According to statistics, a new cyberattack was detected every 39 seconds in 2023! With this rise in number of attacks, protecting sensitive data becomes crucial and challenging.
To protect IT, vulnerability scanners are the lead at defense, actively identifying weaknesses within systems and networks. However, due to the multiple vulnerability scanners in the market, the seriousness with which organizations approach scanners is underscored.
How do you make sure you have chosen the right vulnerability scanning tool?
6 Things to Keep in Mind While Selecting a Vulnerability Scanning Tool
1. Automated and continuous: Vulnerability scanning tools should offer continuous scanning capabilities, allowing real-time monitoring of your IT. It should also support automation to ensure scans occur regularly without manual efforts to reduce the attack surface.
2. Detection of Vulnerabilities Beyond CVEs: While CVEs are important, a scanning tool should go beyond CVEs and find other security risks, including misconfigurations, exposures, missing patches, and posture anomalies.
3. Accuracy of Scans: A vulnerability scanning tool’s performance depends on its scan’s accuracy. The scanning results should have a very low percentage of false positives. Also, choose a tool known for its accurate identification and reporting capabilities to minimize the chances of cyberattack.
4. Time to complete scans: A scanning tool should conduct complete scans within reasonable time, reducing disruption to ongoing operations. Moreover, balancing accuracy with speed is a must to identify and fix critical vulns on time without any delays.
