SanerNow Solution for
Risk-based Asset Discovery & Normalization
To gain clarity of large asset portfolios, discover & remediate attack vectors


A Terrific And Powerful Vulnerabilities Assessment And Patching Platform
SanerNow is a very powerful security platform that is user-friendly and robust. My overall experience is positive. I love the GUI is easy to navigate and provides easy insight into our patching status. Vulnerability detection is fast, the implementation in the cloud which is secure and accessible anywhere and good automation processes to detect vulnerabilities easily makes it perfect for our daily uses.
– Assistant System Administrator, 500M+ USD Firm





Improve Asset Visibility. Gain Maximum Control over IT Environment.
Manage IT Infrastructure At Scale
On-demand asset discovery across all endpoints across enterprise infrastructure, identify any changes in assets, track removal & installation of hardware components or software applications, including licenses. Monitor software usage metrics to measure software performance.
Ensure Sanity In System Behavior
Use rule-based outlier detection and more than 100 device artifacts to uncover any posture anomalies, categorize anomalies based on context and keep only those which are within acceptable limits.
Establish Cyber Hygiene
Authorize and approve security controls based on how they are configured, identify deviations, and remediate any anomalies to maintain cyber hygiene.
Secure IT Environment
Visualize enterprise IT infrastructure as one entity and detect insecure ports, default credentials, anonymous logins, guest logins, unapproved VPN connections, file sharing apps, attack vectors to implement maximum protection.
Assess Device Security Gaps. Remediate Security Anomalies with Ease.
Improve Device Security Management
Whitelist devices and configurations across IT infrastructure, analyze security controls, from disabled firewalls, outdated OS or software, disabled Bitlocker, to over 2000+ device parameters and get insightful information on security posture with over 75+ anomaly computation rules.
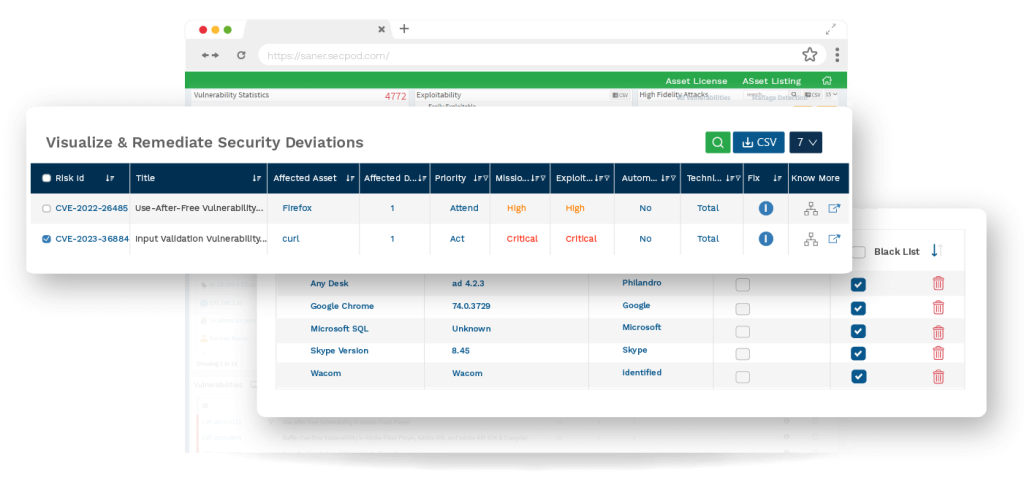
Visualize & Remediate Security Deviations
Evaluate security posture with insightful visualizations, derive data from performing outlier analysis, generate custom visibility using APIs, create own detection rules to find anomalies, and remediate them quickly from a centralized console to secure IT infrastructure. Discover unknown security risks and monitor security controls for any functional abnormalities.
