Contact Form 7 is a popular WordPress plugin that is used to create, customize, and manage multiple contact forms on WordPress sites. A critical file upload vulnerability (CVE-2020-35489) has an identity in the WordPress Contact Form 7 plugin, allowing an attacker to execute arbitrary code on affected WordPress sites. Contact Form 7 is a very popular WordPress plugin and is currently on more than 5 million active WordPress websites. This can be prevented by using a Vulnerability Management Software.

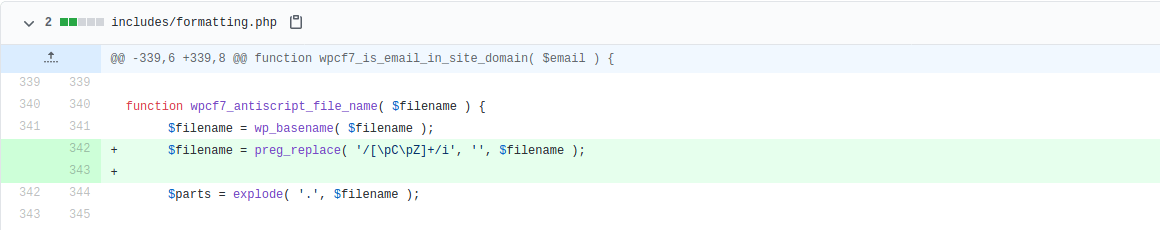
This file upload vulnerability exists in the formatting.php file in the WordPress Contact Form 7 plugin and its identification is CVE-2020-35489. The Contact Form 7’s filename sanitization protection does not validate the filename for special characters (like invisible separators, control characters, or any kind of whitespace). They are additionally allowing attackers to upload files of any type and execute arbitrary code. The validity check for the removal of such unique characters is provisional as part of the solution to this vulnerability in the below figure:
Affected Versions
The vulnerability affects WordPress Contact Form 7 plugin versions 5.3.1 and prior.
Note: The installation of sites having Contact Form 7 without the file upload function is not vulnerable.
Impact
- An attacker can upload a web shell and inject malicious scripts.
- An attacker can execute arbitrary code and completely take over the website.
- An attacker can compromise the web server also.
- An attacker can put a phishing page into the website and deface the website.
Solution
Finally, this vulnerability has a fix. Update the WordPress Contact Form 7 plugin to version 5.3.2 or later.
Fixing these vulnerabilities is easier with a patch management software.