While interacting with Enterprise IT Security Teams, I have come to notice that most enterprises have huge vulnerability backlogs. Thousands of unattended vulnerabilities stall the Month-on-Month progress for the IT Security teams. Primary reason for such backlogs is the disjointed approach to vulnerability management. InfoSec using their tools stack to find vulnerabilities and ITSecOps empowered with their software stack trying to remediate vulnerabilities, pursue an ambitious goal of zero risks Month-on-Month. Most of them, failing to keep vulnerability counts down, end up with thousands of unattended vulnerabilities.
Only the lucky ones do not get attacked. The question everybody is seeking answer to; is it realistic to dream of zero vulnerabilities for an Enterprise IT Security team? Well, it is not as straight forward, though there is a method to this madness. Many Enterprise IT Security teams are achieving the dream of building unbreachable defences. Let us learn how they do it.
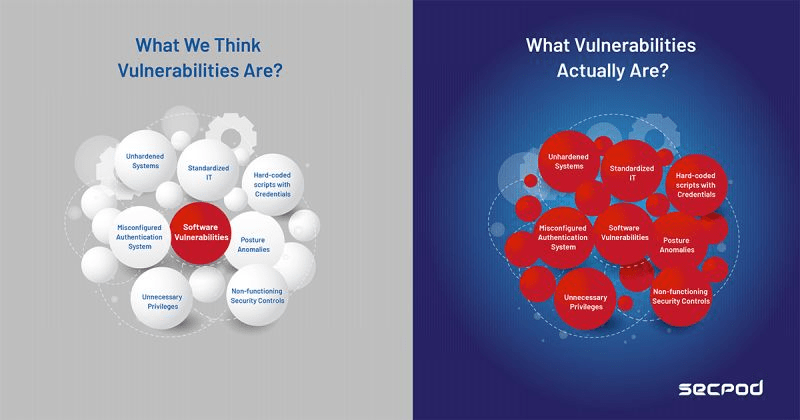
Identifying the Landscape of Cybersecurity Vulnerabilities that Needs Attention
IT Security Teams handling security operations for a large enterprise IT infrastructure face a continuous influx of vulnerabilities. Decades-long implementation of vulnerability management as a practice has resulted in the detection of most of these vulnerabilities in the software or their limitation to the software component of IT.
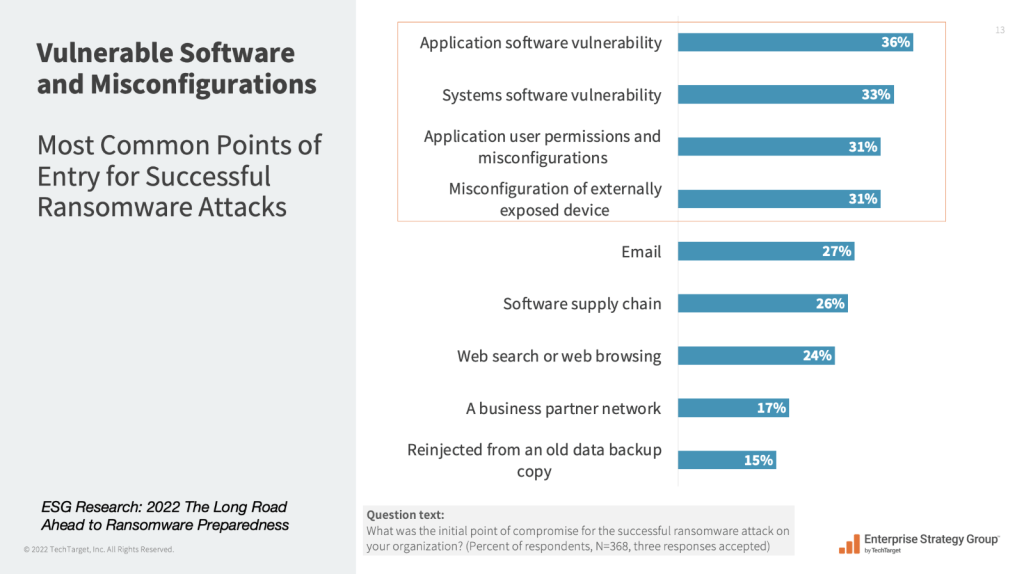
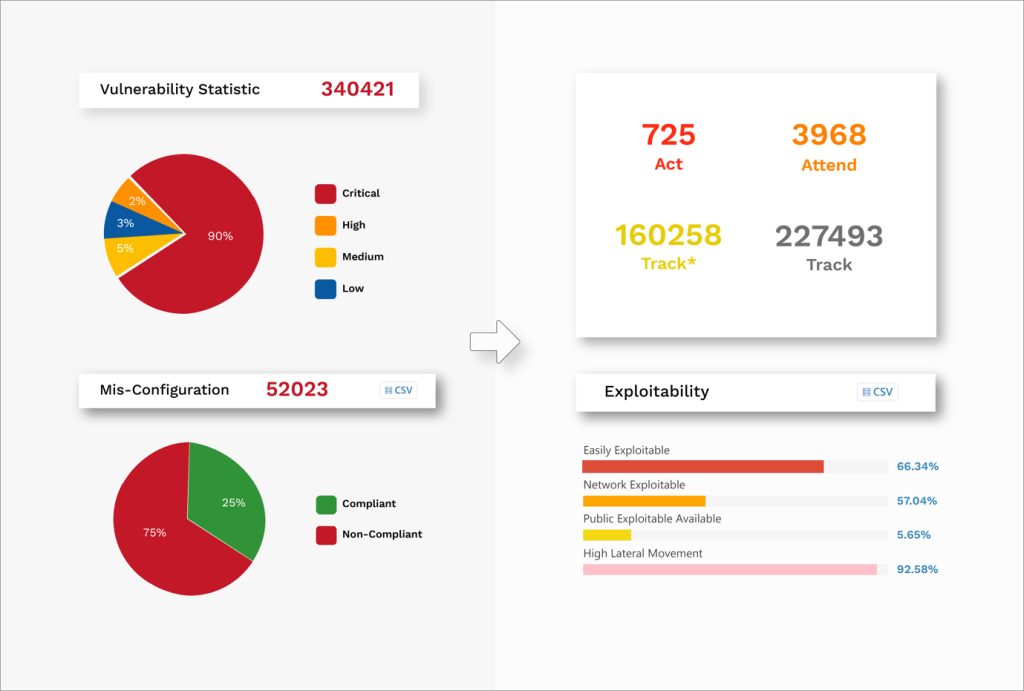
