Vulnerability Management, the name itself says it all. We all know vulnerability management is crucial for companies and individuals to follow. But why is it important and what is the workflow each time we try to Kill a vulnerability? Everything we do, either has a ‘Yes’ or a ‘No’, right? The process of knowing which vulnerabilities to remediate and why to do so is all you need to know during the vulnerability management workflow.
Read on to know how a vulnerability management workflow helps you handle a vulnerability.
Cruciality of Vulnerability Management
Vulnerability mitigation is an essential part in all companies, be it a SMB or an enterprise. Effective vulnerability management makes the job of IT and security team much easier. From vulnerability detection to remediation, one vulnerability management tool is all you need!
Not mitigating vulnerabilities and risks in an enterprise leads to a lot of consequences. From data theft to a company’s reputation. Not all vulnerabilities discovered are equally important, some vulns may not even need to be remediated. But the most critical vulns should be prioritized and remediated as soon as possible.
Traditional vulnerability management approaches don’t work well because they are reactive, time-consuming, and prone to human errors. What we need now is a proactive, automated, and streamlined workflow that adapts to the threat landscape your VM process isn’t just about keeping up with the times, it’s about staying ahead of them.
What is Vulnerability Management Workflow? Why does it matter?
A vulnerability management workflow is a step-by-step process of identifying, assessing, prioritizing, and mitigating vulnerabilities in your systems. Think of it as a roadmap that guides you through the entire lifecycle of vulnerability management.
Now coming to the next question – Why does it matter? Because without a clear and efficient workflow, managing risks and vulnerabilities becomes difficult. You’ll miss critical patches and struggle to keep up with constant threats. A well-defined vulnerability management workflow ensures your systems remain secure.
Components of the Workflow
Let’s break down the key stages of an effective vulnerability management workflow:
- Discovery: This is where it all begins. You can’t fix what you don’t know is broken. This phase involves scanning your network, systems, and applications for vulns.
- Assessment: Once you’ve identified potential vulns in your network, it’s time to assess their impact. Not all vulnerabilities are created equal, some pose a higher risk to your enterprise than others.
- Prioritization: With a long list of vulnerabilities, prioritization is key. Focus on the vulnerabilities that pose the greatest risk to your organization first. This involves factors such as exploitability, criticality of vulnerabilities, and the availability of patches.
- Mitigation: Now it’s time to take action. The mitigation phase involves applying patches, configuring systems, or implementing other security measures to reduce or eliminate the risk posed by the vulnerabilities.
- Reporting: Finally, you need to document the entire process and generate reports. These reports are essential for compliance, auditing, and tracking your progress over time.
The Flowchart
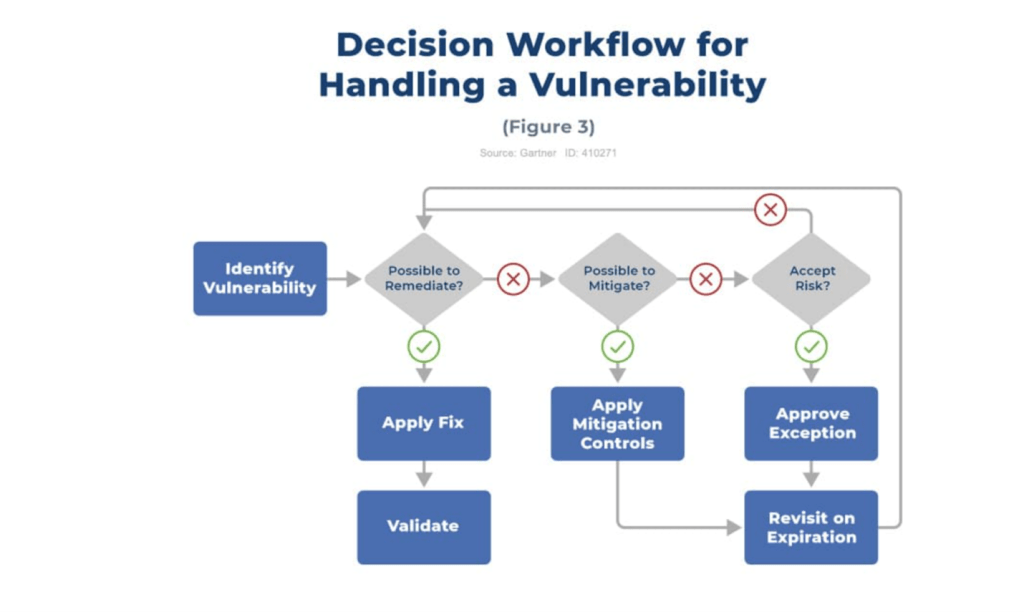
Since we have covered the vulnerability management workflow, let’s talk about the process of handling specific vulnerabilities. Not all vulnerabilities are important and managed the same way, right?
For example, a patch may not be available, or a company may not have enough resources to fix every “medium” vulnerability.
Gartner’s vulnerability management flowchart shows the different decisions you can make when considering remediation.
Conclusion
In a world where cyber threats are constantly evolving, your vulnerability management workflow is no longer optional, it’s essential. A well-defined, automated workflow ensures that you stay ahead of the curve and keep your systems secure. By using SanerNow, you streamline your VM process, reduce the risk of vulnerabilities, and focus on what matters.


