“Attackers? Good luck getting past my VPN wall!”. Maybe it’s time to reconsider that. New research just uncovered security vulnerabilities in multiple tunneling protocols that could allow attackers to perform a wide range of attacks in your “private” network.
What are Tunneling Protocols?
Tunneling protocols such as IP-in-IP (IPIP) and Generic Routing Encapsulation (GRE) are foundational in linking otherwise disconnected networks and forming Virtual Private Networks (VPNs) to facilitate seamless communication between them.
In networking, a tunnel is a method to transfer data between disconnected networks. From a general aspect, tunneling protocol encapsulates packets and sends them to the receiver. The receiver will strip the outer header and acquire the original encapsulated packet which can then be forwarded. Tunneling protocols are usually utilized to transport layer two frames or later three packets.
What’s the issue with these protocols?
These protocols have a key limitation: they don’t authenticate or encrypt traffic, leaving data vulnerable to interception. To secure them, they must be combined with Internet Protocol Security (IPsec) for encryption and authentication. However, these protocols are often implemented without additional security.
The poor implementation and way of managing traffic paves the way for attackers to inject malicious traffic into a tunnel, a variation of a vulnerability that was previously identified as CVE-2020-10136. The recently discovered vulnerabilities have been assigned the following CVEs corresponding to the protocols affected:
- CVE-2024-7595: GRE and GRE6 Protocols (RFC2784) do not validate or verify the source of a network packet, allowing an attacker to route arbitrary traffic via an exposed network interface that can lead to spoofing, access control bypass, and other unexpected network behaviors.
- CVE-2024-7596: Proposed Generic UDP Encapsulation (GUE) (IETF draft-ietf-intarea-gue*) does not validate or verify the source of a network packet, allowing an attacker to route arbitrary traffic via an exposed network interface that can lead to spoofing, access control bypass, and other unexpected network behaviors.
- CVE-2025-23018: The IPv4-in-IPv6 and IPv6-in-IPv6 protocols (RFC2473) do not require the validation or verification of the source of a network packet, allowing an attacker to route arbitrary traffic via an exposed network interface that can lead to spoofing, access control bypass, and other unexpected network behaviors.
- CVE-2025-23019: The IPv6-in-IPv4 protocol (RFC4213) does not require authentication of incoming packets, allowing an attacker to route traffic via an exposed network interface that can lead to spoofing, access control bypass, and other unexpected network behaviors.
How do they affect hosts?
Internet hosts that accept tunneling packets without verifying the source’s identity are at risk of being hijacked. Many hosts also allow spoofed packets, masking the attacker’s IP and enabling anonymous attacks.
Exploiting these vulnerabilities, attackers can inject malicious traffic into private networks, execute DoS or SYN flood attacks, and even hijack off-path TCP sessions. These vulnerabilities can also turn hosts into one-way proxies, amplifying attacks and consuming critical system resources, ultimately disrupting service availability and causing full-scale Denial of Service (DoS).
Method of Attack:
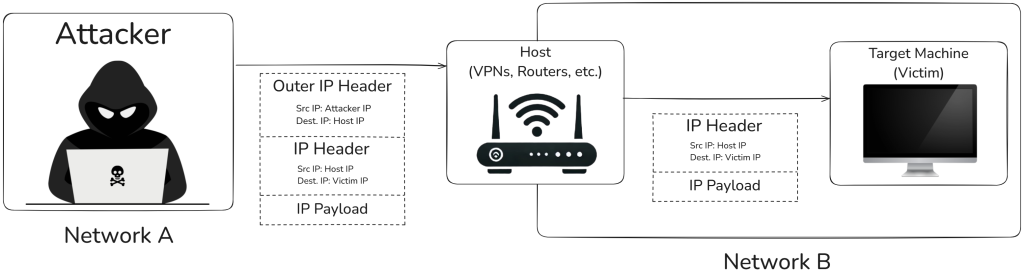
- An attacker sends a packet encapsulated using one of the affected protocols with 2 IP headers. The outer header contains the attacker’s source IP with the vulnerable host IP as destination.
- The inner header’s source IP is that of the vulnerable host IP rather than the attacker’s IP and the destination IP is that of the target (victim) of the anonymous attack
- When the vulnerable host receives the malicious packet, it strips the outer IP address header and forwards the inner packet to its destination.
- Since the source IP address on the inner packet is that of the vulnerable host, it is able to get past network filters.
Possible Attacks:
- Ping-pong amplification Attack
- Tunneled-Temporal Lensing (TuTL)
- Routing Loop DoS
- Abusing Abuse Reports
- DoS techniques and DNS spoofing, which in turn enables traditional DoS attacks
- off-path TCP hijacking
- SYN floods
- Certain WiFi attacks.
Affected Hosts:
- VPN Servers
- ISP home routers
- Core internet routers
- Mobile network gateways and nodes
- CDN nodes
Affected Protocols:
| Protocol | Protocol Number in IP Header |
| IPIP (IP in IP) | 4 |
| IP6IP6 (IPv6 in IPv6) | 41 |
| GRE (Generic Routing Encapsulation) | 47 |
| GRE6 (GRE over IPv6) | 47 |
| 4in6 (IPv4 over IPv6) | 41 |
| 6in4 (IPv6 over IPv4) | 41 |
| GUE (Generic UDP Encapsulation) | No specific protocol number. Typically uses UDP port numbers, port 6080 by convention |
How should you defend yourself?
Host-level Defense:
- Only Accept tunneling packets from trusted sources.
- However, Spoofing would evade this defense.
- Use more secure tunneling protocols.
- It is recommended to use IPSec or WireGuard to provide authentication and encryption to only accept tunneling packets from trusted and verified sources.
Network-level Defense:
- Implement traffic filtering on routers and middleboxes
- These tunneling protocols can be identified by the protocol number used in the IP packet.
- For example, IPIP used protocol number 4. Thus, filtering can be done based on the protocol number, such as if “ip.proto == 4” then the packet should be rejected or dropped.
- Deep packet inspection (DPI). DPI analyzes the contents of packets to identify malicious or unencrypted tunneling traffic.
- Block all unencrypted tunneling packets.
Tunneling protocols are essential for modern networking, but their vulnerabilities expose millions of hosts to serious risks. By implementing stronger security measures, such as IPSec or WireGuard, and filtering unverified traffic, we can safeguard critical infrastructure and private networks. Addressing these weaknesses is key to ensuring a safer and more resilient internet.
Instantly Fix Risks with SanerNow Patch Management
SanerNow patch management is a continuous, automated, and integrated software that instantly fixes risks exploited in the wild. The software supports major operating systems like Windows, Linux, and macOS, as well as 550+ third-party applications.
It also allows you to set up a safe testing area to test patches before deploying them in a primary production environment. SanerNow patch management additionally supports a patch rollback feature in case of patch failure or a system malfunction.
Experience the fastest and most accurate patching software here.