5. Integration: Just having a vulnerability scanning tool isn’t enough in this ever-growing landscape. You need to have an integrated patching alongside to fix vulns instantly.
6. Adopting CVEM: Have a vulnerability scanning tool that adapts the “continuous vulnerability and exposure management” concept. Also,CVEM states that it should have a continuous, automated, and integrated vulnerability management process that discovers vulns beyond CVEs and fix instantly.
Top Vulnerability Scanning Tool for 2024
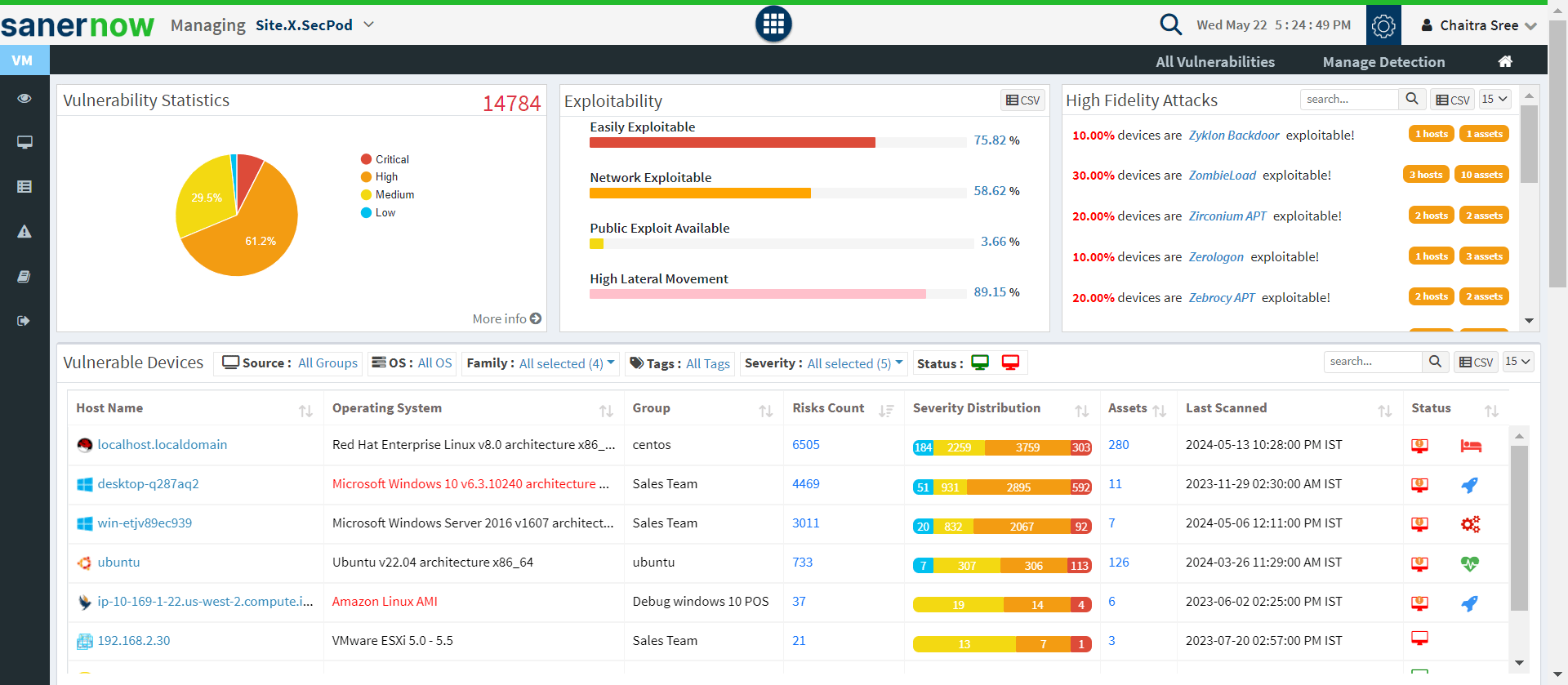
1. SanerNow CVEM: SecPod SanerNow vulnerability scanner does the industry’s fastest 5-minute scans. It supports all major OSs, including Windows, Linux, macOS, and 550+ third-party applications. It scans for vulnerabilities beyond CVEs, such as misconfigurations, anomalies, missing patches, exposure, etc.
Moreover, SanerNow utilizes lightweight and intelligent agent to perform scans seamlessly. The scanner also has the option to opt for agentless scanning.
Furthermore, SanerNow has support from the world’s largest SCAP repo with 190,000+ vulns checks and is also the world’s first CISA-SSVC-based risk prioritization model. It ticks all the boxes for the right vulnerability scanning tool.
Pro: Continuous, accurate, automated, fastest, integrated with patch management, and supports all major OSs and 3rd party applications.
Con: Authenticated scan capabilities is limited.
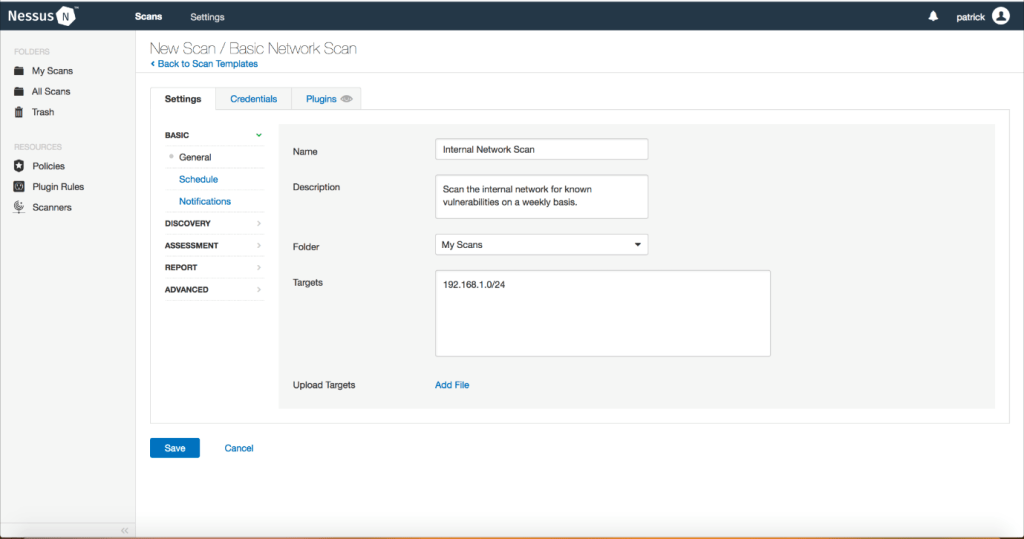
2. Tenable: Tenable’s vulnerability scanner, Nessus, identifies all the vulnerabilities present in your network. Moreover, it is supported by a well-established database and provides coverage scanning for 59,000 CVEs.
