In today’s rapidly evolving threat landscape, organizations face a constant barrage of vulnerabilities that can potentially expose their systems to cyber threats. To effectively address this challenge, a vulnerability management maturity model becomes essential. And a good vulnerability management tool help structure the framework for organizations to assess, improve, and mature their vulnerability management practices.
This article will outline the various levels of security threats and vulnerability management maturity model.
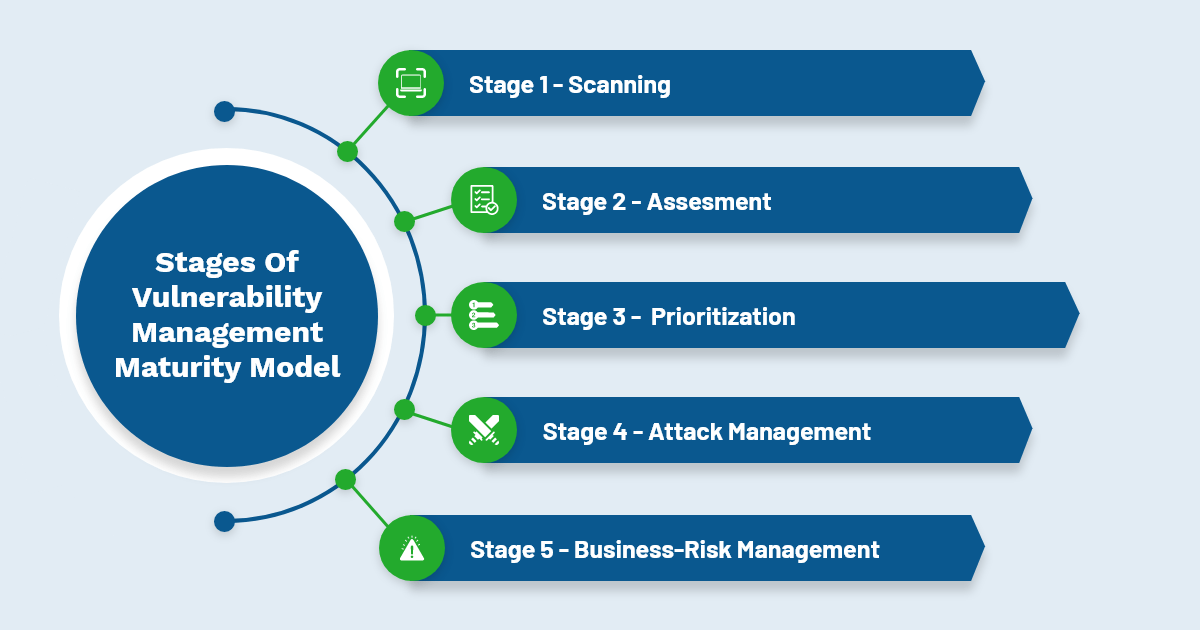
The Vulnerability Management Maturity Model
The vulnerability management maturity model is all about the combination of vulnerability scanning, asset analysis, patch management, remediation steps, and metrics that allow IT Security admins to implement an effective vulnerability management software. It is comprised of five stages leading to an understanding of how your systems will be attacked and exploited along with the technique of countering adversaries.
Stage 0: Non-Existent
This is the developing phase of any security threat and vulnerability management program. Enterprises with no automated vulnerability management software in place perform all the cyber security measures manually. It is not a reasonable approach for any intelligent organization. Patches are implemented on a haphazard basis. And the proactive patching at this level is the only patch Tuesday push every week from Microsoft.
Stage 1: Scanning
Vulnerability scanning is the foundation of your vulnerability management program. It sets specific security considerations and illuminates all the possible cybersecurity flaws in the network. You gain an insight into all the potential weaknesses. With this data, you can shape a strategy on how to handle these vulnerabilities effectively. A scan offers the data; it fails to provide the necessary guidance for what to do with this data.
In the next stage, you will handle these security vulnerabilities effectively. Also, the key strategy includes the industry’s best practices and compliances that every enterprise should comply with.

Stage 2: Assessment
The availability of vulnerability data raises the question of what to address first. Enterprises are overloaded with the scanned data report at this stage, as it is challenging to determine what issues impact the assets. The data is too much but not enough context.
The process of assessing vulnerabilities is designed around various compliance regulations instead of ad-hoc methods. For instance, organizations with requirements of PCI-DSS must perform scans quarterly or whenever major changes occur in the computing environment. The same holds true for patching within a month of patch release.
So, the next move is the advancing of assessment, which is prioritization to decide what security flaws require immediate focus and allocation of IT resources. This needs additional context to determine the right remediation action.
Stage 3: Analysis and Prioritization
A vulnerability management program emerges from a simple program at the prioritization level. Besides, the scanned report and patching process is considered a complete ecosystem rather than a separate entity. Instead of a simple scan and patch technique, a little more advanced and detailed strategy for prioritization. It can be a CVSS scoring system that scales vulnerabilities into critical, high, medial, and low categories. And, it helps to manage high-risk business assets and function effectively
However, both IT operations and information security units should adopt tools and processes, consolidate scanned sources, employ advanced prioritization. As a result, it overcomes the decision-making challenges due to data overload involved during the scanning phase. To further enhance this strategy, organizations can integrate threat modeling that focuses on proactive identification and mitigation of potential threats to a system.
Stage 4: Attack Management
The maturity of the vulnerability management platform is achieved at this stage. Here, the program revolved around mitigating or remediating the critical vulnerabilities. Besides, the focus is entirely towards the attacker and threat-centric, covering all the IT assets and respective computing environments.
At this stage, IT security teams conduct regular penetration testing of high-risk assets, identify assets against known exploits, . This is a back-end process of remediation. Furthermore, the team also leverages various tests to validate the potential threats before and after remediation.
Stage 5: Business-Risk Management
At this point, the security and IT operations teams adopt a risk management framework that focuses entirely on the risk to the business. It offers early warnings about the threats and vulnerabilities that pose risks to business performance. Businesses can make informed decisions to protect IT assets against flaws and attacks.
Vulnerability patch management is a continuous and automated process operating on an ongoing basis. It is integrated into all other information security and IT operations, enabling real-time adjustment of security controls and network and data center management.
Finally, you are responsible for the successful implementation of a vulnerability management tool within your organization. The question is about the program’s maturity model to scan, detect and remediate vulnerabilities. The module only gets better using continuous and automated ways of handling vulnerabilities.
Know more about SanerNow’s Vulnerability Management Maturity Model
SanerNow AVM platform offers continuous and automated vulnerability management solutions to prevent cyberattacks. In addition, the platform performs vulnerability identification, assessment, prioritization processes and helps IT teams with necessary recommendations for remediation.
Further, SanerNow also offers integrated patch management with constant visibility to the computing environment. It identifies security gaps misconfigurations and implements necessary automation techniques.
The platform works on the Agent-Sever model. SanerNow agent continuously scans the entire network in just five minutes and delivers accurate vulnerability data, faster remediation. Besides, the platform houses 175,000+ security checks, which result in a reduced security gap between discovering and remediating flaws. The accuracy of the scanned vulnerability data is very high as the database of large security checks backs it up.
Schedule a demo of SanerNow AVM and know how to strengthen your vulnerability management process. Prevent cyber-attacks using continuous and automated vulnerability management solutions.

