You initiate vulnerability scanning in your network, and the scanner spits out an excel sheet with rows and rows of vulnerabilities that never seem to end. You have a colossal task ahead. The task of fixing the detected vulnerabilities identified by vulnerability scanning can be simplified with a vulnerability management software.
You question yourselves, ‘How do I make this easier and faster?’, ‘Where do I start?’ but most importantly,
‘What should I fix first?’
Vulnerability management tool is used in the process of fixing vulnerabilities. But to fix vulnerabilities quickly, vulnerability remediation prioritization is vital.
What are the different methods of vulnerability remediation prioritization?
Vulnerability remediation prioritization is the process of choosing a vulnerability to remediate first based on the data provided by the vulnerability management tool. Ideally, you must remediate all the vulnerabilities in your network, which is neither practical nor feasible in the modern vulnerability landscape. So, we must incorporate various methods of prioritized remediation.
- Prioritized Remediation based on Vulnerability Criticality:
Arguably, it is the most commonly used method of prioritization. A patch fixes a vulnerability, and if the vulnerability is critical, then so is the patch. By correlating the criticality of the vulnerability with the patch, you can exponentially reduce attack surfaces.
Like a top to bottom approach, you can move from the most critical vulnerability to the least critical. This helps remediate vulnerabilities that with the most risk first and ensures your network is protected.
Prioritized Remediation based on Asset Criticality:
In your network, there might be assets that are filled with critical vulnerabilities, which can be a point of entry for attackers, and it is key to fix them first. Assigning a criticality to an asset based on the vulnerabilities present in it and then sorting it based on the criticality with vulnerability management software can be beneficial in swiftly reducing the attack surface.
In your organization, some assets are more important than others, and asset criticality can be perceiving similarly. For example, fixing assets that store sensitive data or performing critical operations is paramount to ensure minimum downtime and reduced risk.
Prioritized Remediation based on Patch:
Many times, a single patch can fix multiple vulnerabilities. It makes sense to apply that patch to your network and remediate many vulnerabilities in one shot. So, by sorting patches based on the number of vulnerabilities it fixes, you can quickly reduce the number of vulnerabilities in your network.
But this method only reduces the number of vulnerabilities and doesn’t consider its criticality. So, if a patch only fixes one single critical vulnerability, you might push to the back of the list, and this is dangerous.
Prioritized Remediation based on Event/Situation
Sometimes a critical vulnerability is discovered, and hackers quickly create exploit kits that can be used to breach devices with the vulnerability. These are known as high-fidelity attacks and are extremely dangerous. It is critical to ensure that your organization is protected from these exploits in the wild. By prioritizing vulnerabilities with exploits, you can swiftly safeguard your network from threats that can potentially cause maximum damage.
So which method of prioritized remediation is most effective?
Answering the question is not straightforward since we must consider many factors, but more importantly, the best method varies among organizations and the context of the threat it faces from the vulnerability.
Based on its size, the number of assets, or functionality, you must choose the method accordingly. So, your vulnerability remediation prioritization method must be flexible when needed too. This is possible with SanerNow patch management software.
Is your Vulnerability Remediation Prioritization Effective?
Effective vulnerability prioritization can enhance your network’s efficacy in combating cyberattacks by improving the velocity of vulnerability management. Consequently, this improves the vulnerability response time.
Ideally, vulnerability remediation prioritization must be quick, reduce vulnerabilities exponentially and eliminate attack surfaces to prevent cyberattacks. If your remediation method can achieve them, then it’s effective.
If your remediation prioritization is quick, can adapt to critical threats spontaneously, and remediate instantaneously, then it’s effective.
Automated Prioritization with SanerNow
SanerNow Continuous Vulnerability and Exposure Management (CVEM) is a revolutionary new way of combating cyber-attacks. It revamps traditional vulnerability management by integrating vulnerability assessment, prioritization, and remediation into a single, smooth, automated process.
