Some facts before you read further:
1) Zoom client installed on 4 million Mac computers worldwide.
2) Zoom client on mac can let an attacker connect you to a video call without your consent.
3) 4 million Mac users worldwide forcibly connected to a video call without their approval !!
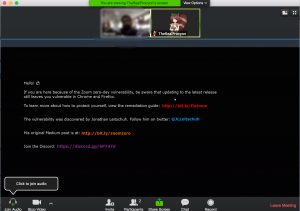
Zoom Client on Mac is vulnerable to drive-by compromise. A malicious website used to join a user to a zoom call without his permission. A vulnerability management solution can solve this problem. The user also made a part of a video call forcibly. This vulnerability reported by a security researcher Jonathan Leitschuh. Considering the fact that zoom has a huge customer base around the world, this is a serious threat to millions of users.
Using patch management tool, we can patch this vulnerability in all mac devices.
Technical details:
The three features that made ZOOM zoom in on your computers:
1) Zoom has a functionality of allowing users to join a call by just opening a meeting link in a browser. Any link to a website embedded with bare minimum parameters “action=join” and “confno=conference number” is sufficient to join a video call. This custom link feature can be abused by websites by inserting a zoom conference link as an <iframe> in the site’s code. This included as a part of phishing or malware advertisements too.
<img src=“http://localhost:19421/launch?action=join&confno=492468757“/>
<iframe src=“https://zoom.us/j/492468757“/>
2) Another functionality in Zoom allows a user to connect automatically to the participant’s video.
3) Zoom installs a local web server along with the desktop application. This server is running even when zoom uninstalled. You can confirm this by running lsof -i :19421 on your mac terminal. That’s not all, the web server also re-installs and updates the application on the machine.
More Technical details:
When a user tries to connect to a call using a link, the web page loads an image from the Zoom web server instead of regular AJAX requests. On close analysis, it was revealed that some data encoded in the dimensions of the image. The server status codes returned determined by the dimensions of the image which is strange enough. But, a possible explanation for this type of encoding is to bypass the CORS.
The code in the web server API has a list of trusted domains to access the URL : https://domain/upgrade?os=mac . When one of these is accessed, it returns data the download and reinstall of the zoom application. The researcher points out if any of the domains compromised and hosted with malicious Zoom installers, every user who uninstalled zoom from the machine replaced with a malicious version of the application ultimately leading to Remote Code Execution.
Thus, an attacker can forcibly join a user to a call with his video feed activated, even if the zoom application uninstalled on the machine.
Here are the good tidings. Zoom has handled these issues in its new patches for CVE-2019–13450 :
- A web server functionality discarded for mac. The local web server running on the machine entirely removed once the application updated.
- Users can uninstall zoom and the webserver completely with just a click.
However, the researcher brings out his disappointment in a write-up and points out that the vendor was inert to the numerous requests made by the researcher to resolve the issue and repeatedly issued lazy fixes for the flaw which could be easily bypassed.
Affected Applications :
Zoom Client version4.4.53932.0709 and earlier on MacOS are vulnerable.
Solution :
Please refer to this KB article.
NOTE: Apple has also pushed out silent updates to remove the webserver. This was particularly helpful for those users who had uninstalled their zoom applications but not the webserver.