Every security admins’ nightmare is detecting the vulnerabilities lurking within the network. Whether its potentially dangerous malware to hidden backdoor programs with the systems, it is important to discover these vulnerabilities and remediate them using vulnerability management tool. But to carry out this tedious process, we need a tool that performs exhaustive searches.
We all have heard the stories of detectives and their sidekicks working hard, searching clues and finding the culprits. Analogous to that, vulnerability scanners are unsung heroes that detect vulnerabilities and other weaknesses that plague your network.
It is essential to understand how the vulnerability scanners work to prevent emerging vulnerabilities, strengthen security and protect sensitive data.
Now let us gain more insights on vulnerability management software that helps us to avoid potential cyber-attacks.
Understanding Vulnerability Scanning and Vulnerability Scanning Software
What is a Vulnerability? And what is Vulnerability Scanning?
A vulnerability is a security issue or a weakness that can be exploited by a threat actor (think hackers) to perform unauthorized actions within a network and devices. Millions of vulnerabilities are detected every day, and the detection is done using vulnerability scanners.
Vulnerability scanning is a continuous process of using different tools to identify and detect vulnerabilities that affect the endpoints in the network. It is arguably the most important part of vulnerability management because if you don’t know if it exists, how can you eradicate it?
What is Vulnerability Scanning Software?
Vulnerability scanning software(VSS) or simply vulnerability scanners use various tools and methods to identify and detect vulnerabilities in your endpoints. Vulnerabilities are like chinks in the armour, your armour being endpoints. A vulnerability scanning software helps in detecting these weaknesses, and other remediating and patching software clear them up.
Types of Vulnerability Scans:
- External Network Scans:
These scans occur from the outside of the system and they test and identify the vulnerabilities in the system’s perimeter security. The scanners imitate threat actors by simulating their activities. These scans do not need administrative access. They mainly scan servers and applications which are accessible from the internet. - Internal Network Scans:
These scans occur from inside the system and they discover and configure vulnerabilities within the network. They are useful to identify vulnerable devices throughout the network. But an important point to remember is they need login credentials or basically, internal access to the network. Both internal and external scanners work similarly but the direction of scan varies. - Un-Authenticated/Non-Credential Scanning:
These scans are similar to external scans and since they do not have access to internal networks, they try to communicate with different services within the network and gain information by exchanging packets. They help in finding vulnerable open services and frameworks but are not very detailed and comprehensive in detecting vulnerabilities within the system. - Authenticated/Credential Scanning:
These scans are similar to internal scans and they basically need authorized access to get into the network and scan. They are comprehensive and provide detailed information regarding the vulnerabilities within the system. Companies can run these scans for an in-depth inspection of weak passwords, misconfigured databases etc