Though the landscape of vulnerabilities extends beyond software component alone. SecPod’s security research reports that, on average, 45% of the total vulnerabilities in enterprise IT infrastructure detect misconfigurations, posture anomalies, missing patches, missing security controls, and more. Thus, extending the vulnerability landscape way beyond software part, which usually go unnoticed and unattended.
Moreover, the software part alone can have vulnerabilities in the range of 10,000 to 100,000 every month in a typical enterprise IT infrastructure. Now, if you take non-software vulnerabilities into account, the number can double. Which would need an army of IT Security professionals to keep in control.
Such a huge velocity of vulnerabilities month-on-month calls for an intelligent approach to managing the vulnerability landscape. A vulnerability management solution, that is continuous, automated, and integrated, is the solution IT Security teams long for.
The Real Challenge: 1 million Vulnerabilities
As an IT Security professional, logging into your enterprise vulnerability management software and viewing the dashboard with over a million open vulnerabilities can be overwhelming. Some of the key challenges enterprise IT Security teams face today:
- Keeping up with the volume of open vulnerabilities
- Automating the process of vulnerability discovery, prioritisation, dispatch to owner and mitigation
- Coordinating vulnerability management process across various tools and teams
- Tracking software vulnerabilities with no available patch or the inability to patch them
The potential risk of not addressing vulnerabilities on time can be extreme. Spanning from increased risk of cyberattacks, t could result in heavy fines, in case the enterprise must adhere to regulatory compliance policies.
