Staying a step ahead of potential threats is key to preventing devastating cyberattacks. One of the most effective ways to maintain this edge is through regular scanning reports. A scanning report is a snapshot of your enterprise’s vulnerabilities and risks at a given point in time. Cybersecurity is like a never-ending game of chess, and you need to think a few moves ahead to stay protected. One of the most powerful opening moves? Having a solid scanning report!
What is a Scanning Report?
Imagine running a health check on your computer systems, like a doctor checking your vitals to ensure you’re in good shape. A scanning report does exactly that for your IT infrastructure. The twist here? It isn’t checking for high blood pressure or cholesterol, it’s checking for vulnerabilities.
In simpler terms, a scanning report is a document that details the vulnerabilities and risks in your network, software, or systems. It’s the output you get after a “vulnerability scan”, which is done after inspecting your enterprises IT by identifying risks and threats. These reports categorize risks based on severity, potential impacts, and even suggest how to fix them.
Now, why does this matter? Let’s talk about why scanning reports are crucial.
Why Scanning Reports are crucial?
Imagine having a flashlight in a dark room. Without it, you’re entering blindly and are unaware of the dangers lurking in the corner.
But once you flip the switch, everything is visible and fixable. Reports work similarly, too! Here’s why these reports are necessary:
- Early Detection: The earlier you find a vulnerability, the faster you can fix it. Many attacks exploit known vulnerabilities that enterprises simply failed to address. A scanning report tells you where those issues are, so you can patch them up before a cybercriminal has the chance to strike.
- Prioritization: Not all vulnerabilities are created equal. Some are minor annoyances, while others are ticking time bombs. Scanning reports helps you prioritize by highlighting the most critical risks, so you know where to focus your efforts.
- Compliance Requirements: Regulations like HIPAA often mandate routine vulnerability scans. A scanning report serves as proof that you’re proactively managing security, which can be a lifesaver during audits.
- Risk Management: Vulnerability management isn’t about fixing everything at once, it’s about managing risk. A good report helps you do just that by providing a roadmap of what to tackle first and how to minimize potential damage.
- Continuous Improvement: Cyber threats evolve, so your defense strategies need to evolve, too. Regular scanning reports show you how your security posture is improving (or not) over time.
What a GOOD Scanning Report should look like
Not all scanning reports are equal, and a poorly constructed one can be more confusing than helpful. So, what should you look for in a quality scanning report?
- Comprehensive Coverage: A good report covers all critical areas of your IT environment, like servers, endpoints, networks, and applications. It should leave no stone unturned.
- Clear and Actionable Information: If the report reads like a foreign language, it’s not doing its job. The findings should be easy to understand, with detailed explanations of each vulnerability and the potential impact. Bonus points if it offers step-by-step remediation guidance.
- Risk Scoring and Prioritization: Look for a report that ranks vulnerabilities based on risk level, usually using a scoring system like CVSS and CISA’s SSVC. This way, you know which issues need immediate attention and which ones can wait.
- Customized Insights: Every enterprise is different. A good scanning report should offer insights specific to your IT environment, not just generic advice.
- Visualization Tools: Graphs, and dashboards can make a report easier to digest and more engaging. Visuals can quickly show trends or highlight critical areas.
- Remediation Suggestions: The report should not only identify vulnerabilities but also suggest practical ways to fix them. Whether it’s a patch or a configuration change, actionable insights make the report truly valuable.
- Compliance Mapping: If you’re in a regulated industry, the report should show how the findings relate to specific compliance requirements, like PCI-DSS or NIST standards.
This is How SanerNow Shows Reports
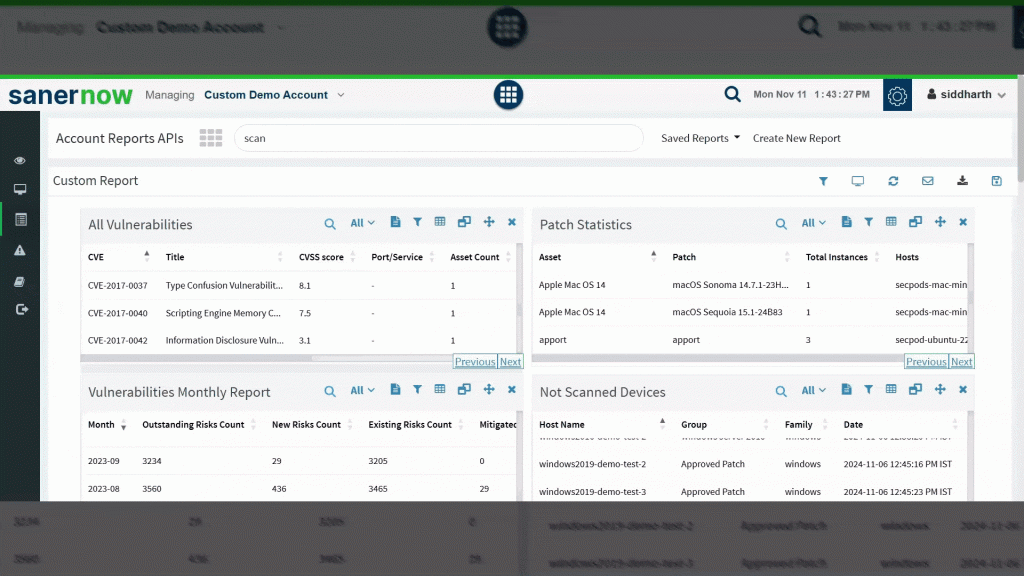
Conclusion
In the world of cybersecurity, knowledge is power, and a scanning report gives you that power. It sheds light on vulnerabilities, helps you prioritize and act, and keeps you ahead of threats. But to truly maximize the benefits, you need a robust, easy-to-understand, and actionable report.
With SanerNow, scanning and reporting are no longer daunting tasks. The platform transforms complex data into clear, manageable actions, ensuring that your cybersecurity is always a few steps ahead of potential cyber-attacks.


