A Cloud-Native Application Protection Platform (CNAPP) is a unified security solution that protects cloud-native applications from development to runtime. Cloud computing has transformed application deployment and management for the better, but it also brings unique security complexities, particularly in dynamic and distributed cloud-native environments. Traditional security tools struggle with the short-lived nature of these infrastructures, leaving gaps that attackers can exploit.
To address these challenges, CNAPPs offer integrated tools designed to secure cloud-native workloads. It combines features like workload protection, configuration management, and runtime threat detection to tackle modern cloud security challenges effectively.
But what makes a CNAPP so revolutionary? Unlike traditional security systems that operate in silos, CNAPPs offer centralized security visibility and control for the entire cloud-native application lifecycle, enabling organizations to stay ahead of emerging threats.
If you want for a shortcut to obtaining the most powerful cloud security, look no further than Saner Cloud, SecPod’s new AI-fortified CNAPP solution.
This blog will go deep into the key capabilities of CNAPPs, how they enhance organizational security, the benefits they deliver, and their implementation strategies.
What Does a CNAPP Solve?
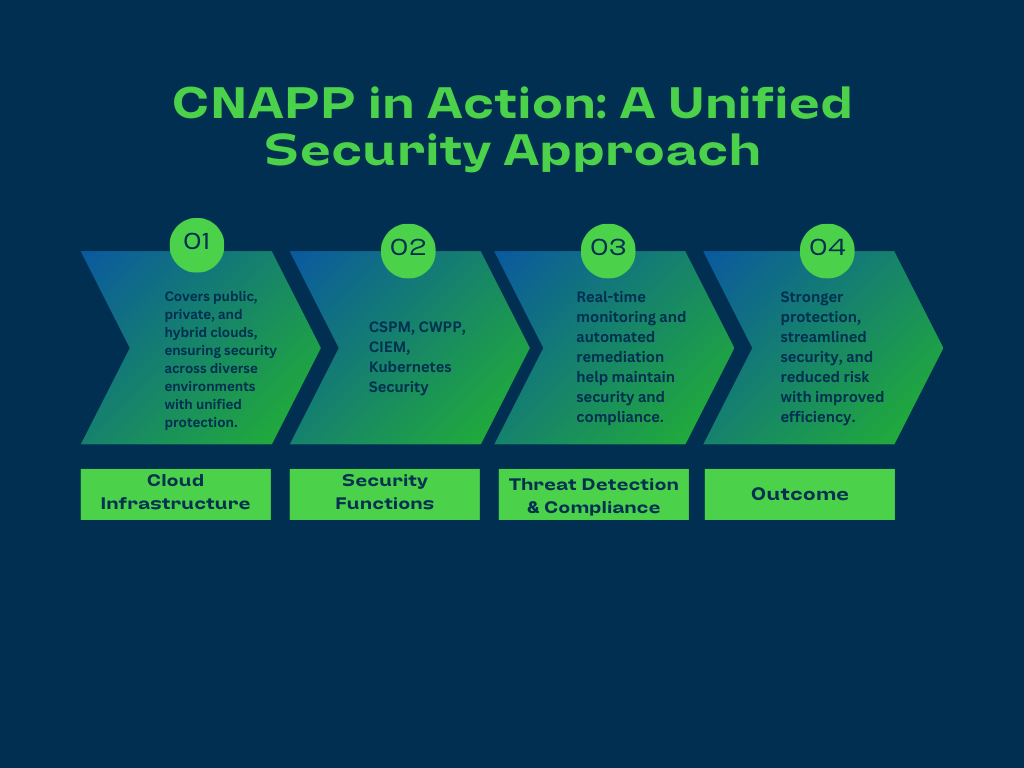
CNAPPs address fundamental challenges in cloud security by unifying security efforts across the entire application lifecycle. Traditionally, runtime and development security have been handled separately, using tools that often operated in silos and reacted only when a security event occurred. The fragmented approach slowed down cloud security and increased the risk of oversights. CNAPP solutions replace this outdated model with a unified process, aligning seamlessly with the speed and communication needs of modern development.
- Bridging Fragmented Security Efforts: Traditional cloud security tools operated in silos, with separate solutions for artifact scanning, runtime protection, and cloud configuration management. Each tool provided only partial visibility, creating blind spots and inefficiencies. CNAPP consolidates these functions, offering comprehensive insight into application and infrastructure security. A unified approach allows teams to assess risks in context, prioritize vulnerabilities effectively, and address security challenges holistically.
- Proactive Security with Continuous Monitoring: Earlier security models were largely reactive, identifying risks only after they had already surfaced. CNAPP moves security earlier in the development cycle by integrating threat detection at the code level while maintaining oversight during runtime. Automated scanning of artifacts and configurations helps prevent vulnerabilities from reaching production, reducing risks, and accelerating remediation efforts.
