Patch Management Essentials
Patch Management Best Practices
Are you wondering if there are any patching best practices that can make your patch management tool effective?
Patching plays a vital role in preventing cyber-attacks! Just having a patch management process in place won’t be helpful.
Every organization must follow specific patch management best practices and apply patches to the right applications at the right time.
There are many patching best practices that can help organizations attain a perfect security posture using the top patch management software.
The top 9 patch management best practices
Maintain up-to-date software inventory:
A complete inventory of all assets in your organization’s environment is essential. You can’t protect what you cannot see!
Therefore, it should be a routine to have an up-to-date inventory in every organization.
Categorize your assets based on software, hardware, version, manufacturer, and operating system. This will help you know which assets would need your special attention, and you can focus on patching them immediately.
Automate patching:
It’s one of the vital patching best practices. On average, it may take weeks or months to patch a vulnerability once detected.
Always use automated patch manager since scanning and deploying missing patches is tedious.Automating the entire patch management software will reduce human error, saves time, and helps in keeping track of vulnerabilities and respective patches and deploying them on time.
Patch management policy:
Deploying patches randomly can make you miss out on any most-critical patch.
Develop a patch policy that explains when the system should be patched and which patches are given priority.You can start creating a patch management policy by listing down steps followed during the patch management process and any strategic plans to carry out patch management smoothly.
For instance, there are times when specific systems would need special attention compared to others. During these circumstances, a patch policy should know what action needs to be taken.
Regular patching:
What do you think will happen if you delay applying patches?
In this modern IT landscape, vulnerabilities are detected daily! Periodically scanning your organization’s network is not at all practical.And if the time taken to deploy patches is longer, your organization will definitely be vulnerable to cyber-attacks. You can achieve faster patch deployment by speeding up patch discovery and automating deployment and patch downloads.
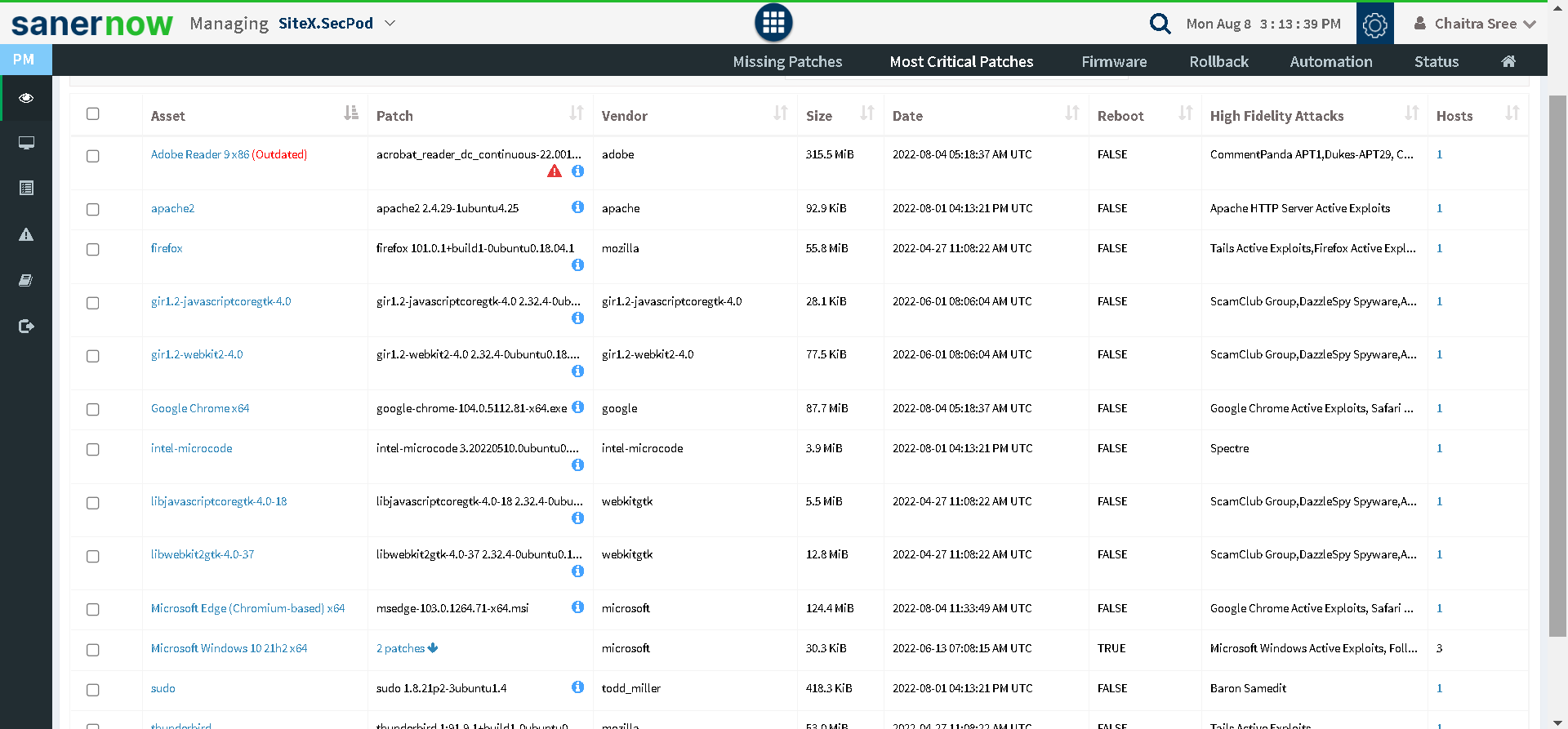
Prioritize patches:
Another patch management best practice is to prioritize patches based on severity and CVSS (Common Vulnerability Scoring System) scores.
But just looking at the CVSS score will not give you a clear picture of how to prioritize vulnerabilities. Other factors are worth considering, such as exploitation level and the potential of high-fidelity attacks.Prioritizing patches will be helpful when you encounter a bunch of patches without any idea about their deployment order. It is inadequate to follow random order of patching.
Third-party application patching:
Third-party applications are common in every organization. Different vendors maintain the third-party application and have their own schedules to release patches.
