Microsoft recently patched a critical remote code execution vulnerability in the HTTP Protocol Stack (http. sys). Used by the Windows built-in IIS server for processing HTTP requests. The vulnerability is assigned with an identifier CVE-2021-31166 and has a CVSS score of 9.8. This is a wormable vulnerability and is also said to attack the Windows Remote Management (WinRM) service on the unpatched machines that are exposed to the public. Fortunately, according to the vendor advisories, only Windows 10 and Servers of 2004 and 20H2 are affected by this vulnerability. As a result, only a subset of systems were vulnerable to this attack. Out of the 2 million systems exposing the vulnerable WinRM service online. This can be rectified by using a Vulnerability Management tool.
Vulnerability Details:
The vulnerability came into the picture due to improper pointer tracking when processing the network packet objects used while sending HTTP requests. So the attacker can exploit the flaw by sending a specially crafted packet to the victim server that uses the HTTP Protocol Stack to process these packets. Exploiting this flaw will at least lead to a Blue Screen of Death (BSOD) as HTTP.sys is implemented as a kernel-mode device driver, and in the worst case, it will lead to remote code execution. This RCE is said to be a Wormable Windows HTTP vulnerability CVE-2021-31166 since it can be used to infect multiple systems over the network like a chain reaction without requiring any user interaction. Home PCs are safe from this attack unless they have a vulnerable HTTP Protocol Stack or manually enabled the WinRM service.
The security researcher Jim DeVries found that this would also impact WinRM service apart from the IIS server since it uses vulnerable HTTP. sys The Enterprise edition of Windows has WinRM service enabled by default, whereas Home PCs are safe from this attack unless they have WinRM service enabled or are vulnerable to HTTP Protocol Stack. So the chances of this vulnerability affecting WinRM servers are high in corporate environments. To reduce these chances of attacks, utilizing a good vulnerability management software is advisable.

Proof-of-Concept:
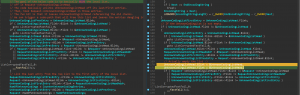
Security researcher Axel Souchet published the PoC for exploiting this vulnerability recently. It also contains a video demonstrating the BSOD after successfully running the script on the targeted system. Below is the code snippet’s image where the bug comes into the picture.
Image Credits: @0vercl0k
The bug actually exists in the http!UlpParseContentCoding function of the code. HTTP!Ulp ParseContentCoding is basically where the parsing of ‘Accept-Encoding’ in the HTTP request header takes place. This function contains a local LIST_ENTRY, a circular doubly linked list used to append items to it. Once the items are appended to this list, it proceeds to the request structure. But it won’t empty the LIST_ENTRY details. The issue occurs when an attacker can trigger a code path to free up entries in this local list. Using CVE-2021-31166, The attacker can make this list empty by freeing each entry in the list, making the entire list dangling in the request object. This causes the LIST_ENTRY to be corruptand the kernel to crash, leading to a BSOD.
Impact
An unauthenticated attacker who successfully exploited the vulnerability can remotely execute arbitrary code on the affected systems or even cause a denial of service (BSOD).
Affected Products
All Microsoft Windows architectures of versions 2004 and 20H2 using the HTTP Protocol Stack (http.sys) to process packets have a direct effect on CVE-2021-31166
- Microsoft Windows 10 Version 2004
- Microsoft Windows 10 Version 20H2
- Microsoft Windows Server, version 2004 (Server Core installation)
- Microsoft Windows Server, version 20H2 (Server Core Installation)
Solution
Microsoft has released a security fix in its monthly Patch Tuesday updates for May 2021. Apply the respective KB to the related OS.
SanerNow detects these vulnerabilities and automatically fixes them by applying security updates. We strongly give a recommendation of applying the security updates as soon as possible. Following the instructions publishing in our article, the support article .