A critical Linux kernel vulnerability 5.15 was found in SMB servers with KSMBD enabled. KSMBD is a Linux kernel server that implements SMB3 protocol in kernel space for sharing files over the network. The vulnerability is assigned with CVE-2022-47939. Remote attackers are able to execute code on vulnerable Linux Kernel systems without any authentication. This can be prevented by using a Vulnerability Management tool.
The vulnerability was discovered on July 26, 2022, by Zero Day Initiative (ZDI), a zero-day security research firm and the flaw was publicly disclosed on December 22, 2022.
ZDI says SMB2 TREE DISCONNECT command processing is where the exact fault is located. The problem arises from the failure to confirm an object’s existence before conducting actions on it. This flaw allows an attacker to run code within the kernel context.
What is KSMBD?
In 2021, the Linux kernel version 5.15 (CVE-2022-47939) released a new module called “KSMBD“, which was developed by Samsung that provides an SMB server. It is intended to be a low overhead, low footprint, a performant file server that can handle many common use cases and run on smaller devices with constrained resources.
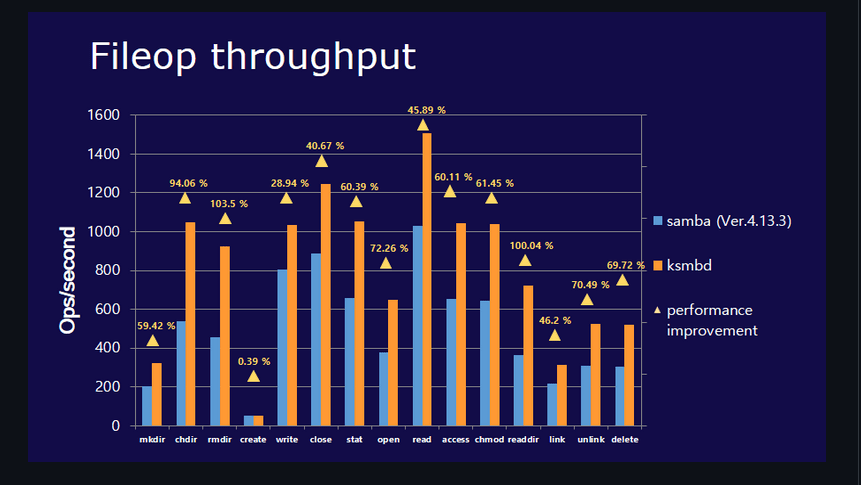
KSMBD claims to have improved performance on a variety of benchmarks, as discussed in the article KSMBD: a new in-kernel SMB server. The below graph demonstrates a doubling of the performance test. There was also the idea that an in-kernel server is probably a simpler place to enable SMB Direct, which employs RDMA to transport data between systems.
KSMBD vs samba performance comparison using fileop (Linux Client)
Is SMBD also affected?
As per Jeremy Allison, Samba’s co-creator, KSMBD was built entirely from scratch and has no code in common with production Samba. In other words, the Samba file server you could be running on your PCs has nothing to do with the current scenario. Overall, the team notes KSMBD will eventually integrate with Samba. The Samba developers at SerNet are eager to work on and with KSMBD.
Impact
Successful exploitation allows attackers to execute arbitrary code.
Affected Product
Any distribution using the Linux kernel 5.15 or above is potentially at risk. For example, Ubuntu 22.04, and its descendants, Deepin Linux 20.3 and Slackware 15, use this kernel. On the contrary, the Red Hat Enterprise Linux (RHEL) family does not use the 5.15 kernel.
Solution
Linux Kernel 5.15.61 or later versions
Therefore, use SanerNow and keep your systems updated and secure.