To ensure you are up to date with the latest patches, one can subscribe to all their security updates and download them as soon as they notify you, but it is not exactly considered patching best practice.A few tools will automatically download all third-party applications, non-security and security patches; try using them.
Test and deploy patches:
It is one of the most crucial patch management best practices. Create a test environment similar to your production environment and deploy patches in a test environment to see what impact it will cause.
Allocate proper time to test your patches for adequate functionality before deploying them in the production environment.
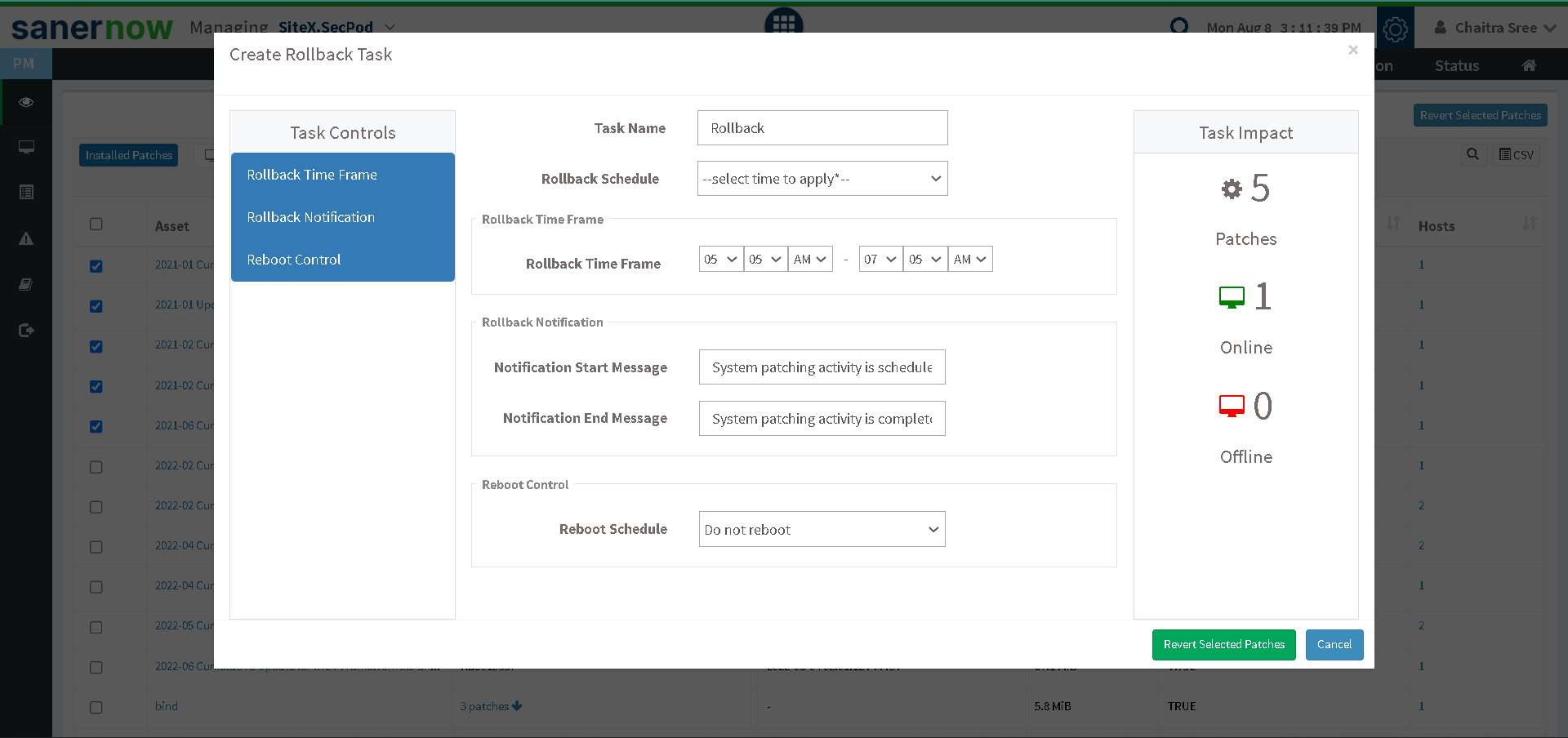
Have rollback planned:
There will be a few circumstances where non-security and security patches, even after testing, would prove incompatible.
To overcome them, a patch rollback planned would remove the latest patches and provide you with the previous stable version.Integrate patch management with vulnerability management:
Using different patch and vulnerability management tool can sometimes be complex.
Scan results of one device should be linked with available patches from another tool; this process is not quite adequate.
These are the few best practices your organization can follow, or you can choose the right tool to perform the entire patch management process effectively.
Benefits of SanerNow patch management
1. End-to-end Automation:
SanerNow patch management tool is entirely automated. You can schedule patches daily, weekly, or monthly without user interruptions.