Security professionals can gain control over the situation by integrating prioritization and remediation with continuous vulnerability discovery and assessment in a strategic approach. Minimising the volume of open vulnerabilities and keeping a steady flow of remediating on time is a key ask of security leadership. Hence the transformation needed in the enterprise vulnerability management programs is inevitable.
The Three-Week Transformation, Key Learnings and Best Practices
Say what now? Can an enterprise turnaround their state of a 1M open vulnerabilities in just three weeks?
It sounds too good to be true, right?
No, several IT Security teams are today drastically transforming the way they approach this complicated problem. By ceasing to follow their traditional approach and innovating their technology and processes, successful IT Security teams are winning this battle.
The pivotal change that is resulting in their success is how IT Security teams are willing to scrap their age-old technologies and switch over to modern solution that are more integrated and collaborative by design.
What exactly are winning teams doing:
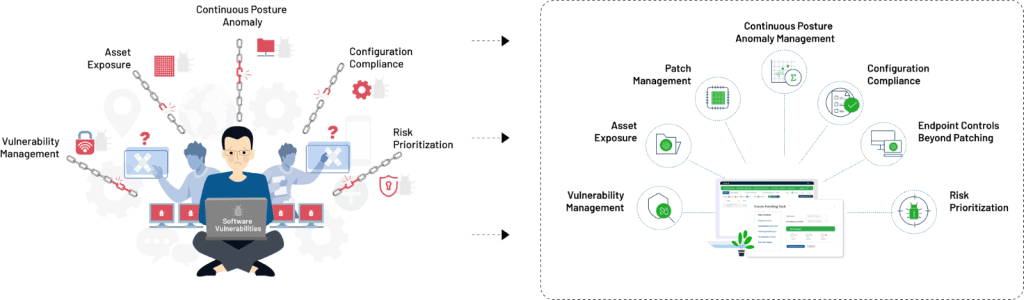
- Continuous discovery and assessment of wholistic vulnerability landscape: Expanding their scans to detect vulnerabilities in the software as well as other components, teams are adding more certainty to their vulnerability detection.
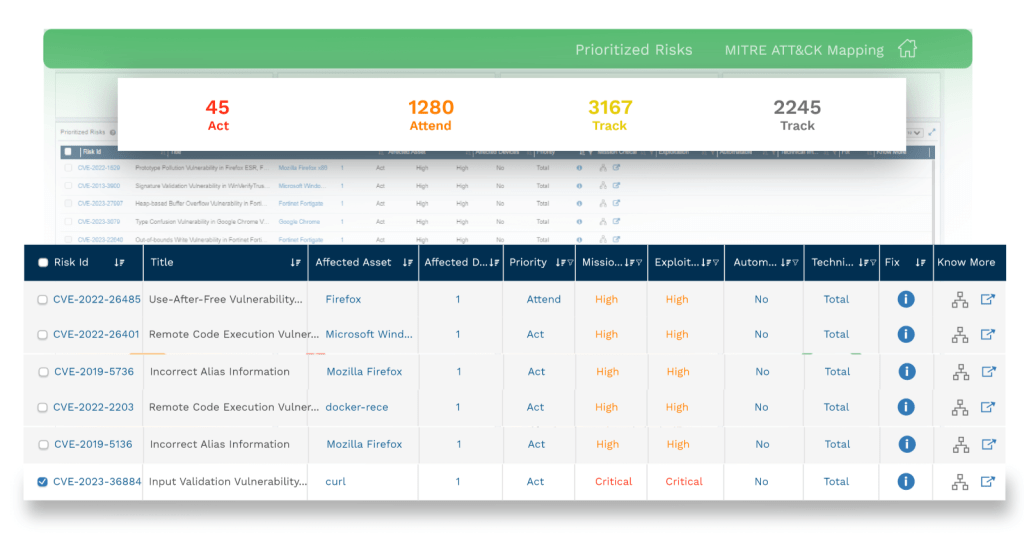
- Prioritisation of critical vulnerabilities: Modern frameworks such as Stakeholder-Specific-Vulnerability-Categorization (SSVC) introduced by CISA offer a categorical definition of what must be treated as critical vulnerabilities and hence the action needed. Such framework helps IT Security teams to create monthly and weekly plans of action for addressing vulnerabilities.
