instance\webapps\statsreport\” looks agile for this purpose. An attacker would now just need to create and upload a specially crafted .jsp file to execute commands on the system.
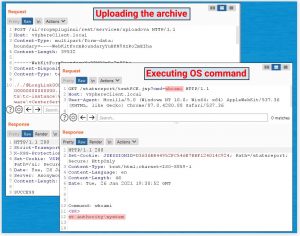
Credits: Positive Technologies
The malicious .jsp file uploaded to the server, and as seen above, it used to execute arbitrary commands on the system with NT AUTHORITY\SYSTEM privileges.
On the other hand, to get the code execution on Linux. The same understanding used by the attacker to upload ssh public key to the user’s home directory on the server. That later used to log in via ssh using the private key and achieve remote code execution.
Available PoC’s
There are many proof-of-concept(PoC) codes that are now widely available. Some of them listed below:
- https://swarm.ptsecurity.com/unauth-rce-vmware/
- https://github.com/horizon3ai/CVE-2021-21972
- https://github.com/QmF0c3UK/CVE-2021-21972-vCenter-6.5-7.0-RCE-POC
Impact of CVE-2021-21972
Successful exploitation of the vulnerability allows remote code execution, which further used to compromise the affected systems completely.
Affected Products by CVE-2021-21972
- VMware vCenter Server (7.x before 7.0 U1c, 6.7 before 6.7 U3l and 6.5 before 6.5 U3n)
- VMware Cloud Foundation (4.x before 4.2 and 3.x before 3.10.1.2)
Solution
VMWare has fixed the flaw stating the details in the advisory. Affected users can upgrade to :
- VMware vCenter Server 7.0 U1c, 6.7 U3l, 6.5 U3n, or later
- VMware Cloud Foundation version 4.2, 3.10.1.2, or later
SanerNow’s software deployment capability used to install executables/scripts.