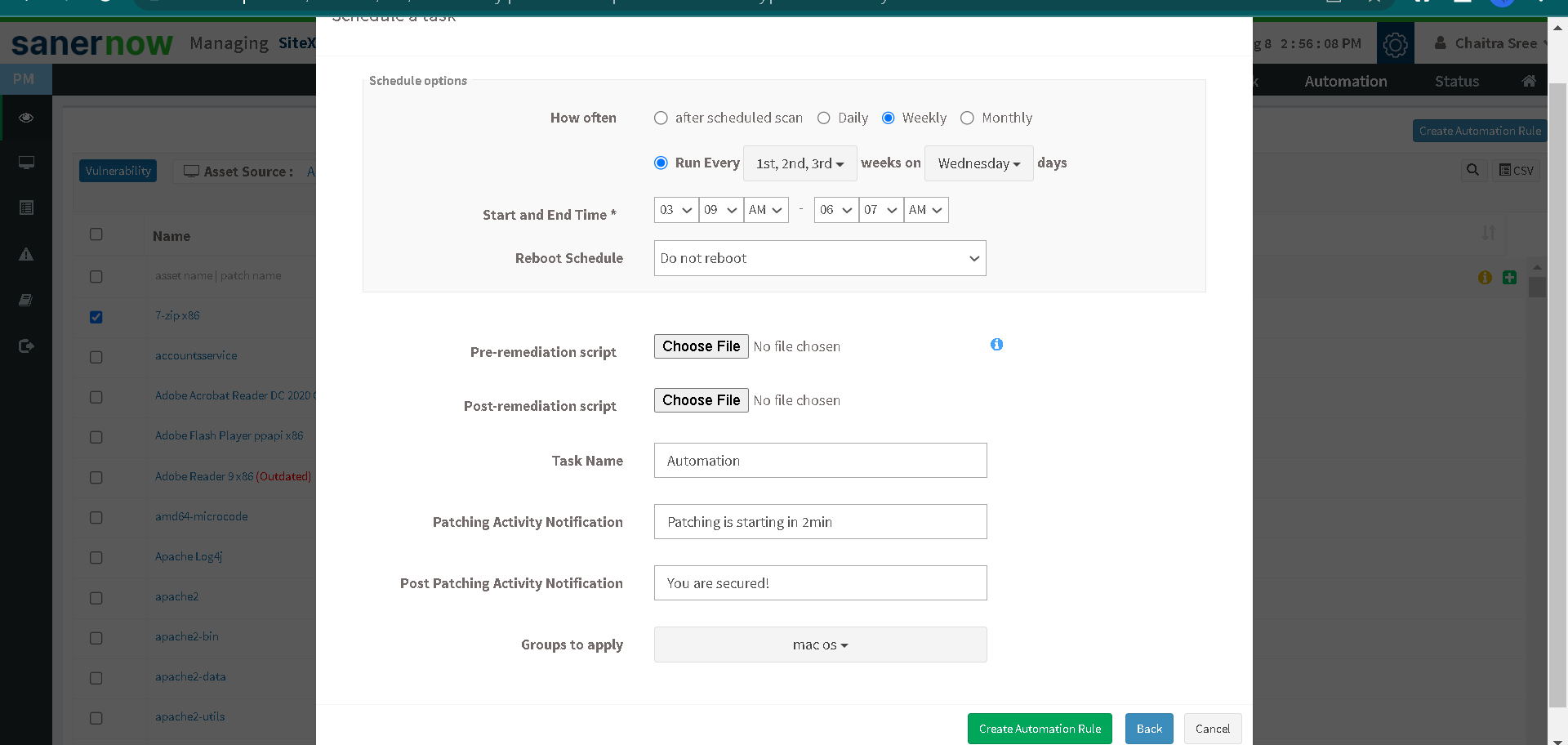
2. Prioritization based on CVSS:
Based on patch severity levels and CVSS scores, SanerNow automatically prioritizes patches.
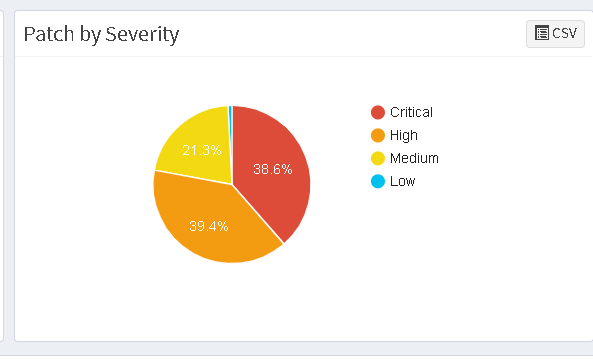
3. Integrated solution:
Patch management is integrated with vulnerability management tool, giving you a clear picture of patches that apply to their respective device.