Also, it also scans IoT, OT, and web applications and also provides preconfigured templates to enable quick starts.
Pro: Good coverage for CVEs.
Con: Expensive, difficult to navigate through, and scalability issue.
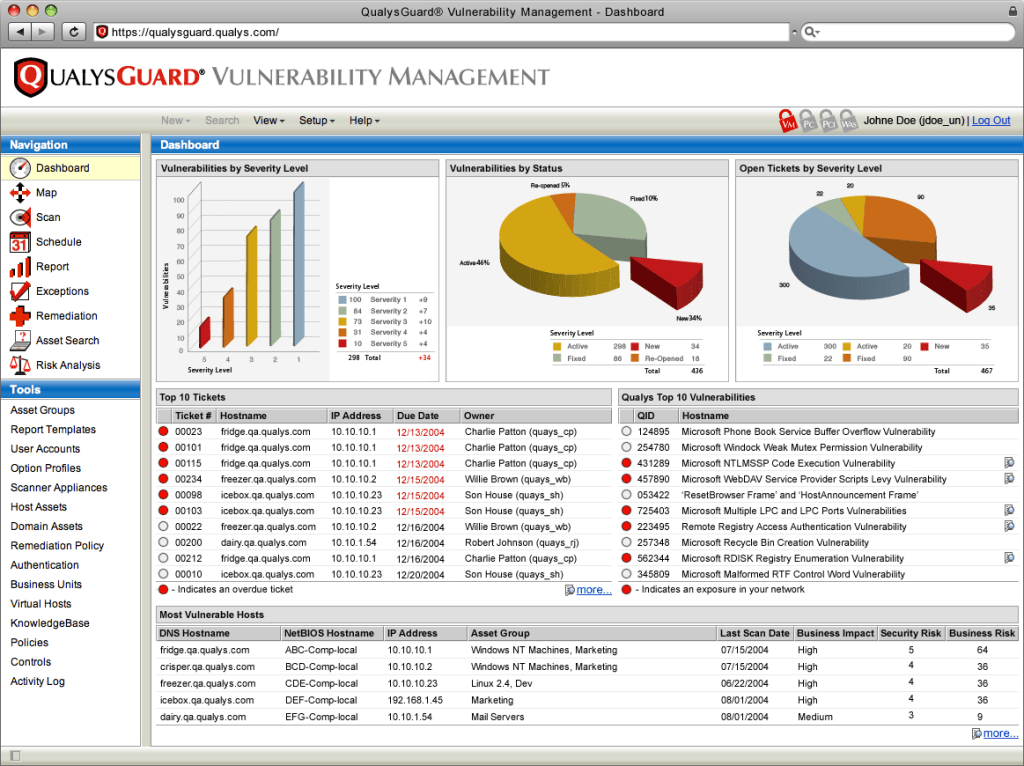
3. Qualys: It has two scanners, one qualys guard for cloud application and another qualys web application scanner. It scans IT, OT, and IoT devices and all applications, including cloud instances and APIs for mobile devices.
Also, it allows for quick discovery, prioritization, and automatic fixing of vulnerabilities and can be integrated with ITSM tools.
Pro: Good vulnerability scanning range.
Con: Complex to set up. Configure limited customer support.