- Collaboration and communication between IT and Security teams: In today’s age of hyper social interaction, if IT and Security teams do not collaborate effectively, they are only pushing themselves back in time. Hence, successful teams put more emphasis on how they collaborate and communicate to resolve vulnerabilities faster.
- Leveraging automation and advanced tools: Automation plays a critical role in the success of this strategy. Automating processes such as vulnerability scanning, patch management, compliance management, incidence response, threat intelligence integration, continuous monitoring can reduce manual effort and make IT Security professionals superhumans.
- Continuous monitoring and evolution: There is a famous saying, “If it is not continuous, it does not work”, which is mostly derived from the success of enterprise IT Security teams that are implementing a continuous approach in their vulnerability management practice and keep pushing forward to innovate their processes.
How to Reduce Vulnerability Counts
Reducing vulnerabilities from 1 million to near zero in 3 weeks may seem like an ambitious and unachievable task. Though, if you get your activities organised into following weekly plan proactively, you can achieve what seems impossible.
Week 1: Discovery and Prioritization
Get all hands on deck. As you implement a vulnerability management solution and have an inventory of devices/assets you need to scan, conduct a thorough vulnerability assessment and prioritization exercise. Inform your risk and compliance teams about the risk the detected vulnerabilities impose on the organisational security. Also, create a schedule for remediation of critical and not-so-critical vulnerabilities based on output of the prioritisation framework.
Week 2: Remediation Planning and Implementation
In the second week, you must start remediating critical vulnerabilities and achieve a zero-critical open vulnerability state. This practice must be fairly achievable. Only thing you need to make sure is that the collaboration between info security and IT operations teams is seamless. For vulnerabilities that do not have a fix or a patch available, create an action plan and assign a project owner to track continuous progress.
Week 3: Testing, Validation and Reporting
Once you finish remediation, in the third week, initiate a test and validation practice. Instruct your quality assurance teams to verify that they have implemented all the fixes well and eliminated vulnerabilities. Generate a joint report showcasing the impact of remediation to both your IT operations and info security teams, so they get a sense of progress. Present the same report to your risk and compliance teams and your leadership, demonstrating the impact.
After you wrap up things in week 3, the key is in repetition and continuity. Set up schedules for continuous vulnerability assessment, prioritisation, remediation, and, reporting.
The Impact IT Security Teams can Create
All organizations care about two things: avoiding attacks and avoiding fines. While the former requires an unbreachable cyber defense, the latter demands strict adherence to regulatory compliance policies. Successful IT Security teams implement impactful programs by utilizing technology solutions that can address both aspects equally.
Following is the impact of such programs:
- Positive outcome of the vulnerability reduction initiatives
- Enhanced security posture and reduced risk for the organisation
- Increased confidence and satisfaction among enterprise IT Security teams
Future Strategies and Continuous Improvement
It’s an imperative to build a continuous vulnerability management practice to avoid losses to cyberattacks and regulatory non-compliance. IT Security teams must take a proactive approach to managing vulnerabilities and keep a steady flow to remediate them within stipulated times. Such an approach guarantees minimal risk and less frustration among teams. To further enhance their impact, IT security teams can leverage artificial intelligence and quantum computing, thereby adding more granularity to vulnerability detection and remediation practices.
IT Security teams must seek continuous innovation in the technologies they use and processes they follow. Seeking new solutions keep them ahead of the cyberattackers.