Read More: Understanding Vulnerability Assessment
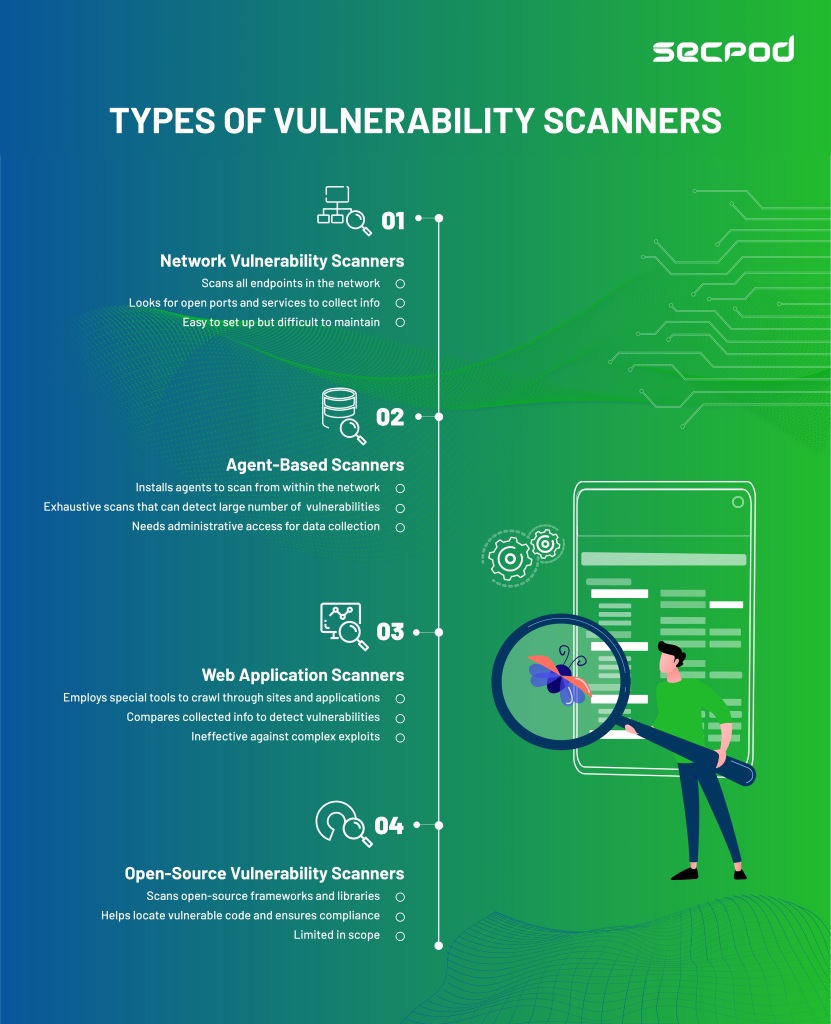
Types of Vulnerability Scanners:
Usually, vulnerability scanners are deployed in the endpoints via different methods(discussed later). They crawl through the endpoints, collecting information regarding potential vulnerabilities and comparing the information with vulnerability databases.
Vulnerability scanners perform a wide array of functions and can be broadly classified into four main types.
- Network Vulnerability Scanners:
Putting it simply, it scans all devices and endpoints across your network. It looks for open ports and services, collects information, and configures any vulnerabilities. They are easy to set up and use but challenging to maintain. When your networks become more extensive, with more endpoints and systems, the number of network scanners increases to scan each network segment. - Agent-Based Scanners:
By installing a lightweight software scanner in your network, they can work from within the system and run vulnerability checks. These agents are connected to a centralized server to report the results. These scanners are comprehensive and can detect many vulnerabilities within the system but need administrative access. Many organizations use cloud-based apps and networks, and agent-based scanners are an excellent fit for the role. - Web Application Scanners:
Web applications are becoming increasingly popular, and the risks and vulnerabilities associated with them have also increased. These scanners are specialized tools that crawl through a site or an application, collecting information and looking for vulnerabilities. These scanners work by comparing the information with a list of known exploits.. They can identify typical weaknesses like SQL injections but are ineffective in detecting complex exploits. - Open-Source Vulnerability Scanners:
Comprehensive scanners which identify vulnerabilities in open-source frameworks and libraries. Open-source codes and libraries are generally used to build everything from scratch, and not a lot of focus is on checking vulnerabilities in these libraries. These scanners can help in locating vulnerable code. They can also help in ensuring compliance with the open-source license.
How do Vulnerability Scanners Work?
All these scanners work with a similar fundamental idea but vary with functionality. They use probes or crawlers to scan through vulnerable codes, open ports, libraries, or deploy agents who perform similar functions. All these tools collect information, run it against a comprehensive database and check for matches in vulnerabilities. For more detailed and thorough scans, they might need authentication.
Why do we need Vulnerability Scanning Software?
Every organization requires robust security, and scanning vulnerabilities becomes an essential part of the security process. Vulnerability scanning software are arguably the most crucial part of a standard vulnerability management program. Vulnerabilities, if ignored, can have a devastating effect on the image of a company, along with the loss of data.
New vulnerabilities are discovered every day, which can have adverse effects on the endpoints in the network, affecting employees’ productivity and results. So, reducing risk by making vulnerability detection a continuous process can become very liberating.
