What is modern IT Security without a vulnerability management tool? Severely limited, crippled, and not contemporary. The key goal of vulnerability management tools is to reduce your attack surface. They are critical weapons for IT and security teams to combat and prevent cyberattacks. From scanning for security risks and vulnerabilities to remediating them, these tools play an essential role in strengthening the cybersecurity posture. In this blog, we’ll cover key topics that include things to keep in mind while choosing a tool and what the top vulnerability management tools of 2024 are.
Things To Keep in Mind While Choosing a Vulnerability Management Tool
Choosing a vulnerability management tool can be pivotal for IT Security teams and leaders. So here are some key pointers to keep in mind while choosing one.
- A Regularly Updating Database:
New vulnerabilities are discovered every day, and cyber attackers try to exploit these risks at a higher priority. A vulnerability management database with an outdated database can be severely limited in detecting and mitigating newer risks. A good tool should have a continuously updating vulnerability database.
- Broader Security Risks Detection:
Cyberattacks don’t just exploit vulnerabilities anymore. Other risks like misconfigurations, exposures, and posture anomalies are gaining popularity and becoming increasingly dangerous. A good vulnerability management tool must be able to detect and accommodate risks beyond just CVEs.
- Swift Risk Prioritization:
Research suggests the projected number of CVEs in 2024 to be well over 35000! With the number of vulnerabilities rising exponentially, prioritization of risks is the only way to manage and mitigate security risks practically. A good vulnerability management tool must prioritize risk effectively based on criticality, business impact, and other factors.
- Integrated Risk Remediation:
Vulnerability management is detection AND remediation. If a vulnerability management tool can’t remediate the risks it detects, it severely limits its capabilities at ‘managing’ risks and becomes a vulnerability scanner. A good vulnerability management tool must be able to remediate the risks it detects with patches or other mitigation methods.
- End-to-End Automation:
It is impractical to manually manage the humongous amount of security risks in the modern IT infrastructure. Automation is critical to effectively eliminate the manual efforts needed to manage the detected security risks. A good vulnerability management tool must be able to automate the detection and remediation of security risks.
Top Vulnerability Management Tools for 2024
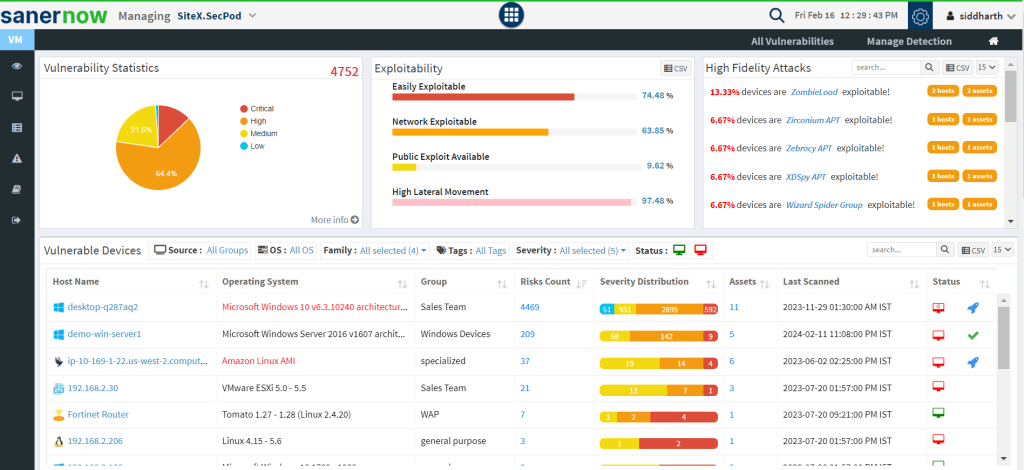
- SecPod SanerNow:
SecPod SanerNow is a Continuous Vulnerability & Exposure Management platform that detects, assesses, prioritizes, and remediates vulnerabilities and other security risks beyond CVES in a unified console. It’s an excellent vulnerability and exposure management tool for IT Security teams looking for.
SanerNow is powered by the world’s largest in-house vulnerability repository with over 175,000+ checks, the world’s first CISA’s SSVC-based Risk Prioritization, and integrated & automated remediation to simplify and speed up vulnerability management. It ticks all the right things you should remember while selecting a vulnerability management tool
- NMAP:
NMAP is an open-source vulnerability management tool that excels in risk detection. It can detect vulnerabilities, misconfigurations, ports, and other risks but lacks integrated remediation. Further, it doesn’t feature a UI and is challenging to use. Additionally, its lengthy and resource-consuming scans make it a 2nd choice for teams looking for a VM tool.