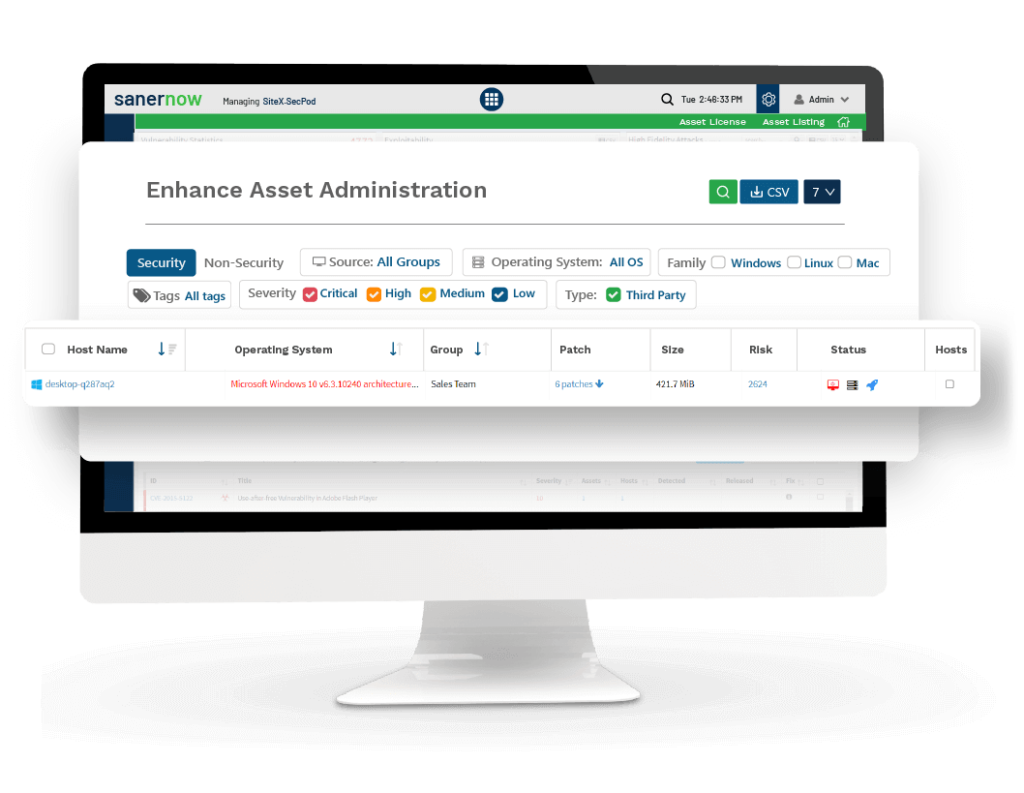
Enhance Asset Administration
Manage IT inventory in real time by getting comprehensive view of large hardware and software asset portfolios with high-speed full automated scans, take data driven decisions based on inventory data available through insightful dashboards, track how assets are used and manage any vulnerable assets to reduce risk exposures.
Prevent Shadow IT
Detect & decommission unsanctioned IT assets, which include software, hardware, and any device or tool used without enterprise IT approval deployed in the network to prevent security risks.
Strengthen Security Controls
Guarantee the functioning of security controls by fixing any deviations in them, ensure only authorized control are at work across systems and they are configured to meet the security policy standards.
Take Real Time Security Decisions
Streamline security operations by getting intelligent, actionable insights on security loopholes and hidden risks and act on them to prevent cyber-attacks.
Sustain Risk Tolerance Limits
Meet acceptable deviations from risk appetite by have the right controls in place and by deeply understanding IT environments to gain clarity and confidence in security posture.
Prevent Security Breaches
Remediate attack entry points by proactively discovering attack vectors and declutter IT infrastructure by eliminating unauthorized hardware and software assets to reduce attack surface.
Solutions Crafted for Asset Discovery and Normalization
Understand how SanerNow Continuous Vulnerability & Exposure Management (CVEM) can effectively remediate risks and protect organizations from devastating cyberattacks.
HIGHLIGHTED CASE STUDY
Digital Banking Services Provider Achieves Instant Visibility of Risk Posture to Rapidly Remediate Risks, and Achieve Continuous Compliance
A Leading Digital Banking Service provider was looking for a vulnerability management solution to transform their IT security from a traditional security approach.
Continuously Examine Security Posture by Discovering Unknown Security Risks
Request a product walkthrough demo with one of our solution experts.