Alpine Linux is a simple and resource efficient OS which was built based on muscl and Busybox. Due to these optimized features, Alpine Linux behaves as a great docker container.
Security researchers discovered a security vulnerability in the Alpine Linux docker image (since v3.3). Alpine Linux docker image has default root credentials with an empty or null password when it utilizes linux-pam or mechanisms which rely on system shadow file as an authentication database. Obviously, enabling the root login with a blank password is dangerously concerning. However, researchers found and patched this vulnerability, assigned with CVE-2019-5021, in the year 2015. Unfortunately, it was re-introduced in December 2015. You can remediate vulnerabilities like this by using an appropriate patch management software.
What is the Alpine Linux Vulnerability about?
Alpine Linux docker images have an empty or null password for the ‘root’ user when it utilizes shadow or linux-pam packages. Any logged-in non-root user can elevate their privileges to root within the container. However, the non-root user can take full control of the container by elevating privileges to root.
CVSS v3.0 Severity and Metrics:
Base Score: 9.8 HIGH
Vector: AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
CVSS v2.0 Severity and Metrics:
Base Score: 10.0 HIGH
Vector: AV:N/AC:L/Au:N/C:C/I:C/A:C
Affected OS: Alpine Linux Docker image versions 3.3 through 3.9 with shadow or linux-pam installed.
Affected component: Authentication database like System Shadow file (/etc/shadow) or Linux PAM

Are your Alpine Linux container subjected to this vulnerability?
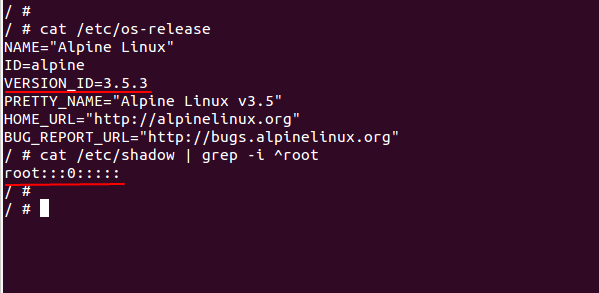
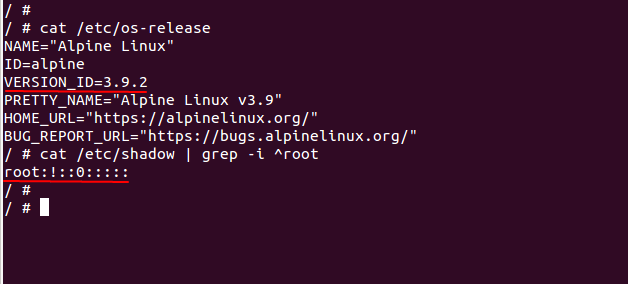
You can identify whether Alpine Linux containers are vulnerable or not by checking the /etc/shadow file in the system. In fact, the container is vulnerable to Alpine Linux Vulnerability if the root password field is empty as shown below,
The patched container has updated /etc/shadow file to include ‘!’ for root user. In the context of the /etc/passwd file, the presence of ‘!’ or ‘*’ for the root login indicates that the root login is locked for editing. On the other hand, if the password field is empty, it indicates that the root login is vulnerable to the attack.
You can use the below shell script to determine whether your Alpine container is vulnerable or not:
#!/bin/bash
var=$(grep -shoP "root:(.*?):" /etc/shadow)
echo $var
var=${var:5:-1}
if [ "$var" == "!" ]
then
echo "System is patched"
elif ["$var" == ""]
then
echo "System is vulnerable"
fi
Mitigation for Alpine Linux Vulnerability:
Upgrade your images to the supported non-vulnerable versions.
Fixes are provided only to the supported Alpine Linux Docker image versions 3.6, 3.7, 3.8 and 3.9. Users who are using vulnerable images can upgrade to the below mentioned patched versions:
- v3.9.2
- v3.8.4
- v3.7.3
- v3.6.5
Workaround:
1) You can mitigate this vulnerability by disabling the root account in the docker images built using affected Alpine versions as a base. To do this, update the /etc/passwd file as shown below, which will disable the root account.
To prevent these attacks from occurring, deploy patches regularly with a continuous and automated patch management software.
root:x:0:0:root:/root:/bin/bash => root:x:0:0:root:/root:/sbin/nologin