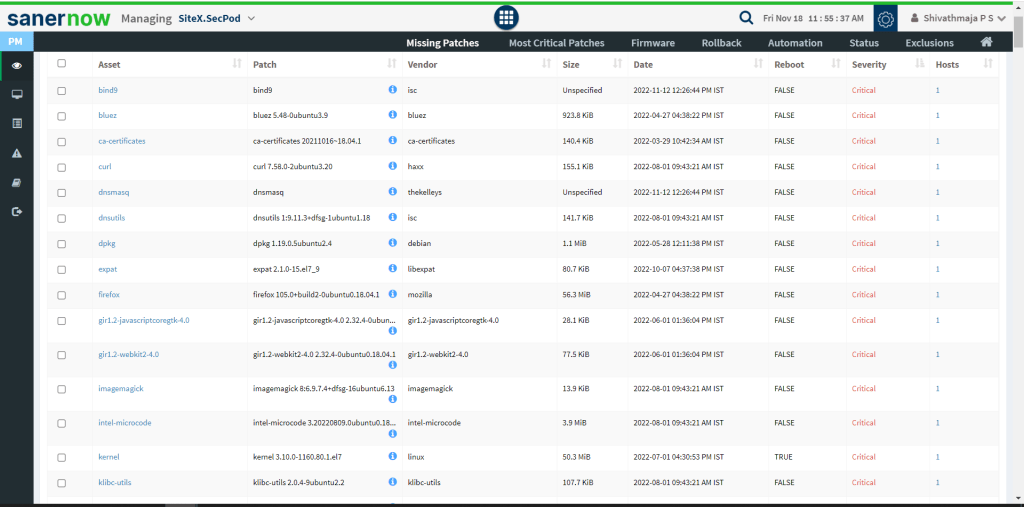
SanerNow has multiple methods of prioritization and provides you with complete control and customization to perform remediation the way you want it. You can categorize and filter out vulnerabilities based on the criticality and availability of exploits and instantly remediate them with integrated remediation.
By automatically prioritizing vulnerability based on its criticality, SanerNow can make your vulnerability remediation prioritization hands-free and simplify the entire process with patch management software.
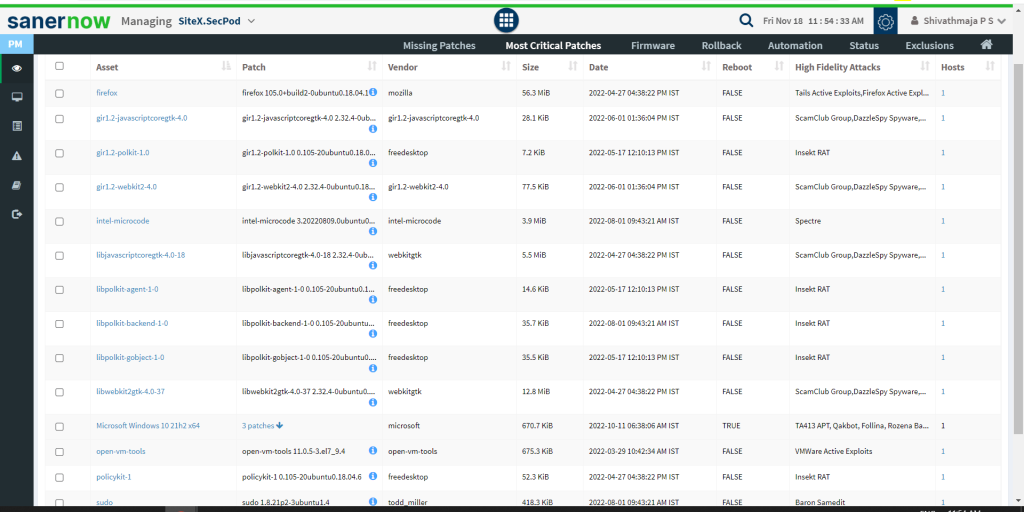
SanerNow can also automatically prioritize vulnerabilities based on the availability of exploits in the wild, aka high-fidelity attacks. This helps you quickly reduce the attack surface and ensure you’re safe and secure.
All in all, SanerNow is a one-stop solution for your vulnerability management needs and preventing cyberattacks.