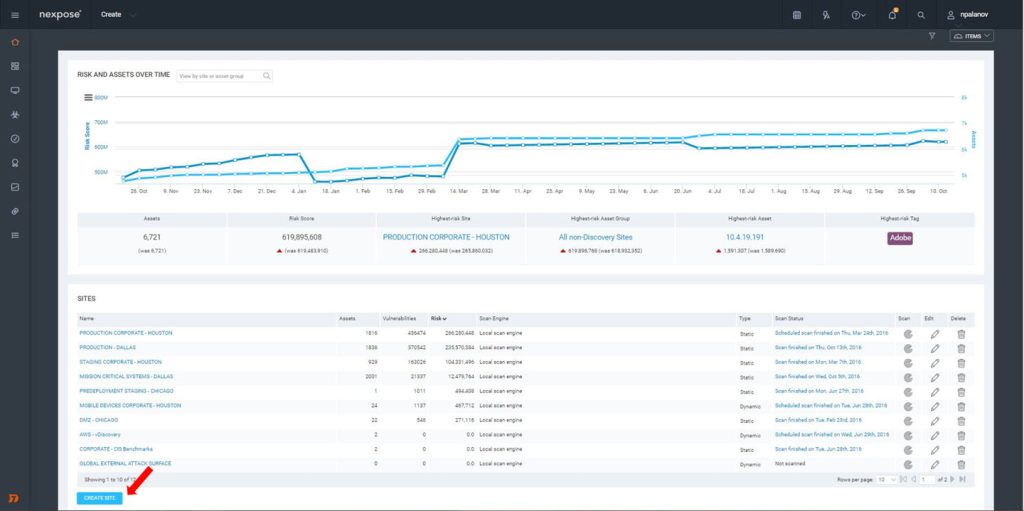
4. NexPose Rapid 7: Open-source web application vulnerability assessment tool used for scanning vulns, offering support for a diverse array of network assessments as well.
Also, it provides network scans to discover risks across all endpoints and on-premises infrastructure.
Pro: Robust scanning capabilities and good for large-scale environments.
Con: Integrates only with other Rapid7 products, complex to set up, high number of false positives.
5. OpenVAS: Free vulnerability scanning tool that identifies vulns across web platforms. It boasts a robust internal programming language, enabling precise identification of vulns locations, and supports both authenticated and unauthenticated scanning.
Furthermore, OpenVAS receives updates to enhance its ability to detect vulns across IT. These updates assist in risk assessment and also provide recommendations for fixing the identified vulns.
Pro: Open-source, free to use, and good for small organizations.
Con: Less user-friendly and lacks advanced features.
6. Burpsuite: Burp Suite community offers free, yet feature-restricted tools coupled with manual pen testing; the Burp Suite Enterprise Edition delivers automated dynamic web vulnerability scanning capabilities.
Burp Suite Professional ($449 per user per year) and Enterprise Edition (starting at $8,395 per year) are also available
Pro: Good for web application security testing
Con: Focused primarily on web applications, may not provide comprehensive vulns scans
7. Acutenix: It is a web vulns scanner known for its advanced technology, capable of uncovering vulns across various web pages. It prioritizes both speed and precision in its scans.
Acutenix comes in three versions: Small Business, Enterprise, and Consultant. The Small Business version caters to organizations with a single website. The Enterprise version is tailored for organizations managing multiple websites, while the Consultant version is designed for organizations conducting scans on numerous customer websites.
Pro: Offers both vulns scanning and patch management capabilities
Con: Complex to manage, high number of false positives, and limited scanning performance.
8. GFI languard: GFI Languard Software serves as a network and web application scanner. It identifies and scans devices to detect any missing patches in operating systems as well as third-party software.
Also,GFI LanGuard patches Microsoft, macOS, Linux, and 50 3rd party applications and deploys both security and non-security patches
Pro: Provides good vulnerability scanning and patch management for Windows and third-party applications.
Con: Lacks advanced features, other OS support.
Conclusion
As cyber threats continue to escalate, vulnerability scanning tools have become increasingly popular for organizations protecting themself from attacks. The decision to select the appropriate tool is crucial for your digital assets. These scanners have the power to enhance your IT security and overall cyber defense. Therefore, choosing the right one will give you an attack-free 2024.