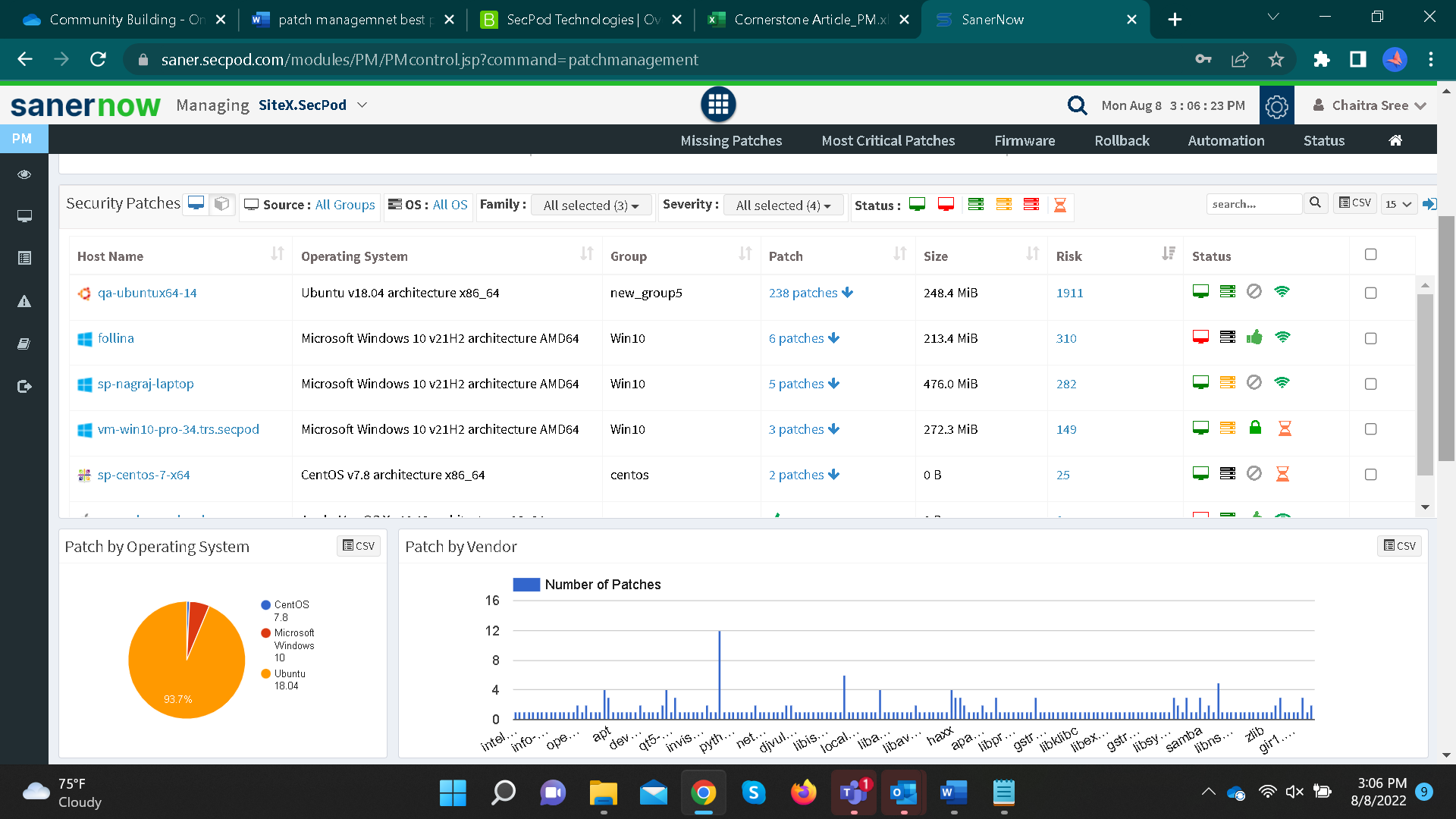
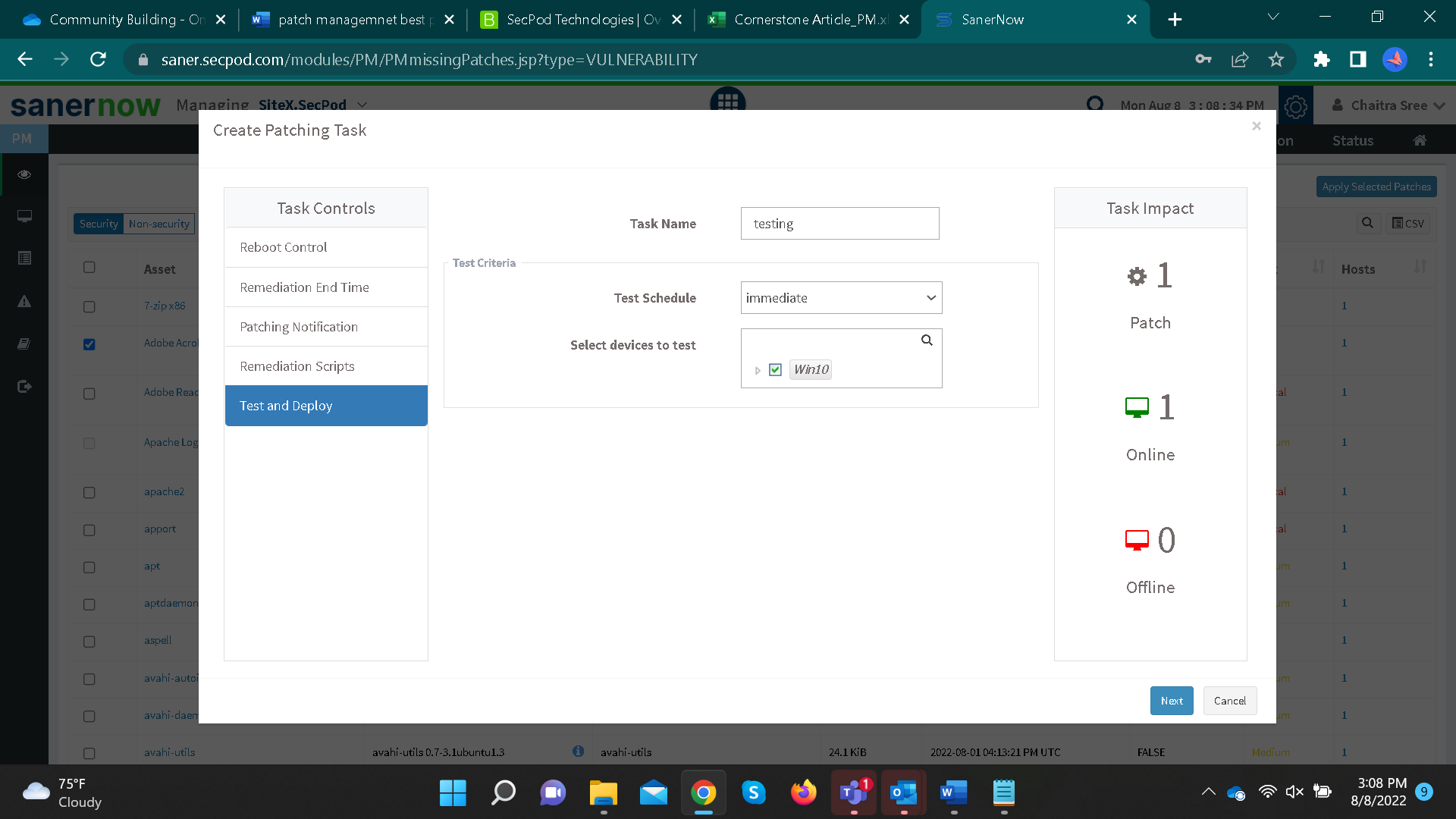
4. Test and deploy:
SanerNow allows you to test the patches in a test environment before deploying them in your live environment.
5. Patch rollback:
SanerNow supports a rollback feature if any patches fail or if you want to have previous versions of any application. You can also schedule rollback based on your preferred timing.
6. Third-party application patches:
With SanerNow, you don’t have to worry about downloading third-party application patches. The patch repository will store all downloaded third-party application patches.
Look out for a tool that can provide you with integrated patch management and vulnerability management platform where you can instantly remediate them


