VMware, the virtualization giant, has patched 19 vulnerabilities, including one critical vulnerability, ten important vulnerabilities, and eight moderate vulnerabilities, in its latest security advisory VMSA-2021-0020. The vulnerabilities tracked as CVE-2021-21991, CVE-2021-21992, CVE-2021-21993, CVE-2021-22005, CVE-2021-22006, CVE-2021-22007, CVE-2021-22008, CVE-2021-22009, CVE-2021-22010, CVE-2021-22011, CVE-2021-22012, CVE-2021-22013, CVE-2021-22014, CVE-2021-22015, CVE-2021-22016, CVE-2021-22017, CVE-2021-22018, CVE-2021-22019, CVE-2021-22020 are affecting the widely used VMware vCenter Server and VMware Cloud Foundation. VMware vCenter Servers Under Active Attack 2021. A vulnerability management tool can detect these vulnerabilities.
Successful exploitation of these vulnerabilities allows attackers to conduct code execution, sensitive information disclosure, privilege escalation, cross-site scripting, server-side request forgery, and denial of service. However, auto patching can mitigate these vulnerabilities.
VMware has also released a patch for an arbitrary file upload vulnerability (CVE-2021-22005) in its Analytics service, which is being exploited in the wild.
CVE-2021-22005 Actively Exploited In The Wild
A critical remote code execution vulnerability is found in the VMware vCenter. The flaw is due to an arbitrary file upload vulnerability in its analytics service. It allows attackers to execute commands and software on the vCenter Server Appliance. Anyone who can reach the vCenter Server over the network can use this vulnerability. It is to gain access irrespective of the configuration settings of the vCenter Server.
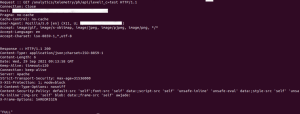
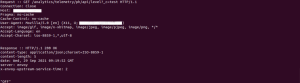
Below attached screenshot of a cURL request performed against the analytics service endpoint to identify vulnerable and non-vulnerable hosts:
Vulnerable host :
- Here Server responds with a 200/OK and anything other than ‘OFF‘ in the response body (such as ‘FULL‘)
Non Vulnerable host :
- Here Server responds with a 200/OK and body content of ‘OFF‘ in the response body. i.e., It is likely not vulnerable and also unpatched with no workaround applied.
If the Server responds with a 400/Bad Request, patched, and if it responds with 404, either the workaround applied, or is not applicable.
Affected Applications in VMware vCenter Servers Under Active Attack 2021
- vCenter Server 6.7 before 6.7u3o and 7.0 before 7.0u2c
- Cloud Foundation 3. x before 3.10.2.2, 4. x before 4.3
Solution
- vCenter Server 6.7u3o for 6.7, 7.0u2c for 7.0
- Cloud Foundation 3.10.2.2 for 3. x, 4.3 for 4. x
SanerNow VM detects these vulnerabilities. We strongly recommend applying the security updates for all vulnerabilities on high priority.