- Improved Visibility Across Development and Runtime: Limited visibility across cloud environments has long been a challenge, particularly with the complexity of cloud-native architectures and third-party integrations. CNAPP provides an end-to-end view of cloud assets, application components, and infrastructure. Security insights are consolidated into a single compliance-aligned dashboard, fostering collaboration between development, operations, and security teams.
- End-to-End Protection Without Gaps: Traditional security approaches often left gaps between development and production environments. CNAPP eliminates these gaps by maintaining security from code commit through runtime. Threats identified in production can be traced back to their source, streamlining remediation and strengthening cloud security posture. Consolidating security functions into a single platform reduces complexity and operational overhead.
- Automation and Integrated Workflows: Automation plays a central role in modern security operations. CNAPP integrates with CI/CD pipelines to support agile DevOps workflows, automating artifact scanning, configuration analysis, and runtime protection. Its compatibility with existing development and security tools enhances collaboration, allowing teams to address security concerns without disrupting workflows.
- Reducing Complexity and Improving Efficiency: Managing cloud security with disconnected tools consumes resources and slows development cycles. CNAPP simplifies security operations by consolidating necessary functions into a unified platform. Automated threat detection and mitigation allow teams to focus on innovation rather than reactive issue management, supporting faster deployment and more efficient cloud security practices.
- A Unified Approach to Cloud Security: CNAPP replaces fragmented security models with a continuous, integrated framework. It provides visibility, automation, and comprehensive security measures throughout the cloud-native application lifecycle. Treating security as an ongoing process rather than a series of isolated tasks, CNAPP equips organizations to manage cloud environments with greater confidence.
CNAPP Architecture and Functionality
CNAPPs are purpose-built to deliver integrated cloud security throughout the application lifecycle. Merging multiple security functions into a single platform reduces fragmentation and fosters collaboration among security, development, and operations teams. A unified design allows risks to be identified, prioritized, and mitigated in real-time.
Unified Dashboard and Reporting
A central dashboard provides visibility, management, and reporting across cloud environments, consolidating security insights into a single interface.
- Centralized Visibility Across Cloud Environments: CNAPPs offer a consolidated view of assets, workloads, APIs, and configurations across public, private, and hybrid clouds. Gaps in visibility are minimized, allowing security teams to monitor attack surfaces more effectively.
- Risk Prioritization and Scoring: Advanced analytics assess risks based on severity, potential business impact, and likelihood of exploitation. Security teams can focus on addressing high-priority vulnerabilities first, improving overall resilience.
- Compliance Reporting: Automated compliance checks align workloads with regulatory frameworks such as PCI DSS, GDPR, and HIPAA. Pre-built reporting templates streamline audits, reducing manual effort while maintaining comprehensive coverage of compliance requirements.
Value of a Unified Dashboard
A single dashboard consolidates information from multiple tools, reducing complexity and improving response times. Real-time insights support faster decision-making and help teams address high-priority threats without unnecessary delays.
Data Collection and Analysis
Sophisticated data collection and analysis capabilities form the backbone of CNAPP functionality. The architecture supports both agent-based and agentless methods, offering flexibility across different environments.
- Agentless vs. Agent-Based Approaches: Agentless scanning leverages cloud-native APIs and logs to reduce deployment overhead, while agent-based solutions provide deeper visibility into runtime states, including containers, virtual machines, and serverless environments.
- Machine Learning (ML) and Artificial Intelligence (AI) for Threat Detection: ML and AI models analyze trends, behaviors, and activities to identify unusual patterns. These capabilities improve the detection of previously unknown vulnerabilities while reducing false positives.
- Real-Time Monitoring and Alerting: Continuous monitoring detect deviations from baseline activities and security policies. Immediate alerts allow security teams to respond swiftly to emerging threats.
Impact of Data Collection and Analysis
Accurate and timely data analysis strengthens early threat detection, minimizes operational disruptions, and improves security posture. Combining agent-based depth with agentless agility creates a balanced approach, while AI-driven analytics refine detection accuracy.
Policy Management and Enforcement
Policy-driven security enforcement forms a core component of CNAPP architecture. Standardizing and automating security policies across cloud environments helps maintain consistency and reduces the risk of human error.
- Custom Policy Creation: Organizations can develop security policies tailored to their business needs, covering areas such as access controls, workload hardening, and infrastructure configurations.
- Policy-Driven Automation: Automated remediation enforces security policies by addressing misconfigurations, applying patches, and correcting deviations without manual intervention.
