Three new security vulnerabilities have recently been identified in various SolarWinds products. Three of the vulnerabilities are severe, and the most critical of them allows remote code execution with high privileges. A vulnerability management tool discovered these critical vulnerabilities. Martin Rakhmanov, Security Research Manager, SpiderLabs at Trustwave, had found the bugs and reported them to the vendor. Trustwave also mentioned that none of the vulnerabilities exploited during recent SolarWinds attacks or “in the wild” attacks.
A Proof-of-Concept (PoC) code for all the three vulnerabilities is expected to be released by the founder of the bugs on the 9th of February, 2021. The two sets of vulnerabilities are reported to the SolarWinds in Orion and Serv-U FTP on December 30, 2020, and January 4, 2021. Following which bugs have been resolved by the company on January 22 and January 25 using a patch management tool.
Three vulnerabilities tracked as CVE-2021-25274, CVE-2021-25275, CVE-2021-25276.
Vulnerabilities Details
CVE-2021-25274, MSMQ Remote Code Execution in the SolarWinds Orion Platform. The improper use of Microsoft Messaging Queue (MSMQ) by SolarWinds Orion Collector Service leads to an issue. It allows an unauthenticated, remote attacker to send messages to these queues over TCP port 1801. Further, it chained with a deserialization issue in the code, which handles incoming messages to perform remote code execution (RCE).
Martin Rakhmanov said,
Given that the message processing code runs as a Windows service configured to use LocalSystem account, we have complete control of the underlying operating system
The patch provided by the vendor to address this issue performs a digital signature validation step on arrived messages. However, MSMQ is still unauthenticated, and anyone can message it.
CVE-2021-25275, Unprivileged users can get DBO owner access in the Orion Platform. The software uses a backend database named “SOLARWINDS_ORION“, credentials of which stored in a configuration file.
Image: Complete control over the SOLARWINDS_ORION database
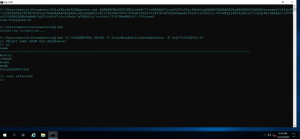
This could allow a local or unprivileged user to add a new admin-lever user, steal information, or take complete control over the database.
At last, CVE-2021-25276, Weak ACLs Vulnerability in SolarWinds Serv-U FTP Server 15.2.1 on Windows. This issue allows any attacker that can log into a system locally or via remote desktop to drop a file that defines a new user and Serv-U FTP will use it automatically.
Since the attacker can create any Serv-U FTP user, it will be easier for an attacker to define an admin account by setting a simple field in the file and may set the home directory to the root of C:\ drive. Since the FTP server runs as LocalSystem, now the attacker can log in via FTP and read or replace any file on the C drive.
Affected Products
- SolarWinds Orion Platform
- SolarWinds Serv-U FTP Server 15.2.1 and prior versions on Windows.
Solution
SolarWinds has released the fixes for both products. Users can get the fixes by installing Orion Platform 2020.2.4 and by applying Hotfix 1 for ServU-FTP 15.2.2. It highly recommended to install the patches.
SanerNow software deployment capability used to install executables/scripts.