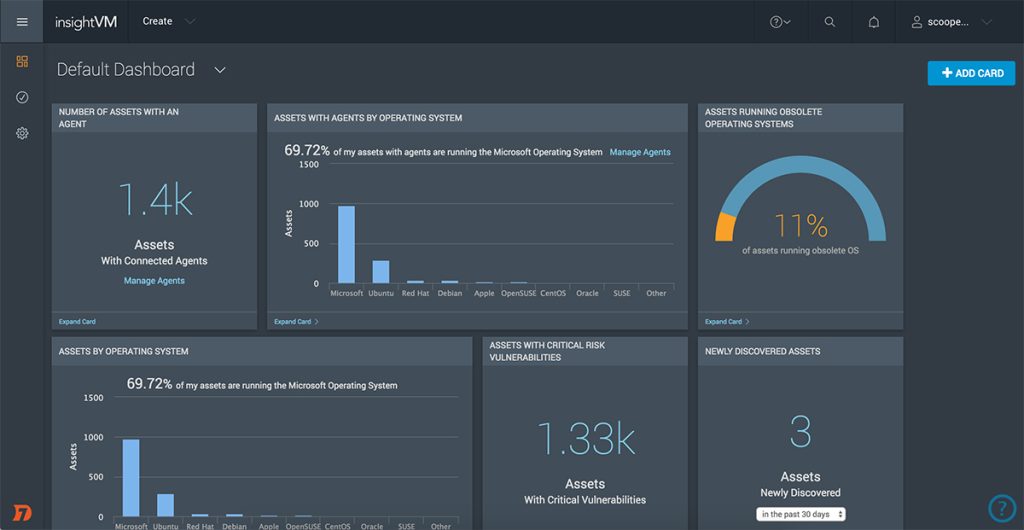
- Rapid7 InsightVM:
InsightVM is Rapid7’s offering for vulnerability management that can quickly scan your network and remediate risks with other products in its suite. While the scans are quick, InsightVM is known to have false positives in its scan results, leading to reduced accuracy. Nonetheless, it is a popular tool among IT security teams.
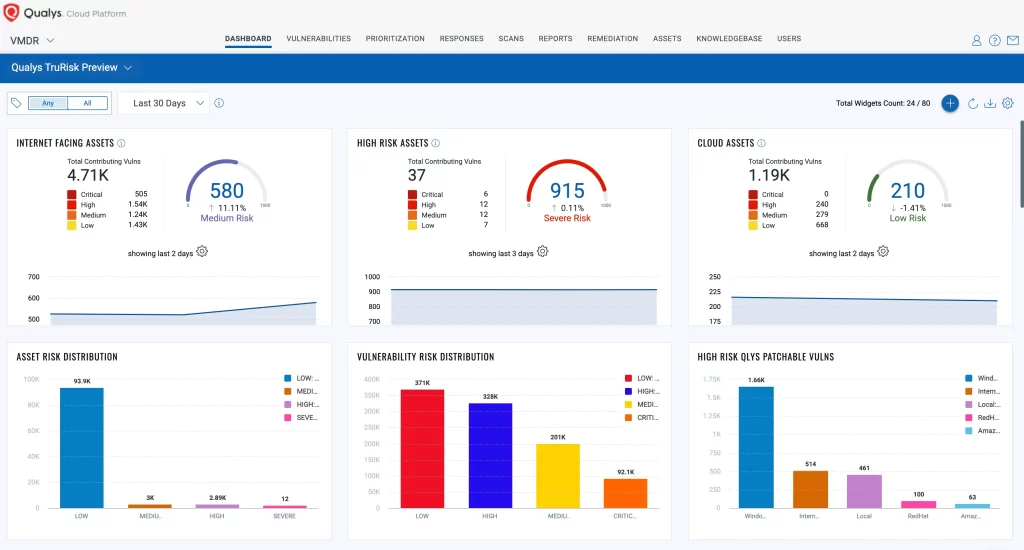
- Qualys VMDR:
Qualys is one of the oldest cloud-based vulnerability scanners in the market. Powered by an extensive vulnerability database, it provides relatively accurate scan results of vulnerabilities in your network. However, an additional tool called Qualys flow is needed to automate and remediate the detected risks, making the user experience a little complicated.
- Tenable One:
Tenable is another well-established vulnerability scanner supported by an extensive database and active community. One of the most popular scanners in the market, Tenable supports both cloud and physical networks. While its scans are accurate, its high scan duration and lack of integrated remediation mean it’s at the bottom of our list.
Conclusion
Vulnerability management tools have risen in popularity in recent times. With the rise in cyberattacks, more and more organizations are looking to protect themselves from potential cyberattacks, and these tools are critical for prevention.
So, choosing the right one can help transform your IT security and strengthen your security posture.