- Cross-cloud Policy Consistency: Policies remain consistent across multicloud environments, maintaining alignment between platforms such as AWS, Azure, and GCP. Gaps and configuration drift are reduced, minimizing exposure to vulnerabilities.
Role of Policy Management in Cloud Security
Standardizing policies across cloud environments improves efficiency and reduces risk. Automation streamlines security operations, allowing teams to respond to threats quickly while maintaining alignment with governance requirements.
Architectural Advantages of CNAPP
CNAPPs consolidate visibility, analytics, automation, and policy-driven security management into a unified system. Addressing the complexities of modern cloud-native environments allows organizations to reduce operational burden, mitigate risks more quickly, and improve security posture while maintaining business agility.
Benefits of CNAPP
CNAPPs have helped redefine cloud security strategies by consolidating core operational functionalities into a single, comprehensive solution. Here’s how CNAPP benefits organizations while addressing the complexities of modern cloud environments.
- Comprehensive Visibility: CNAPP provides a centralized view of cloud assets, consolidating data from services, containers, and virtual machines. Correlation and analytics help detect misconfigurations, compliance gaps, and anomalies, allowing teams to prioritize and address risks effectively across multicloud environments.
- Automated and Real-time Remediation: Security moves from reactive to proactive with automated vulnerability patching and incident response. CNAPP enables actions such as quarantining compromised instances, blocking malicious processes, and rolling back workloads without manual intervention, reducing response times and alleviating operational burdens.
- Integration with Development Pipelines: Embedding security early in the development lifecycle helps identify and resolve vulnerabilities before deployment. CNAPP supports container image scanning, infrastructure-as-code (IaC) analysis, and CI/CD security checks, fostering more secure and efficient DevSecOps practices.
- Ongoing Compliance and Governance: Meeting regulatory requirements is simplified through automated compliance checks for frameworks such as PCI DSS, GDPR, and HIPAA. CNAPP continuously maps cloud resources to compliance mandates, monitors for violations, and triggers corrective actions, reducing audit complexity and regulatory risks.
- Reduced Complexity and Costs: Integrating multiple security functions, including CSPM, CWPP, and SIEM capabilities, eliminates reliance on disparate tools. Consolidation minimizes operational overhead, simplifies tool management, and optimizes resource allocation, leading to more efficient security investments.
- Advanced Threat Detection and Response: CNAPP leverages analytics and real-time threat intelligence to detect and respond to sophisticated attacks. Correlating data across workloads, networks, and applications improves alert fidelity and investigation workflows, enabling faster risk mitigation.
Streamlined security across complex cloud environments enables CNAPPs to improve both operational efficiency and resilience. Organizations gain a structured approach to managing cloud security, balancing protection with agility.
Implementing CNAPP
Implementing CNAPP requires strategic planning and an awareness of potential obstacles. Addressing these challenges early improves adoption and effectiveness.
- Skill Gaps & Culture Shifts: Knowledge disparities across development, security, and operations teams can hinder adoption. DevOps engineers may be unfamiliar with security workflows, while security analysts may lack expertise in containerization or cloud-native environments. Addressing these gaps requires targeted training, cross-functional collaboration, and support from experienced vendors or consultants.
- Organizational Complexity: Siloed teams operating independently create friction when integrating CNAPP. Misaligned workflows and unclear responsibilities slow cloud adoption. Establishing shared goals, improving communication, and fostering collaboration between developers, operations, and security teams promotes a smoother transition.
- High Integration Effort: Merging CNAPP with existing cloud providers, repositories, and security tools can be resource intensive. A phased implementation strategy, supported by custom connectors or API integrations, helps streamline this process and prevent delays.
- Alert Fatigue & Data Overload: CNAPP generates vast amounts of security data, which, if not properly managed, can overwhelm teams with excessive alerts. Prioritization mechanisms and correlation workflows help filter noise, allowing security teams to focus on high-impact threats.
- Change Management Challenges: Adopting CNAPP requires more than technical adjustments — it demands organizational buy-in. Resistance to change can slow adoption. A structured roadmap with clear milestones fosters engagement and demonstrates both immediate benefits and long-term value.
A well-planned approach, supported by collaboration and adaptability, allows organizations to fully integrate CNAPP. This helps avoid common implementation pitfalls.
Advancing Cloud Security with CNAPP
CNAPP reshapes cloud security by consolidating fragmented tools into a unified framework that spans development and runtime. It enhances visibility, automates threat response, and aligns security with modern DevOps workflows. Successful implementation requires addressing skill gaps, integrating with existing environments, and managing alert volume effectively. Organizations that take a structured approach to adoption gain stronger security coverage while improving efficiency and scalability in cloud-native environments.
Ready to simplify your cloud security practices and take them to the next level? See how Saner Cloud is purpose-built to help achieve just that.