Remember that while 100 percent security cannot be achieved, strengthening and preventing attacks is better than taking measures after it has occurred. And vulnerability scanner is a tool that will help you reach that goal.
Read More: Vulnerability Scanning
Benefits of Vulnerability Scanning Software:
- Achieve Comprehensive Vulnerability Detection:
A vulnerability scanner provides complete visibility over the vulnerabilities in your devices. You can detect the vulnerabilities before attackers do, and prevent exploits before they can create havoc. - Improve speed of managing vulnerability:
With regular and continuous scans, it becomes easier and faster to detect vulnerabilities, aiding you in the vulnerability management process. - Help measure risks and enables faster remediation:
Regular and automated scans can help in measuring and defining the risk level for your organization. It also helps in determining how effective the remediation plan you have incorporated. If same vulnerabilities are detected again and again, you might want to rethink your remediation plan. - Meet Safety and Regulation standards:
Security standards like HIPAA,PCI, and NIST mandate vulnerability detection. Scanners play a crucial role in detecting vulnerabilities and help in aligning those standards.
Challenges In Vulnerability Scanning Software:
- False Positives:
The biggest challenge in vulnerability scanning is the presence of false positives. Detecting a vulnerability that does not have any adverse effect on the network and wasting time remediating it. Real and critical vulnerabilities that might harm the network will create chaos, posing a significant risk in vulnerability management. - Inefficient Prioritization of Vulnerabilities:
Prioritizing detected vulnerabilities based on CVSS scores doesn’t always work for the best. It can’t ascertain the current threat landscape and provides a false sense of security. This can become a significant challenge for a vulnerability scanner . - Duration of Scans:
Vulnerability scans can take up vast amounts of time. The average time could be anywhere between 4-15 hours. And longer scans does not necessarily mean comprehensive. - Risk in internal scans:
Internal scans need credentials for authorized access to probe throughout the internal networks for vulnerability. But this also means that you provide access to a 3rd party application to go through your data. This can pose a risk to the privacy of the company. - Out-of-date Database:
New vulnerabilities are detected every day, and an out-of-date database does not help in detecting and remediating new vulnerabilities in your network. - Need for manual interference:
Complete automation of vulnerability scanning and remediating is an ideal idea. The need for human interference is a must for efficient prioritization and remediation of vulnerabilities.
What Makes a Great Vulnerability Scanning Software?
- Seamless interfacing with patch management software to quickly remediate vulnerabilities is an essential feature to look for in a good vulnerability scanner.
- Fast and precise vulnerability scans are an important feature of a great scanning software. Lengthy scans make the vulnerability management process tedious but scanning must be audit-exercise.
- A great vulnerability scanner should have an extensive repository of regularly updated vulnerabilities. Newly discovered vulnerabilities will not be identified if the vulnerability scanner database is not updated.
- An ideal vulnerability scanner must be aware of false positives and not identify them as vulnerabilities. As said previously, this is the biggest challenge for a scanner. A great vulnerability scanner should find a good balance between reducing false positives and detecting critical and non-critical vulnerabilities.
- Auditing and reporting are necessary, albeit a tedious tasks. So, if a vulnerability scanner can generate solid technical reports which are audit-ready, it relieves a huge burden from the security admins.
Conclusion:
Vulnerability scanning is an excellent way to predict how threat actors can attack your networks. They make up a significant part of the bigger idea called vulnerability management.
It is important to understand that 100 percent protection against threats is not possible, but it does not mean we must not strive to reach that goal. We must never forget that a strong defence is better than a weak response after a cyber-attack.
SecPod SanerNow, which is continuous and automated cyber-hygiene platform handles the complete security of your devices and network, it’s a one-stop solution for all your security problems. Built-in with the world’s fastest vulnerability scans using the world’s largest SCAP repository, SanerNow has over 160000+ checks within 5 minutes to ensure it misses no vulnerabilities. SanerNow also includes integral tools like patch management for automated patching of vulnerabilities providing a one-stop solution for all things cybersecurity.